The long arm of the law has finally brought down the creator of one of the internet’s most notorious cybercriminal havens. In a decisive [...]
The intricate dance of microservices within Kubernetes clusters forms the backbone of modern cloud-native applications. As organizations increasingly rely on these dynamic environments, the [...]
Unmasking the Kubernetes C# Client Vulnerability: A Critical Look at MiTM Risks In the intricate landscape of cloud-native infrastructure, the integrity of communication channels [...]
Elevating Data Security: Google Sheets Now Features Client-Side Encryption In an era where data breaches are unfortunately common and compliance regulations are increasingly stringent, [...]
Network Segmentation in Cybersecurity: What You Need to Know In today’s interconnected world, where data breaches and cyber threats are ever-evolving, implementing effective network segmentation [...]
A fundamental security assumption for many organizations relies on BitLocker’s robust encryption to protect sensitive data on Windows systems. However, a recently disclosed critical vulnerability, [...]
FinWise Insider Breach: A Cautionary Tale of Data Exfiltration The digital landscape is fraught with perils, and while external threats often dominate headlines, the [...]
Linux Kernel’s KSMBD Vulnerability: A Critical Resource Exhaustion Threat In the complex landscape of server infrastructure, the stability and availability of services are paramount. [...]
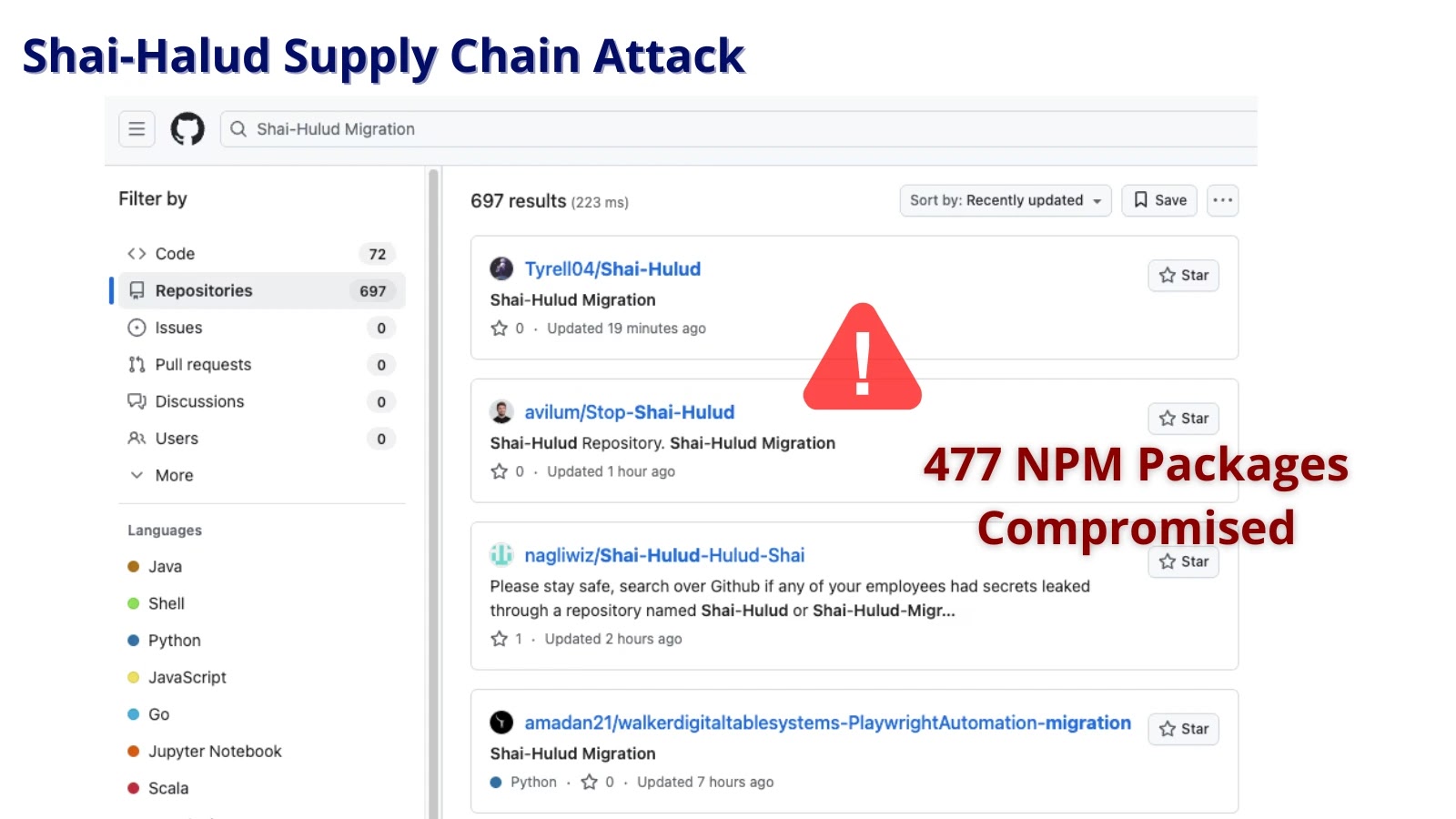
The JavaScript ecosystem, a cornerstone of modern web development, has once again been rocked by a sophisticated supply chain attack. Dubbed “Shai-Halud,” this large-scale [...]
Gamified Cybersecurity Awareness Training: The Power of Gamification in Cyber Security Awareness. In today’s digital age, where cyber threats are constantly evolving, ensuring a robust [...]