—–BEGIN PGP SIGNED MESSAGE—– Hash: SHA256 Multiple vulnerabilities in ISC Bind Indian – Computer Emergency Response Team (https://www.cert-in.org.in) Severity Rating: HIGH Systems Affected BIND Supported [...]
The digital landscape is a constant battleground, and even the most familiar tools can become weapons in the hands of malicious actors. A significant [...]
In a significant victory against the relentless surge of cybercrime, international law enforcement agencies have dealt a substantial blow to the BlackSuit ransomware operation. [...]
The digital landscape is a constant battleground, and sophisticated threat actors continually push the boundaries of cyber espionage. A new campaign, dubbed “Fire Ant,” [...]
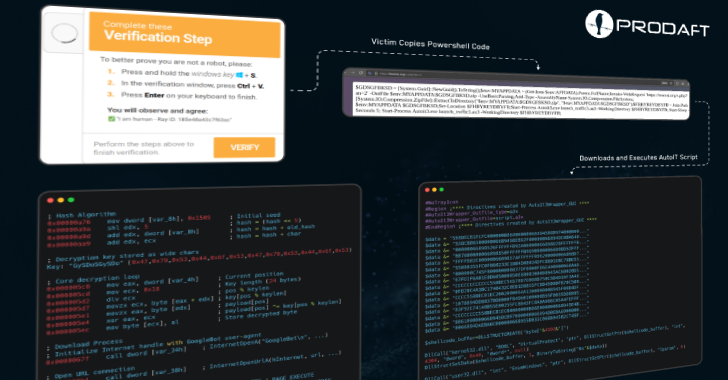
CastleLoader Emerges: Unpacking the Cloudflare-Themed Clickfix Attack Against Windows The digital landscape is under perpetual siege, with adversaries constantly refining their tactics. A recent and [...]
The Gamer’s Peril: New Malware Weaponizes YouTube and Discord for Credential Theft In the evolving threat landscape, attackers relentlessly seek novel methods to compromise [...]
Unmasking the Elephant: APT Group’s Advanced Cyber-Espionage Campaign The digital battlefield is constantly evolving, and the latest threat intelligence points to a highly sophisticated [...]
The digital defense perimeter is constantly shifting, and even the most robust systems can be breached by subtle, insidious attacks. A recent incident involving Amazon’s [...]
The digital battlefield is constantly evolving, with advanced persistent threats (APTs) continually refining their tactics. Few developments pose as significant a threat as the [...]
TP-Link NVR Vulnerabilities: A Critical Threat to Surveillance Infrastructure The security of our physical spaces increasingly relies on robust surveillance systems. However, recent discoveries [...]