A severe security vulnerability has been identified that places countless WordPress websites at significant risk. Specifically, a critical flaw in the widely used “Database [...]
Navigating the AI-Powered Cyber Warfare: Your Survival Guide The artificial intelligence revolution isn’t a future prediction; it’s our present reality. From intelligent co-pilots streamlining [...]
Unmasking Charon: The New Ransomware Employing DLL Sideloading and Anti-EDR Tactics The cybersecurity landscape just became a significant degree more perilous for organizations, particularly [...]
The Lingering Spectre: XZ Backdoor Found in Docker Images The cybersecurity landscape was irrevocably altered in March 2024 with the discovery of the XZ [...]
For far too long, Security Operations Centers (SOCs) have operated under immense pressure, battling an incessant deluge of alerts. The reality for many SOC [...]
In a critical development for enterprise security, both Zoom and Xerox have recently deployed urgent security updates to address significant vulnerabilities that could expose [...]
The digital landscape is under perpetual siege, and the latest alarm comes from Fortinet, a leading cybersecurity vendor. Fortinet has issued an urgent warning [...]
Urgent Alert: Critical Microsoft Office Vulnerabilities Enable Remote Code Execution The digital landscape is under perpetual siege, and the latest threat comes in the [...]
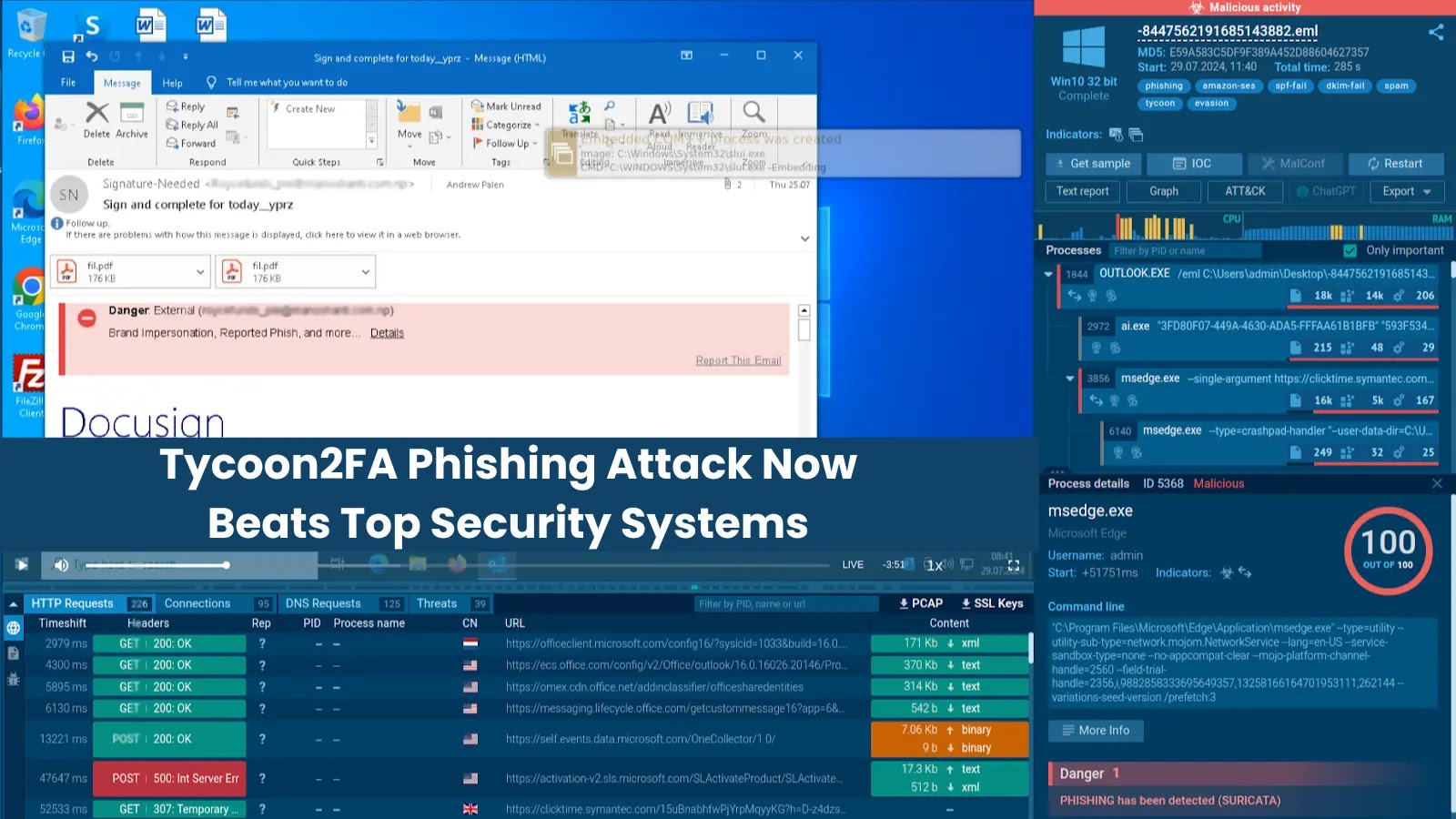
The End of Easy Phishing: Tycoon2FA Attacks Defy Traditional Security Defenses The landscape of cyber threats is witnessing an audacious evolution. Forget the simplistic [...]
A new, highly sophisticated Advanced Persistent Threat (APT) group, dubbed “Curly COMrades,” has emerged on the global cybersecurity landscape, posing a significant threat to [...]