New Research Reveals Windows Event Logs Key to Identifying Ransomware Attacks Recent investigations by cybersecurity experts have uncovered valuable insights into detecting human-operated ransomware attacks [...]
HPE Aruba Networking Access Points Vulnerable To Remote Code Execution A critical security advisory has been issued by HPE Aruba Networking, warning of multiple vulnerabilities in their [...]
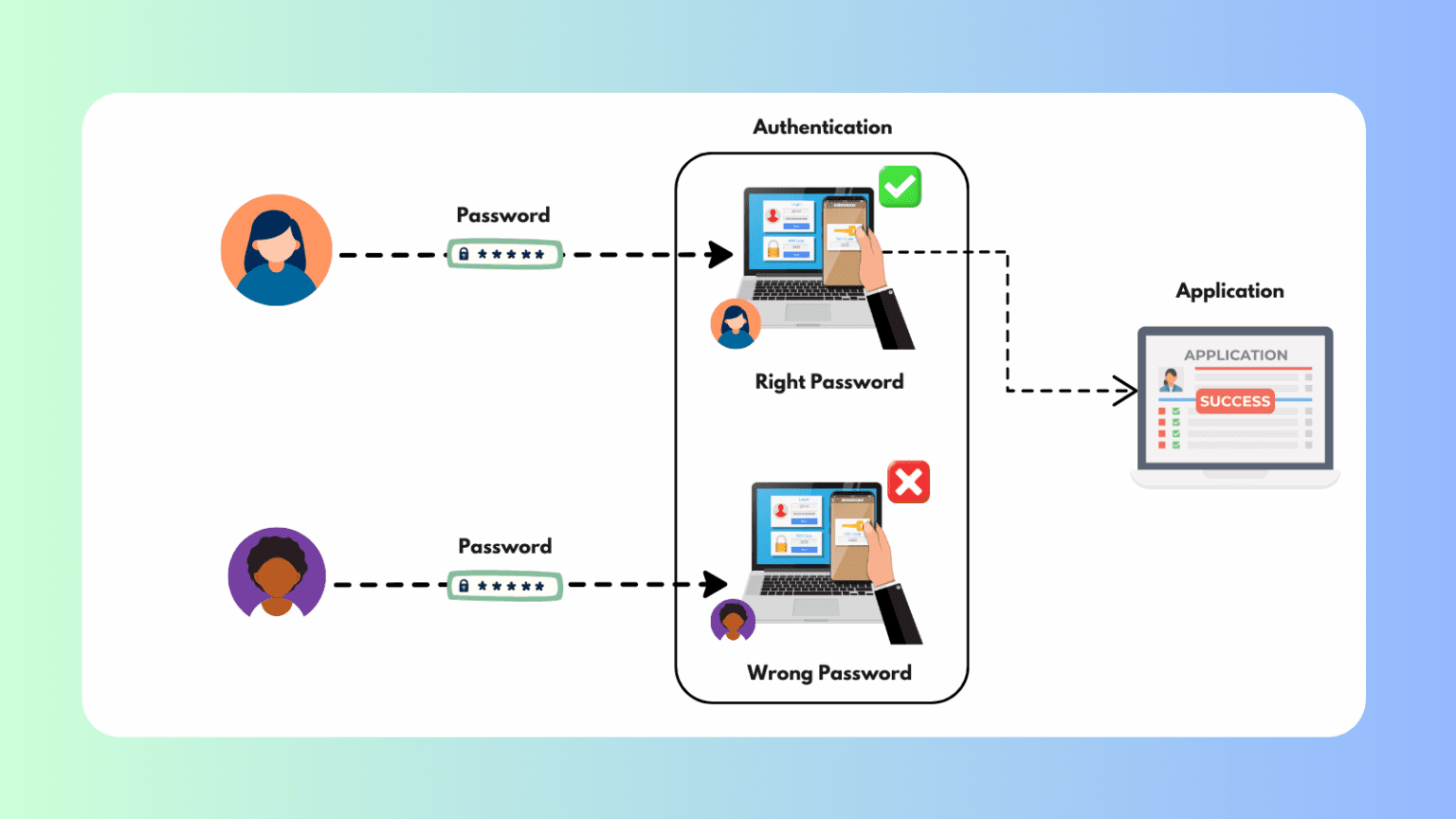
What is Authentication? – Types, Role & How it Works! Authentication is a cornerstone of digital security, serving as the first defense against unauthorized access [...]
CISA Releases Active Directory Security Guide to Mitigate Cyber Attacks In a move to enhance cybersecurity, the Cybersecurity and Infrastructure Security Agency (CISA), in collaboration [...]
GenAI Generated Malware Payload Spotted in the Wild The latest HP Wolf Security Threat Insights Report has revealed the emergence of malware payloads generated using Generative Artificial [...]
