Drone Cybersecurity: Protecting Drone Technology from Cyber Threats The rapid evolution of drone technology has ushered in a new era of innovation across various sectors, [...]
In the intricate landscape of system management and debugging, specialized tools are indispensable. However, the very utilities designed to offer granular control can, if [...]
The cybersecurity landscape is fraught with challenges, yet few incidents resonate as deeply as those impacting critical national infrastructure. A recent development has brought [...]
AI Governance & Security: Risk Management for Artificial Intelligence In the ever-evolving landscape of artificial intelligence, ensuring the security and governance of AI systems is [...]
Wearable Devices: Cybersecurity and Security Risk in Medical Devices and Wearable Technology In the rapidly evolving landscape of digital health, wearable technology stands at the [...]
Organizations leveraging SonicWall products are facing a critical security alert. The Australian Cyber Security Centre (ACSC) has issued an urgent warning regarding a severe [...]
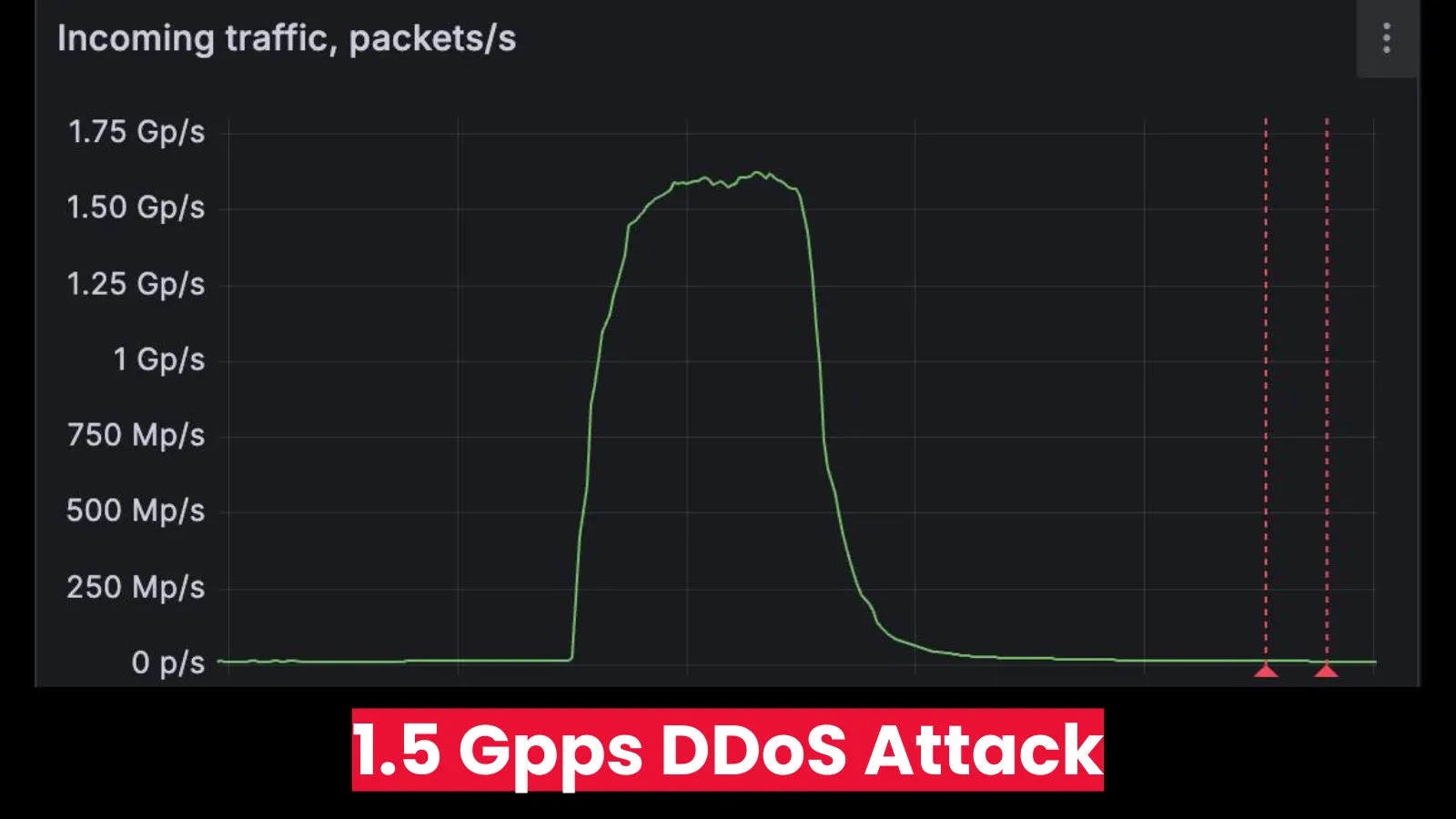
The digital landscape is a constant battleground, and even the most prepared organizations can find themselves under unprecedented assault. This week, the cybersecurity community [...]
The relentless wave of cyber threats has made robust cybersecurity no longer a luxury but a fundamental necessity for businesses of all sizes. Small [...]
New Phishing Attack Mimics Google AppSheet to Steal Login Credentials In the evolving landscape of cyber threats, attackers continually refine their tactics, leveraging legitimate [...]
A Cyber Adversary’s Unforced Error: When EDR Becomes an Insider Threat In a fascinating turn of events, a recent incident unveiled a significant operational [...]