Attackers Can Bypass Windows Security Using New DLL Hijacking Technique Threat actors using the DLL Hijacking technique for persistence have been the order of the [...]
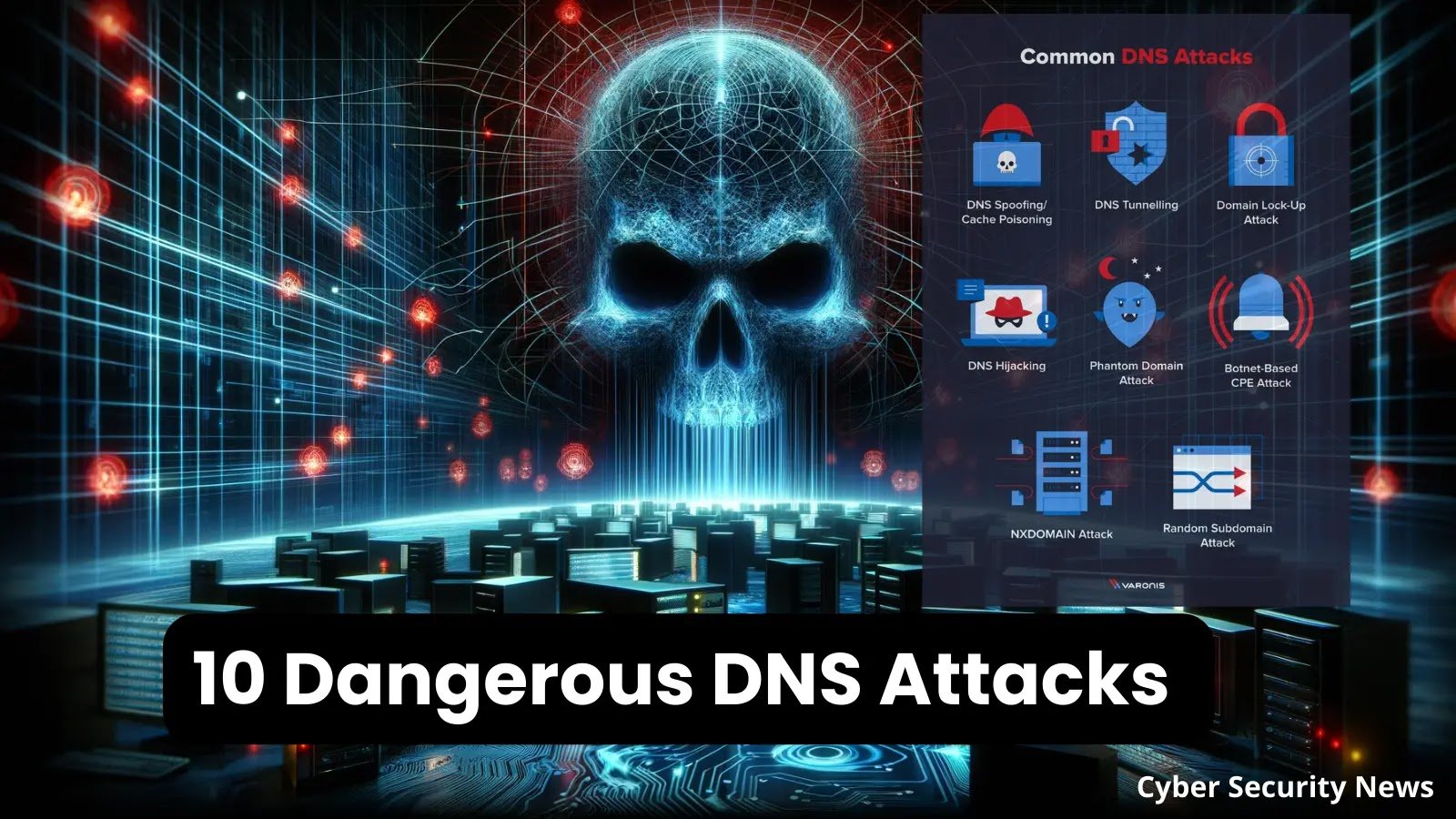
10 Dangerous DNS Attacks Types & Prevention Measures – 2024 Our topic for today seems to be centered around the most common 10 DNS attacks and how [...]
