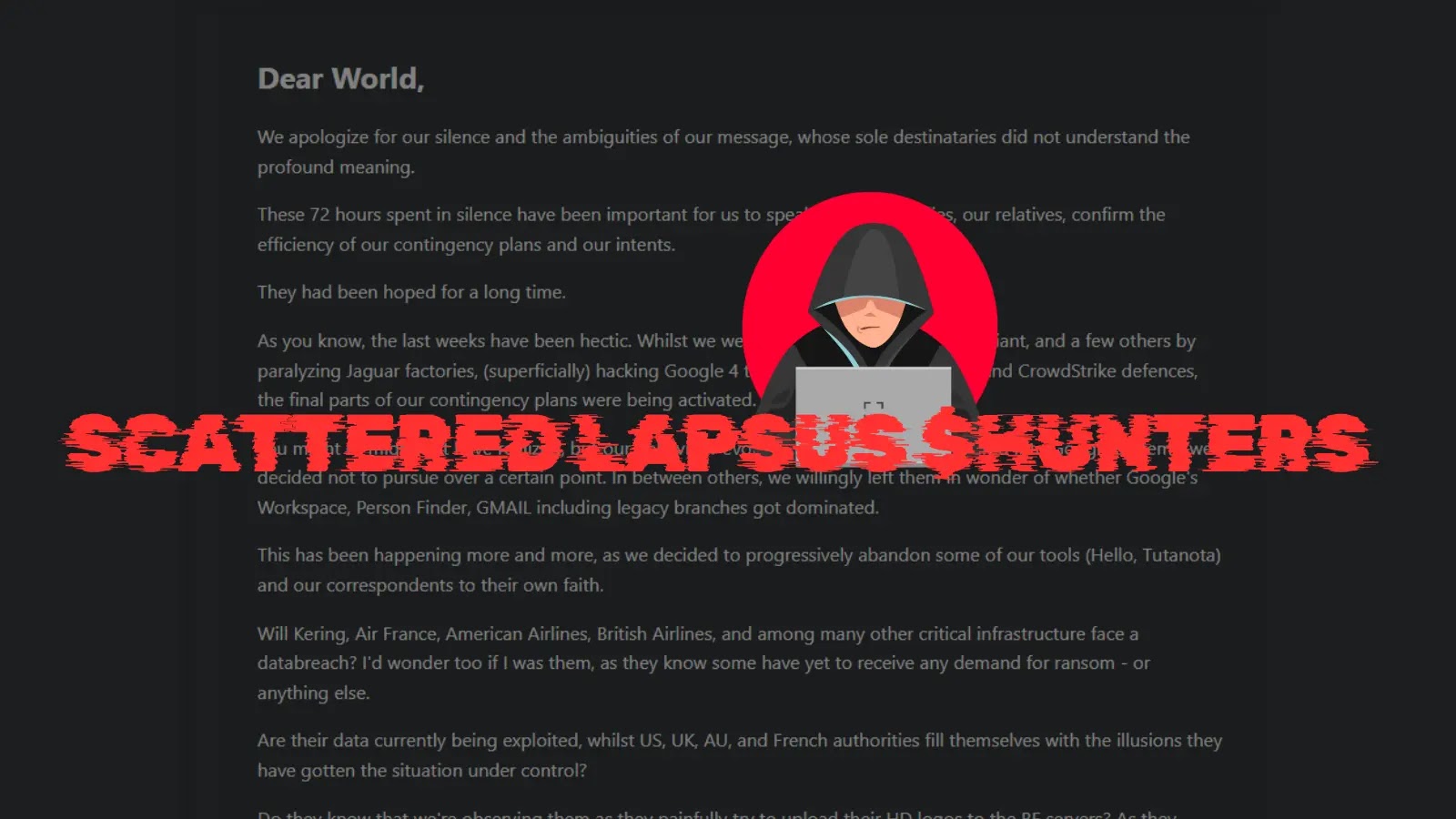
The digital shadows cast by cybercriminal groups often obscure their true motives and operational strategies. However, a recent, highly unusual “farewell statement” from the notorious [...]
A disturbing new report highlights a critical vulnerability stemming from ChatGPT’s expanded integration capabilities. What was intended as a feature to enhance productivity and [...]
—–BEGIN PGP SIGNED MESSAGE—– Hash: SHA256 Multiple vulnerabilities in Google Chrome for Desktop Indian – Computer Emergency Response Team (https://www.cert-in.org.in) Severity Rating: HIGH Software Affected [...]
—–BEGIN PGP SIGNED MESSAGE—– Hash: SHA256 Multiple Vulnerabilities in Ivanti Products Indian – Computer Emergency Response Team (https://www.cert-in.org.in) Severity Rating: HIGH Software Affected Ivanti Connect [...]
—–BEGIN PGP SIGNED MESSAGE—– Hash: SHA256 Multiple Vulnerabilities in Adobe Products Indian – Computer Emergency Response Team (https://www.cert-in.org.in) Severity Rating: HIGH Software Affected Acrobat DC [...]
Cyber Attack Disrupts Inside The Jaguar Land Rover (JLR) Operations What Went Wrong On Cyberattack In an era where cyber threats loom large over industries, [...]
Unmasking the Threat: Git Credential Exfiltration in ArgoCD In the evolving landscape of DevOps and continuous delivery, tools like ArgoCD have become indispensable for [...]
The digital threat landscape never stands still. As organizations increasingly rely on cloud-based services, a new wave of sophisticated credential harvesting operations targets the [...]
Angular SSR Vulnerability: A Critical Data Leakage Risk for Your Applications In the intricate landscape of web application development, Server-Side Rendering (SSR) offers significant [...]
LNER Data Breach: A Third-Party Compromise Exposes Passenger Information In an increasingly interconnected digital landscape, the security posture of an organization extends far beyond [...]