Organizations face an ever-evolving threat landscape, where traditional phishing tactics are continually refined to bypass robust security measures. A new, highly sophisticated campaign has [...]
Urgent Alert: CrushFTP 0-Day Vulnerability Exploited in the Wild The digital landscape is constantly under siege, and the latest threat comes in the form [...]
The Lumma Infostealer: Unmasking a Persistent Browser Data Threat In the evolving threat landscape, information stealers remain a primary concern for cybersecurity professionals and [...]
In the interconnected landscape of modern networks, the stability and security of infrastructure devices are paramount. A recent revelation has sent ripples through the cybersecurity [...]
The cybersecurity landscape is constantly shifting, with malicious actors continually refining their tactics. A recent and particularly insidious development involves threat actors weaponizing GitHub, [...]
Stealthy Monero Miners: A New Wave of Crypto-Hijacking Compromises 3,500+ Websites The digital landscape is a battleground where unseen threats constantly evolve. A recent, [...]
Fancy Bear’s Resurgence: A Heightened Threat to Governments and Military Sectors The digital battleground is constantly shifting, and a familiar, formidable adversary is once [...]
The digital supply chain has become a primary target for sophisticated cyber adversaries. No industry is immune, and recent events underscore the pervasive threat. [...]
Urgent! Threat Actors Weaponize Ivanti Connect Secure VPNs with Cobalt Strike The digital perimeter of many organizations is under an advanced, stealthy assault. Threat [...]
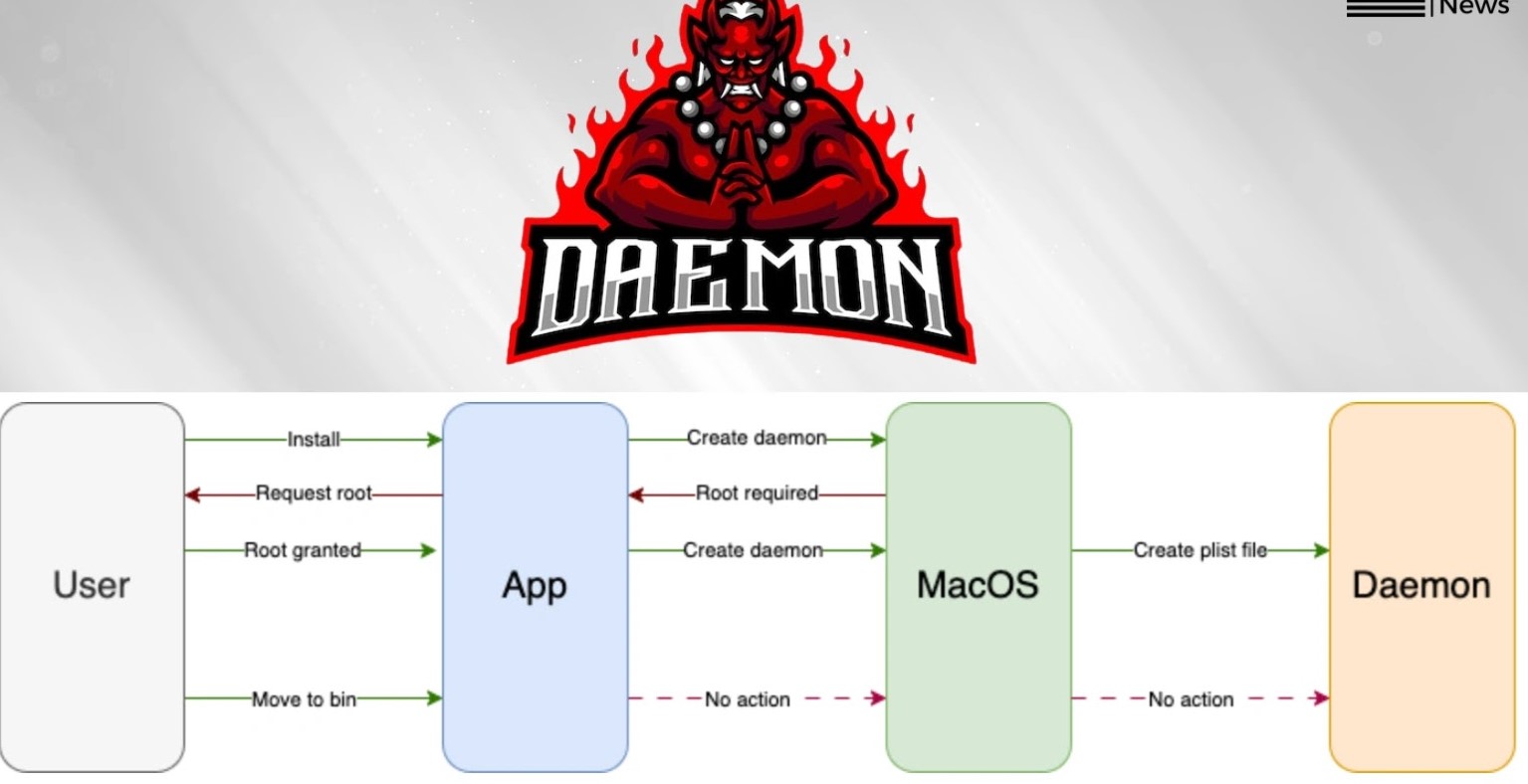
Unmasking “Daemon Ex Plist”: A macOS Vulnerability Exposing Root Privileges The digital landscape is under constant siege, and even seemingly secure operating systems like [...]