Critical FreeBSD Hypervisor Vulnerability Lets Attackers Execute Malicious Code A high-severity vulnerability in the FreeBSD hypervisor, bhyve, has been discovered, allowing malicious software running in [...]
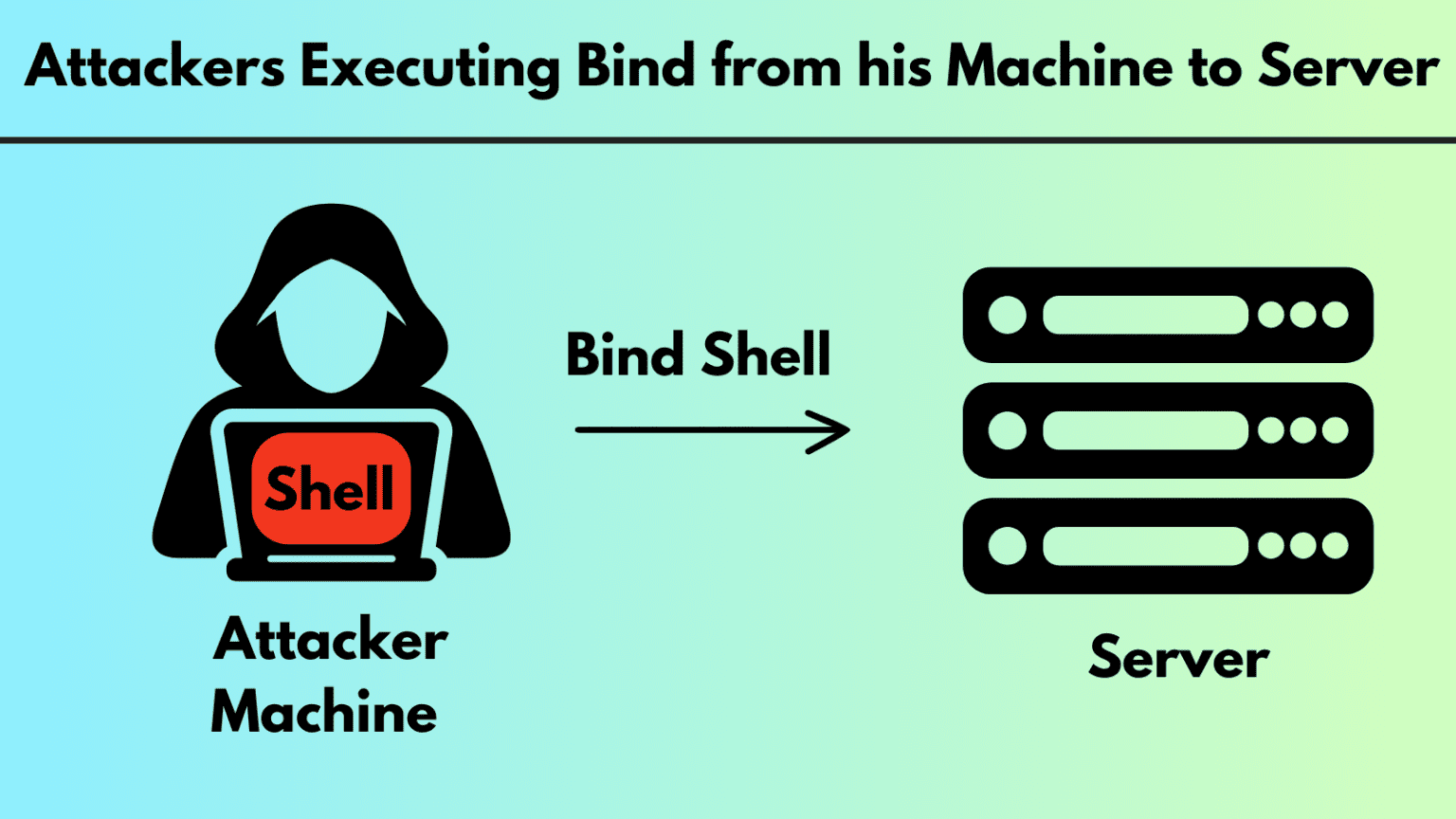
What is a Bind Shell? How it Works, Set Up, Prevention Shells serve as user interfaces that allow interaction with an operating system’s services. They [...]
TeamTNT Hackers Attacking VPS Servers Running CentOS A notorious hacking group known as TeamTNT has resurfaced with a new campaign targeting Virtual Private Server (VPS) infrastructures running [...]
New MacOS Malware Let Attackers Control The Device Remotely A remote access trojan (RAT), HZ RAT, that has been attacking Windows-based devices since at least [...]
What is Botnet? How it Works, Definition & Types A botnet, short for “robot network,” is a collection of internet-connected devices, including computers, servers, mobile [...]