The landscape of personal computing is undergoing a significant transformation, driven by the rapid advancements in Artificial Intelligence. Microsoft, a titan in the technology [...]
Coyote Malware Pioneers Windows UI Automation Exploitation for Banking Credential Theft The cybersecurity landscape continually evolves, with threat actors innovating new methods to circumvent defenses [...]
Ransomware Gangs Weaponize RMM Tools: A New Era of Targeted Cyberattacks Once the silent workhorses of IT departments, Remote Monitoring and Management (RMM) software [...]
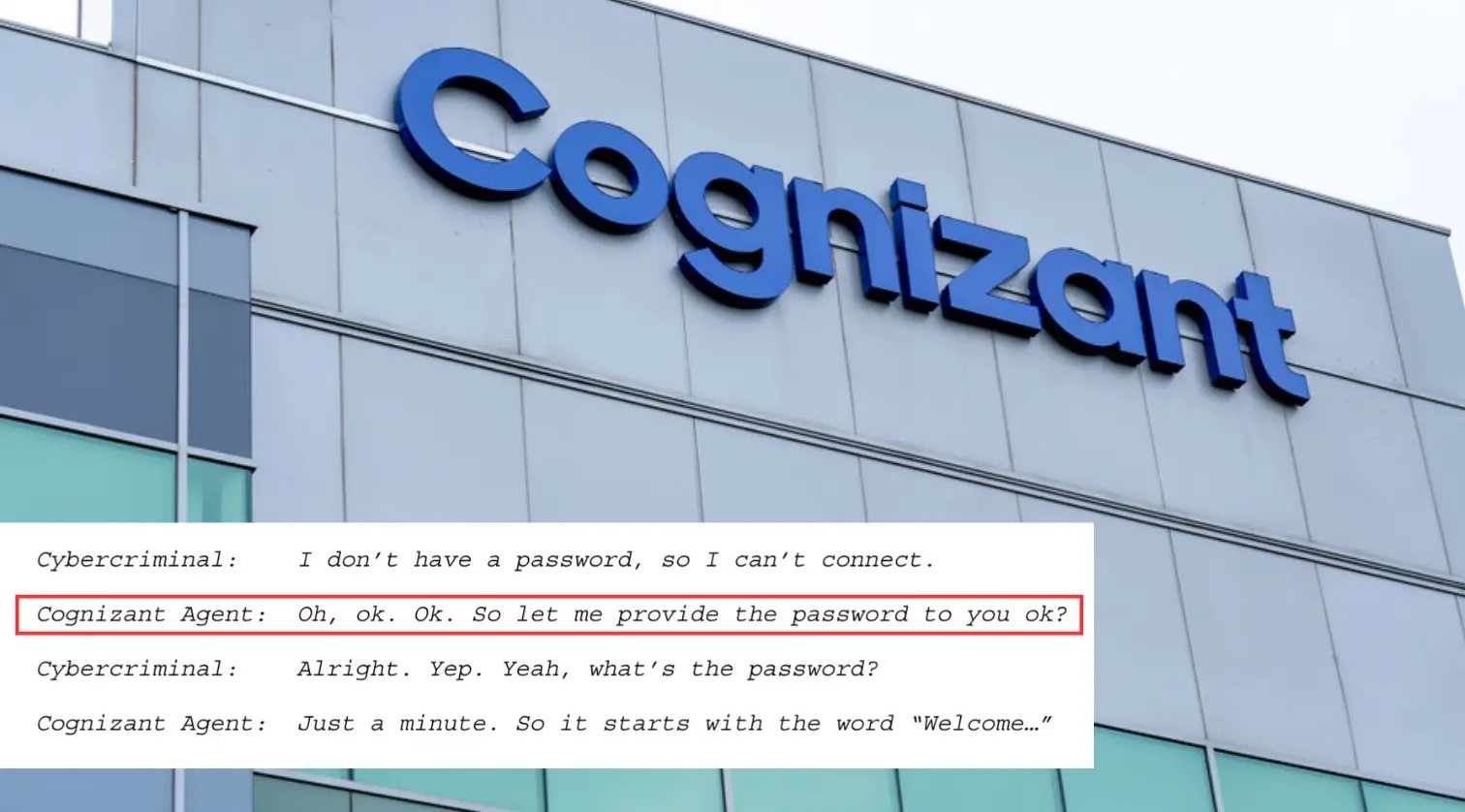
The quiet hum of business operations can turn into a cacophony of disruption when cybersecurity fails. This stark reality has hit The Clorox Company, [...]
Kerberoasting Detections: A New Approach to a Decade-Old Challenge For over a decade, cybersecurity experts have grappled with the persistent threat of Kerberoasting. Despite [...]
US Nuclear Weapons Agency Breached: Exploiting SharePoint 0-Day, A Critical Analysis The National Nuclear Security Administration (NNSA), a cornerstone of US defense infrastructure, has [...]
In the evolving landscape of digital threats, staying ahead is not just a best practice—it’s a necessity. Today, we’re dissecting a critical update from [...]
The open-source community thrives on collaboration and user contributions, epitomized by platforms like the Arch User Repository (AUR). However, this very openness, while fostering innovation, [...]
In a perilous development for organizational security, the Cybersecurity and Infrastructure Security Agency (CISA) has issued an urgent and critical alert: sophisticated Chinese state-sponsored [...]
The open-source software ecosystem, the backbone of modern digital infrastructure, faces an escalating threat: software supply chain attacks. These insidious attacks, often targeting widely [...]