Cisco to Acquire AI Application Security Platform Robust Intelligence Cisco has announced its intent to acquire Robust Intelligence, a leader in AI application security. This [...]
What is an Access Control Lists (ACLs)? Access Control Lists (ACLs) are fundamental to network security and management. They are critical in determining who or what [...]
Multiple Vulnerabilities in AI Platforms Exposes Sensitive Data to Anyone Artificial intelligence (AI) platforms have become integral tools for businesses and organizations worldwide. These technologies [...]
AI Model Achieve 98% Accuracy in Collecting Threat Intelligence From Dark Web Forums In a recent study, researchers from the Université de Montréal and Flare [...]
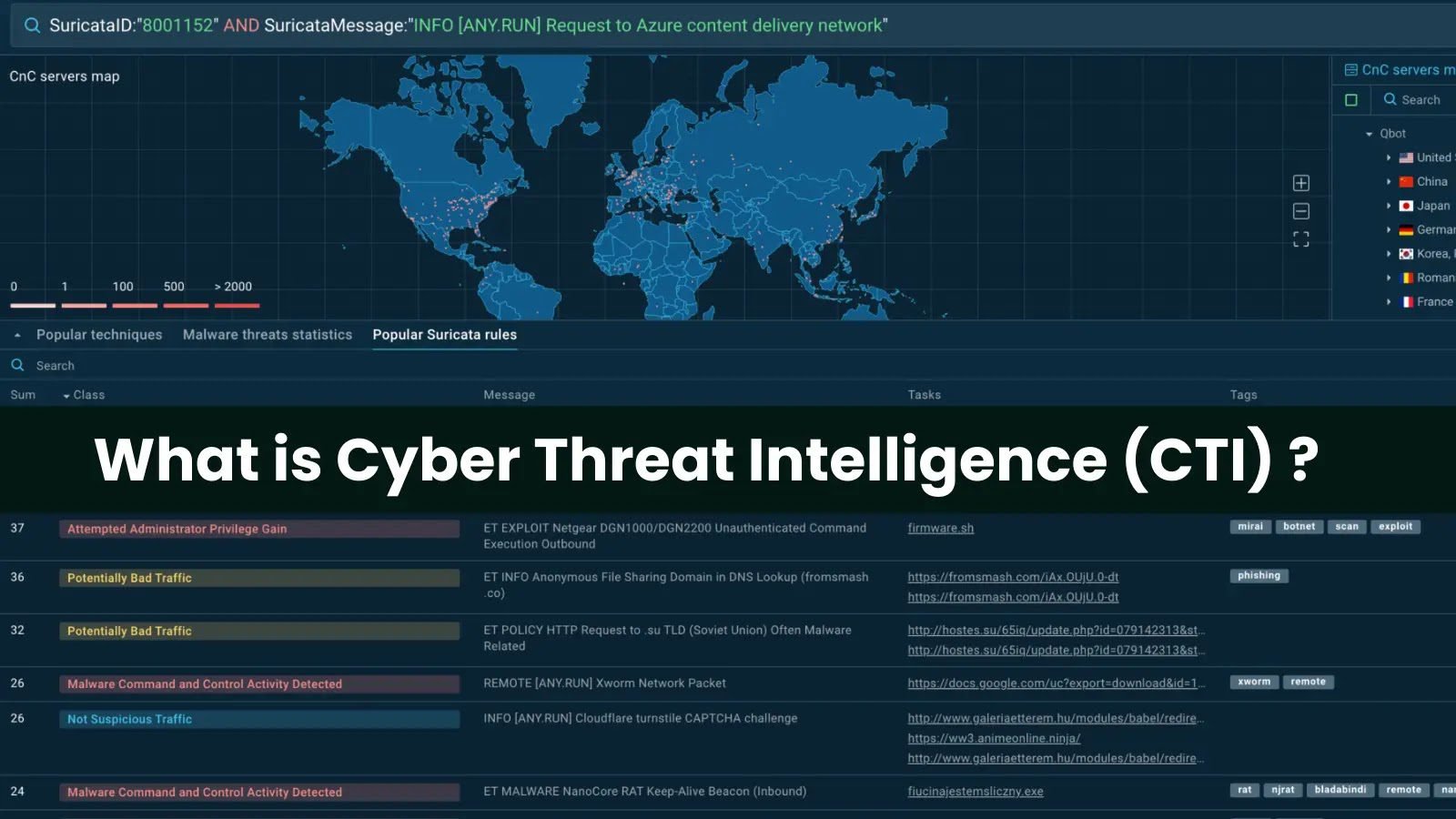
What is Cyber Threat Intelligence (CTI) – How it Works? Cyber Threat Intelligence (CTI), also known as Threat Intelligence or Threat Intelligence, is a critical [...]
Future of 5G: Revolutionizing Network Speeds and Connectivity The future of 5G technology promises to revolutionize network speeds and connectivity, fundamentally transforming how we [...]
Zero-Day Vulnerability In Arcadyan WiFi Devices Allows RCE for Root Access – Exploit Released A critical zero-day vulnerability has been identified in the Arcadyan FMIMG51AX000J [...]
Microsoft Edge RCE Vulnerability Let Attackers Take Control of the System Remotely A critical remote code execution (RCE) vulnerability in Microsoft Edge has been discovered. [...]
Zero Trust Security vs Traditional Firewalls: Which is Superior? Zero Trust Security and Traditional Firewalls represent two distinct approaches to network security, each with its [...]
AI-Powered Cloud Services: The Future of Big Data Analytics In today’s data-driven world, the ability to efficiently analyze and derive insights from vast amounts [...]