Malware delivery methods are constantly evolving, and a new, insidious social engineering technique dubbed “ClickFix” has rapidly emerged as a significant threat in late [...]
The Domain Name System (DNS) is a foundational, yet often overlooked, component of the internet’s infrastructure. When critical vulnerabilities emerge within widely deployed DNS [...]
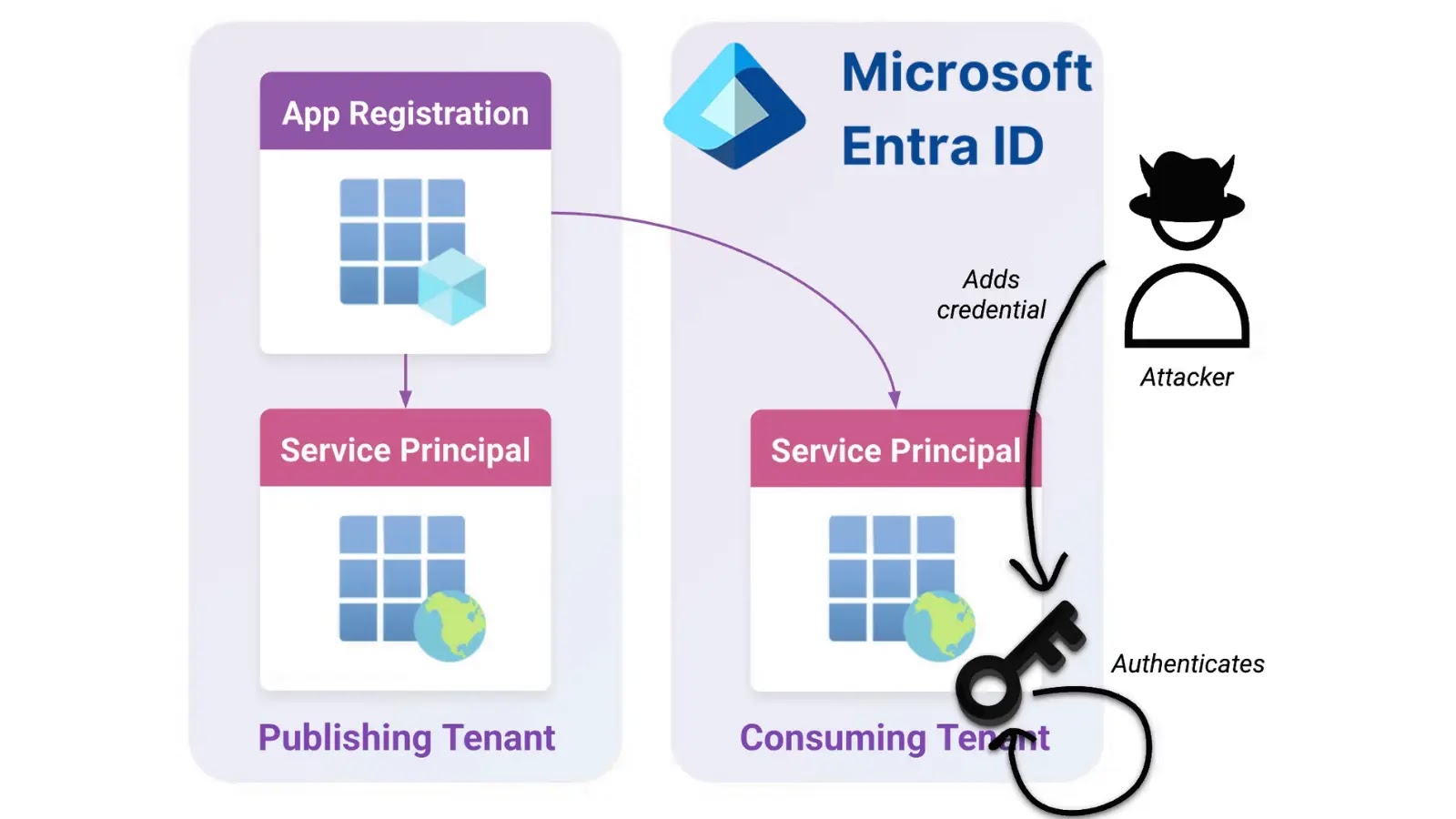
A Critical Alert: Microsoft Entra ID Vulnerability Exposes Global Admin Privileges The digital defense perimeter of countless organizations is under significant scrutiny following the [...]
In the high-stakes arena of cyber warfare, attributed attacks often serve as stark reminders of geopolitical tensions spilling over into the digital domain. Recent reports [...]
Chinese State-Sponsored Cyber Espionage: Weaponized Cobalt Strike Targets the Semiconductor Industry The global semiconductor industry, the bedrock of modern technology, is under intense cyber [...]
Hackers Exploit GitHub Repositories to Host Amadey Malware and Data Stealers, Bypassing Filters The digital threat landscape constantly evolves, with adversaries devising innovative methods to [...]
The digital threat landscape constantly shifts, with attackers innovating new methods to bypass even the most robust security measures. A particularly insidious and growing [...]
The digital landscape is a constant battleground, with threat actors continuously evolving their tactics to exploit new vulnerabilities and revive old ones. One such [...]
Unmasking the New Era of Hacktivism: Attention, Monetization, and Evolving Targets The global hacktivist landscape has undergone a dramatic transformation. No longer solely defined by [...]
Unmasking the Threat: 4M+ Systems Exposed by Tunneling Protocol Vulnerabilities The digital perimeter of countless organizations is under significant threat. Recent revelations by security [...]