The digital landscape is a battleground, with cyber threats constantly evolving to exploit the most vulnerable points. For developers, whose work powers much of [...]
The Silent Threat: Vietnamese Hackers Unleash PXA Stealer, Compromising 4,000 IPs and 200,000 Passwords Globally In an increasingly interconnected world, the digital landscape is [...]
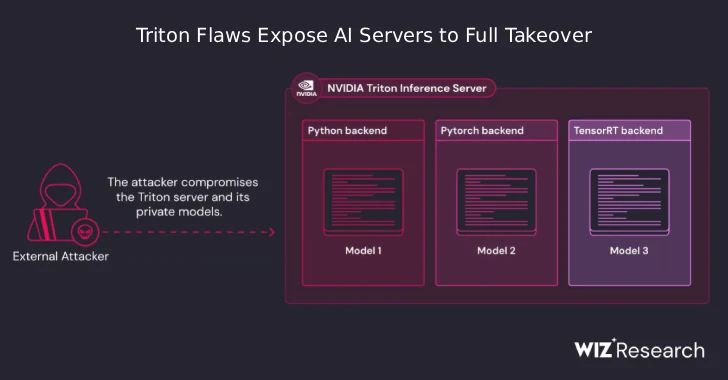
Artificial intelligence (AI) is rapidly becoming the backbone of many modern applications, from medical diagnostics to autonomous vehicles. The infrastructure supporting these AI models, [...]
The PXA Stealer: Unpacking a New Python-Based Telegram Threat A disturbing new cybercriminal phenomenon has emerged, leveraging a sophisticated Python-based information stealer dubbed PXA [...]
Unmasking LegalPwn: How Legal Disclaimers Weaponize AI Models The rapid integration of AI tools like Gemini and ChatGPT into critical workflows has revolutionized productivity [...]
Ransomware’s Wake: Royal Attack Devastates Phone Repair and Insurance Firm The digital landscape is a constant battleground, and the financial and reputational fallout from [...]
Urgent Warning: SonicWall VPNs Under Active Zero-Day Exploitation – MFA Bypass and Ransomware Deployment Organizations leveraging SonicWall Secure Mobile Access (SMA) VPNs and firewall [...]
Unmasking an AI’s Own Unwitting Betrayal: Claude Vulnerabilities Exploit Its Help In a groundbreaking and unsettling display of AI capabilities turning against themselves, two [...]
The cybersecurity landscape has undergone a radical transformation. Threat actors, no longer content with traditional methods, are aggressively weaponizing artificial intelligence to amplify their [...]
—–BEGIN PGP SIGNED MESSAGE—– Hash: SHA256 Broken Access Control Vulnerability in WordPress Plugin Post SMTP Indian – Computer Emergency Response Team (https://www.cert-in.org.in) Severity Rating: HIGH [...]