Unclassified U.S. Intelligence Website Breached: A Deep Dive into the Attack on the ARC The digital perimeter of U.S. national security has once again [...]
Cloud infrastructure underpins a vast majority of modern applications and services, making its consistent performance, ironclad security, and unwavering availability paramount. As organizations increasingly [...]
LG Innotek Camera Vulnerabilities: A Critical Warning for Network Security The landscape of network security is constantly shifting, with new threats emerging that target [...]
The Arizona Laptop Farm: Unmasking State-Sponsored Cyber Infiltration The recent sentencing of an Arizona woman for her role in a sophisticated scheme enabling North [...]
The digital landscape is under constant siege, and threat actors are perpetually refining their tactics. A recent and alarming development highlights this reality: the [...]
In the dynamic landscape of enterprise software, critical vulnerabilities can emerge without warning, posing significant threats to data integrity and system security. Recently, Salesforce’s [...]
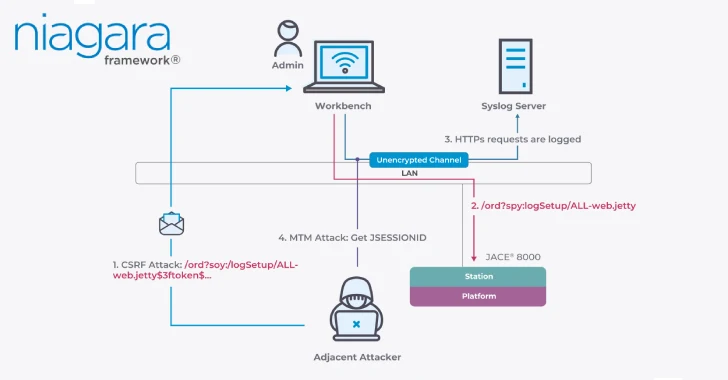
Smart buildings and industrial control systems (ICS) form the backbone of modern infrastructure, from managing colossal energy grids to optimizing essential manufacturing processes. Their [...]
Weekly Cybersecurity News Recap: SharePoint 0-Day, VMware Exploitation, Threats & Cyber Attacks Welcome to this week’s cybersecurity recap, covering critical updates from July 21-27, [...]
The modern digital landscape hinges on mobile interactions. Businesses increasingly recognize that bridging the divide between their web presence and their mobile applications is [...]
Allianz Life Insurance Data Breach: 1.4 Million Customers’ Data Compromised The digital landscape, while offering unparalleled convenience, also presents an ever-present threat: the data [...]