New Threat Hunting Technique to Uncover Malicious Infrastructure Using SSL History As internet security evolves, SSL (Secure Sockets Layer) certificates, cornerstones of encrypted communication, are [...]
VMware Avi Load Balancer Vulnerability Let Attackers Gain Database Access Broadcom disclosed a critical vulnerability affecting its Avi Load Balancer product. The vulnerability, identified as [...]
Hackers Allegedly Selling Fortinet Vulnerability Exploit on Dark Web Forums A significant cybersecurity threat has emerged as hackers on a prominent Russian dark web forum claim to [...]
Hackers Actively Exploiting Zyxel 0-day Vulnerability to Execute Arbitrary Commands A significant zero-day vulnerability in Zyxel CPE series devices, identified as CVE-2024-40891, is being actively exploited by [...]
FortiOS Authentication Bypass Vulnerability Exploited to Gain Super-Admin Access A critical zero-day vulnerability in Fortinet’s FortiOS and FortiProxy products tracked as CVE-2024-55591, has been actively exploited [...]
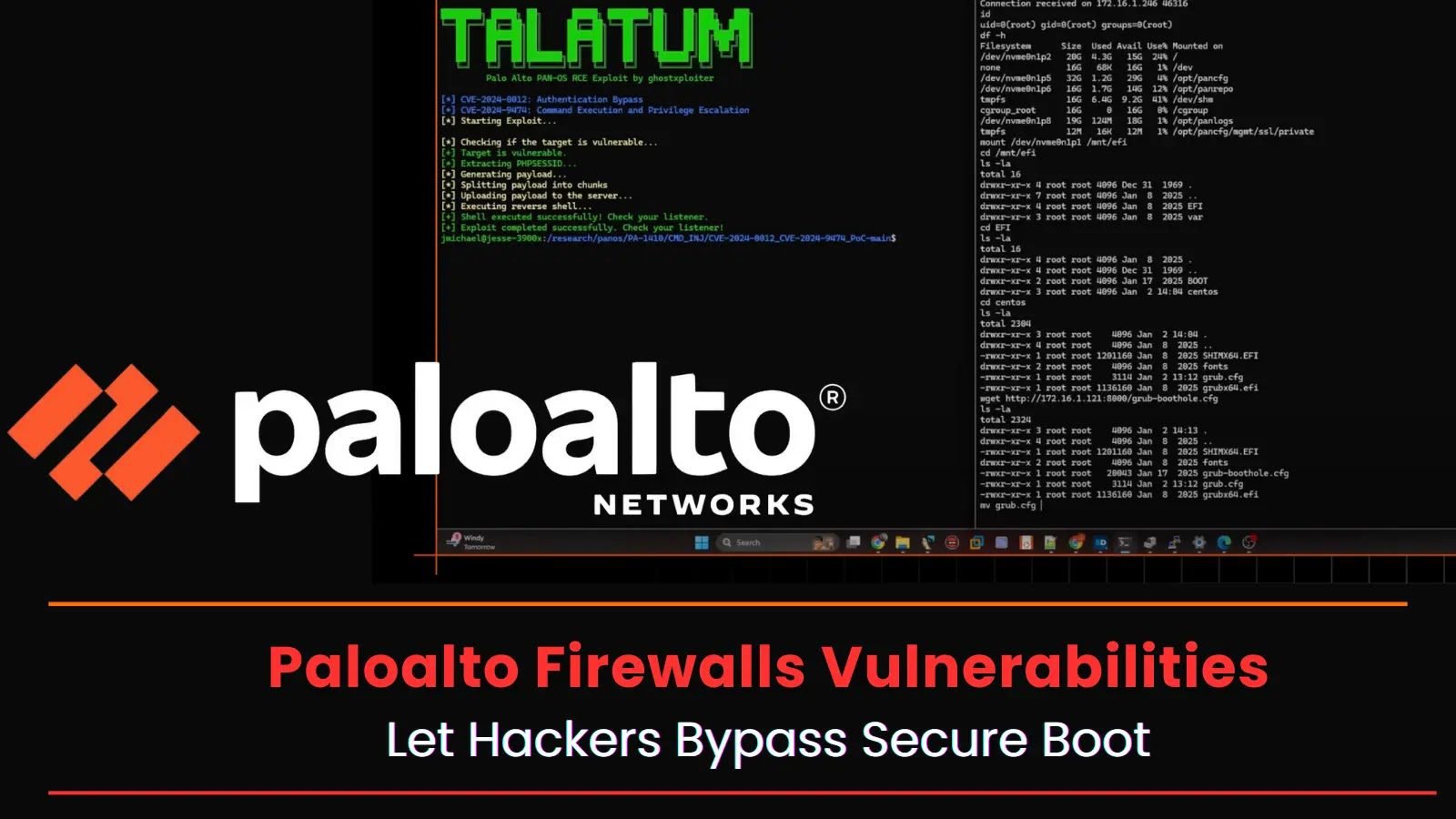
Critical Palo Alto Firewall Vulnerabilities Let Hackers Bypass Secure Boot & Exploit Firmware A recent cybersecurity report has identified critical vulnerabilities in Palo Alto Networks [...]
SonicWall 0-day Vulnerability Exploited In Attacks Execute Arbitrary OS Commands A critical security vulnerability, tracked as CVE-2025-23006, has been identified in SonicWall’s SMA1000 Appliance Management [...]
Cisco Meeting Management Vulnerability Let Attackers Elevate Privileges to Administrator A critical security vulnerability has been identified in Cisco Meeting Management, potentially allowing attackers with [...]
New IoT Botnet Launching Large-Scale DDoS Attacks Hijacking IoT Devices A newly identified Internet of Things (IoT) botnet has been orchestrating large-scale Distributed Denial-of-Service (DDoS) [...]
Hackers Exploited Fortigate 0-Day & Leaked 15,000+ Firewall Configs & Passwords A hacking collective known as the “Belsen Group” has released over 15,000 unique FortiGate [...]