The Future of Data Security in the Cloud: Trends & Solutions Data security in the cloud is a dynamic and evolving field, shaped by technological [...]
Exploring the Rise of IoT in Corporate Network Infrastructure The rise of the Internet of Things (IoT) is fundamentally transforming corporate network infrastructure, introducing a [...]
The Future of 5G in Enterprise Networks The future of 5G in enterprise networks holds immense promise for revolutionizing how businesses operate and communicate. Here [...]
What is the Different Between VPN and Proxy Even though they handle data in slightly different ways, virtual private networks (VPNs) and proxies both help [...]
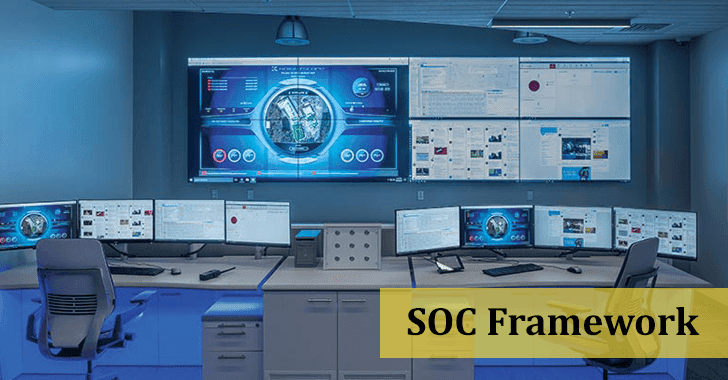
What is a SOC Framework, Elements & Benefits of Security Operation Centre If a company is serious about cybersecurity, its beating heart will be the Security [...]
The Evolution of Firewall Technology in the Digital Age The evolution of firewall technology in the digital age has been marked by continuous adaptation and [...]
9 Essential Cybersecurity Tips For New IT Technicians Picture yourself at the helm of a company’s cyber defenses—stakes are high, and your moves are critical. [...]
Emerging Trends in Structured Cabling Technology Structured cabling technology, the backbone of modern IT infrastructure, continues to evolve to meet the increasing demands of high-speed [...]
Multiple Fortinet Vulnerabilities Let Attackers Execute Arbitrary Code Multiple vulnerabilities have been discovered in FortiOS and FortiProxy that were related to administrator cookie leakage, arbitrary [...]
Multiple Palo Alto Networks Firewall Flaws Let Attackers Cause Disruption Palo Alto Networks has recently disclosed four high-severity vulnerabilities in its firewall products. If exploited, [...]