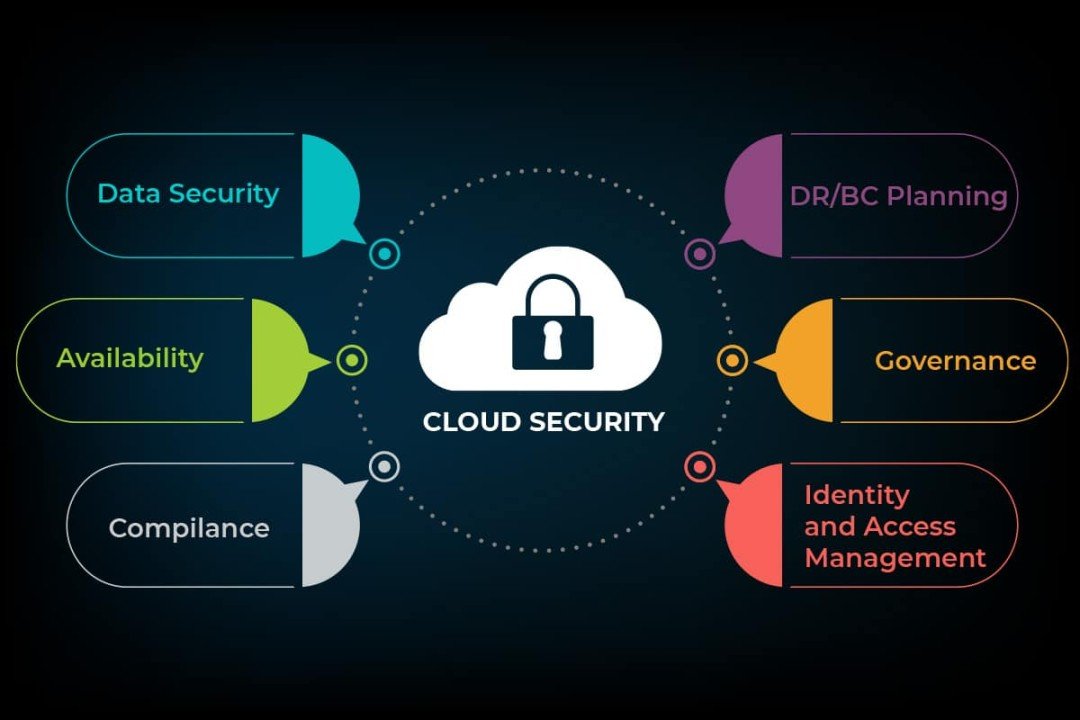
Unveiling the Secrets of Cloud Security Layers Cloud security is a critical aspect of modern computing, considering the widespread adoption of cloud services for data [...]
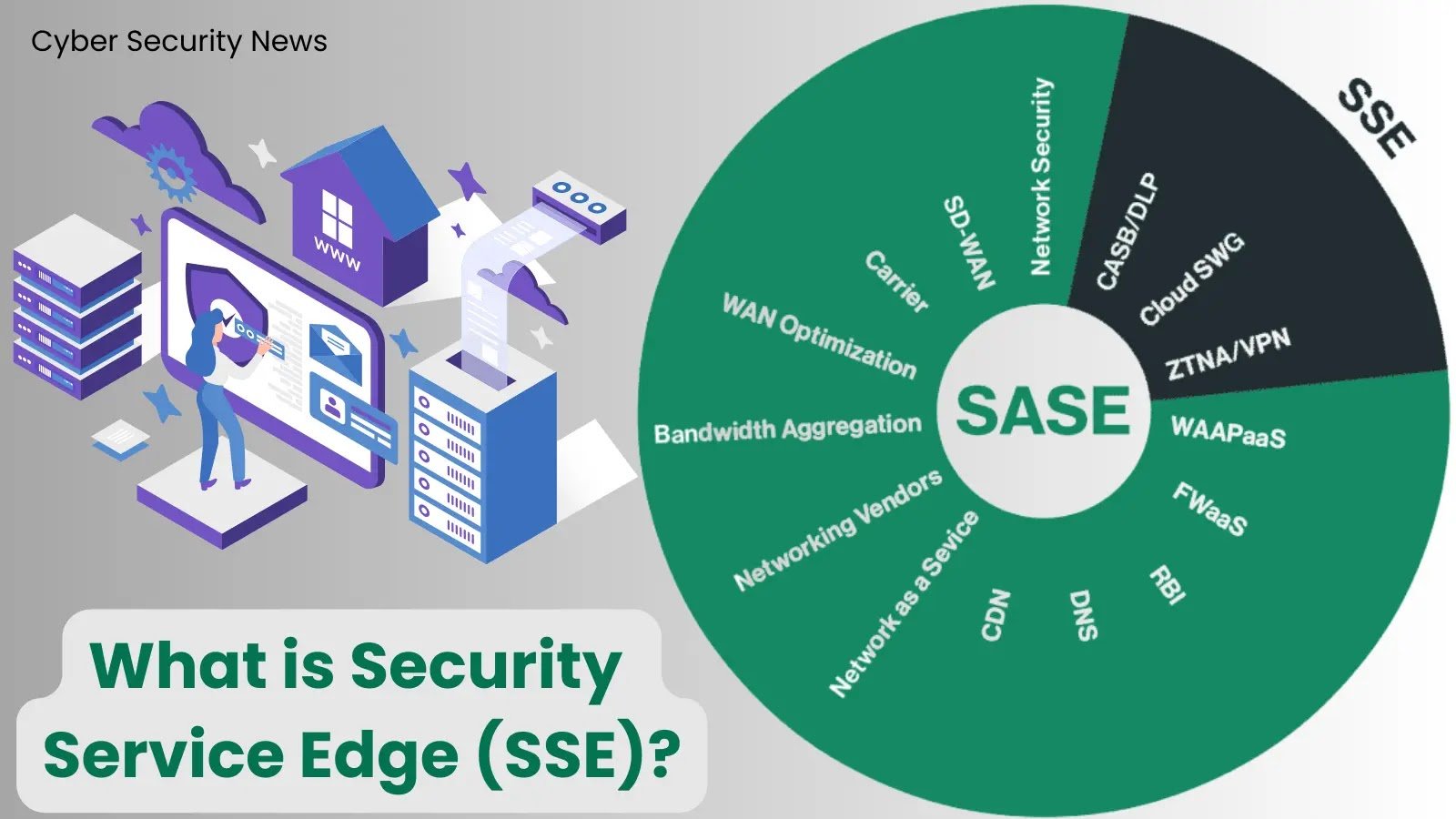
What is Security Service Edge (SSE)? – Revolutionizing Hybrid Work Security in Direct Cloud Access The contemporary work landscape is swiftly transitioning into a hybrid [...]