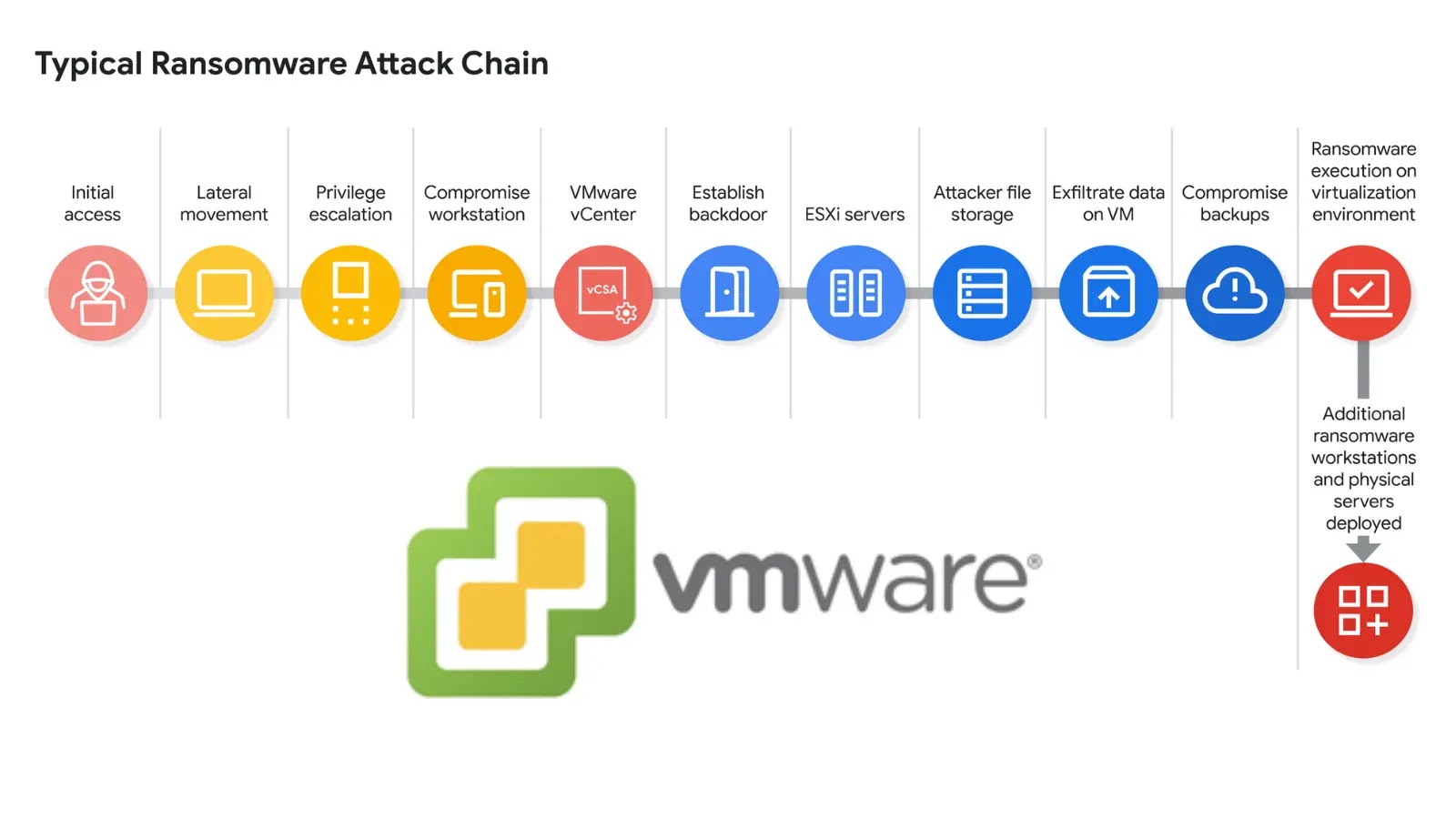
A disturbing new campaign has emerged, highlighting the increasing sophistication of financially motivated threat actors. UNC3944, a group with known ties to “0ktapus,” “Octo [...]
Stealth Backdoor Uncovered in WordPress Mu-Plugins: A Persistent Threat The digital landscape is a constant battleground, and for website administrators, the front lines are [...]
The Silent Swipe: How Weaponized LNK Files Are Pilfering Your Data Disguised as Security Updates In the intricate landscape of digital threats, cunning adversaries [...]
Unmasking Lumma Stealer: The Deceptive Threat Lurking in Cracked Software The cybersecurity landscape is a relentless battleground, and even after significant takedowns, resilient threats [...]
In the evolving landscape of cyber threats, staying ahead of malicious actors is paramount. Recently, a significant shift in attack tactics has been observed, [...]
The Escalating Threat of Credential Theft via Evolving Phishing Attacks Organizations today face an accelerating wave of sophisticated phishing attacks, designed to bypass even [...]
The digital landscape is a battleground where intellectual property often becomes a casualty. In a significant win for content creators and copyright holders, federal authorities [...]
The integrity of national security hinges on the protection of sensitive intelligence. When that trust is breached from within, the implications are profound, extending far [...]
Critical Vulnerability in JavaScript Library Exposes Millions of Apps to Code Execution Attacks A significant cybersecurity threat has emerged, potentially impacting a vast array [...]
The digital landscape is a constant negotiation between innovation and privacy. Nowhere is this more evident than in the recent actions taken by Brave, [...]