Hackers Actively Exploiting Zyxel RCE Vulnerability Via UDP Port A significant spike was observed in exploitation attempts targeting CVE-2023-28771, a critical remote code execution vulnerability affecting [...]
Multiple Vulnerabilities in Ivanti Products. Multiple Vulnerabilities in Ivanti Products Indian – Computer Emergency Response Team (https://www.cert-in.org.in) Severity Rating: HIGH Software Affected Ivanti Workspace Control [...]
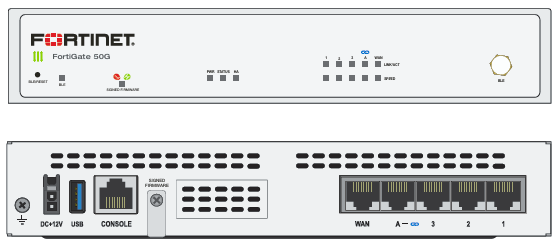
The FortiGate 50G is a next-generation firewall (NGFW) designed to provide robust security features for small to medium-sized enterprises (SMEs). It integrates advanced threat protection, [...]
Palo Alto Networks PAN-OS Vulnerability Enables Admin to Execute Root User Actions A critical command injection vulnerability in Palo Alto Networks PAN-OS operating system enables [...]
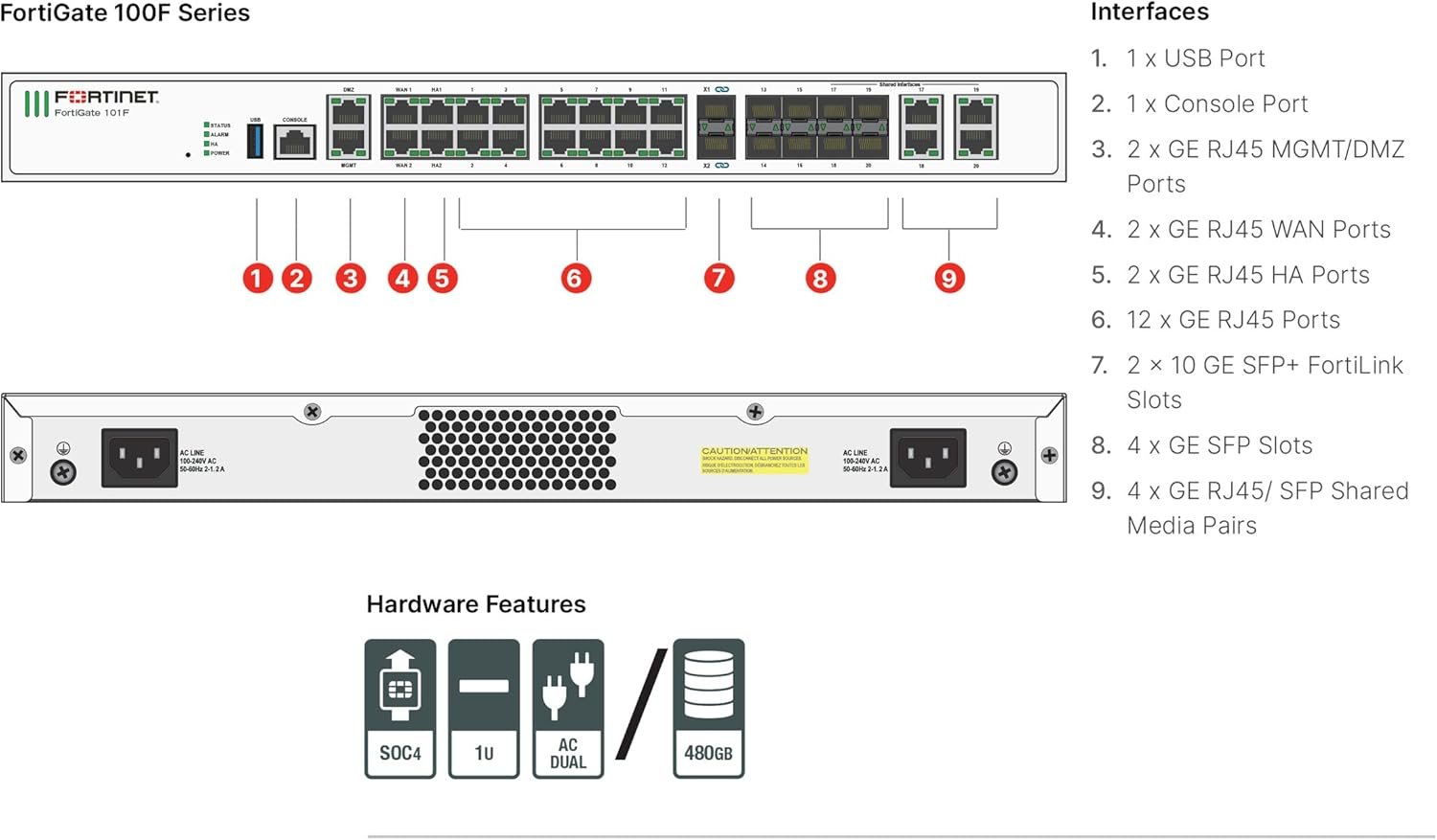
The Fortigate 100F Firewall stands as a robust solution in the realm of network security, designed to protect organizations from an ever-evolving landscape of cyber [...]
Network Cabling & Networking Solutions: Structured Cabling Service In today’s rapidly evolving technological landscape, a robust and reliable network infrastructure is paramount for business success. [...]
In an increasingly interconnected world, the importance of network monitoring cannot be overstated. As businesses rely more heavily on digital infrastructure, the need for robust [...]
Wireless networking technology has undergone a remarkable transformation since its inception, evolving from rudimentary systems to sophisticated networks that underpin modern communication. The journey began [...]
In the rapidly evolving landscape of information technology, networking projects play a pivotal role in ensuring that organizations can communicate effectively, share resources, and maintain [...]
Network optimization is a critical aspect of modern IT infrastructure, focusing on enhancing the performance, reliability, and efficiency of network systems. At its core, network [...]