New Ubuntu Security Bypasses Allow Attackers to Exploit Kernel Vulnerabilities Three critical bypasses in Ubuntu Linux’s unprivileged user namespace restrictions allow local attackers to escalate [...]
Microsoft Removes bypassnro.cmd in Windows 11 Insider To Stop Users from Installing OS Without MS Account Microsoft has taken a decisive step in its latest [...]
Cloud Attacks Raises by Five Times Attacking Sensitive IAM Service Accounts Organizations are facing an unbelievable surge in cloud-based security threats, with attacks nearly five [...]
New Sophisticated Linux-Backdoor Attacking OT Systems Exploiting 0-Day RCE A sophisticated Linux-based backdoor dubbed “OrpaCrab” has emerged as a significant threat to operational technology (OT) [...]
VMware Tools for Windows Vulnerability Let Attackers Bypass Authentication VMware addressed a significant authentication bypass vulnerability in its VMware Tools for Windows suite. The vulnerability, [...]
New IOCONTROL Malware Attacking Critical Infrastructure to Gain Remote Access and Control A newly identified malware strain dubbed “IOCONTROL” has emerged as a critical threat [...]
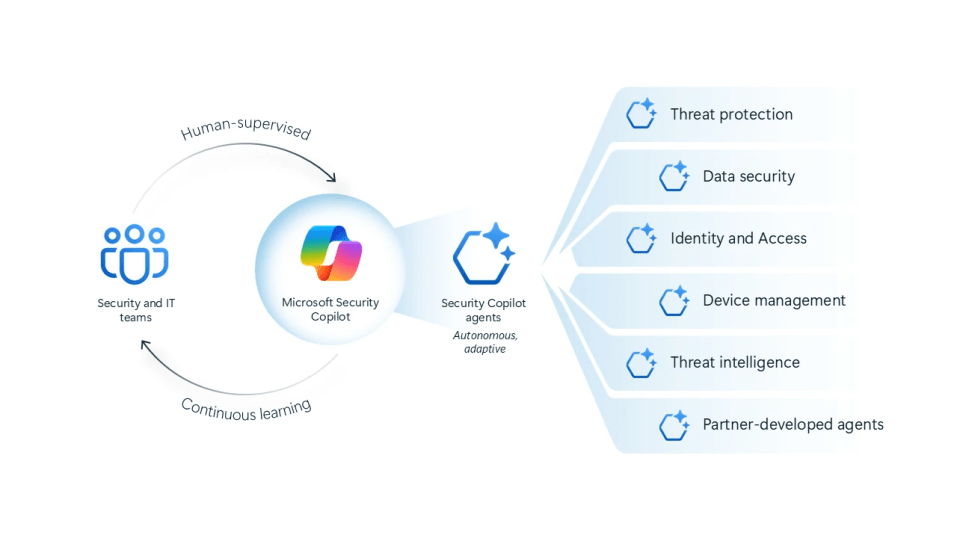
Microsoft Unveils New Security Copilot Agents & Protections for AI Microsoft has announced a significant expansion of its AI-powered security capabilities, introducing autonomous security agents [...]
10 Best Linux Firewalls in 2025 At present, many computers are connected via numerous networks. Monitoring all traffic and having something to filter out good [...]
VPN Vulnerabilities Emerges As The Key Tool for Threat Actors to Attack Organizations VPN infrastructure has become a prime target for cybercriminals and state-sponsored actors, [...]
What is the Difference Between VPN and Proxy . Even though they handle data in slightly different ways, virtual private networks (VPNs) and proxies [...]