How Fortigate Reduces Next-Generation Firewall ROI: Fortinet FortiGate vs. Palo Alto Downtime and Boosts Productivity. In the realm of cybersecurity, safeguarding your enterprise is paramount [...]
Unmasking CVE-2025-12080: The Hidden SMS Threat in Google Wear OS In a landscape where our smart devices are increasingly intertwined with our personal data, a [...]
Remote Code Execution (RCE) Explained: Understanding RCE Attacks AI Platforms In today’s interconnected digital landscape, safeguarding your enterprise against cyber threats is paramount. Remote Code [...]
The cybersecurity landscape just got a lot more dangerous with the emergence of the Beast ransomware, a sophisticated threat actively scanning for open Server [...]
The cybersecurity landscape has once again been shaken by urgent warnings from the U.S. Cybersecurity and Infrastructure Security Agency (CISA). This time, the focus [...]
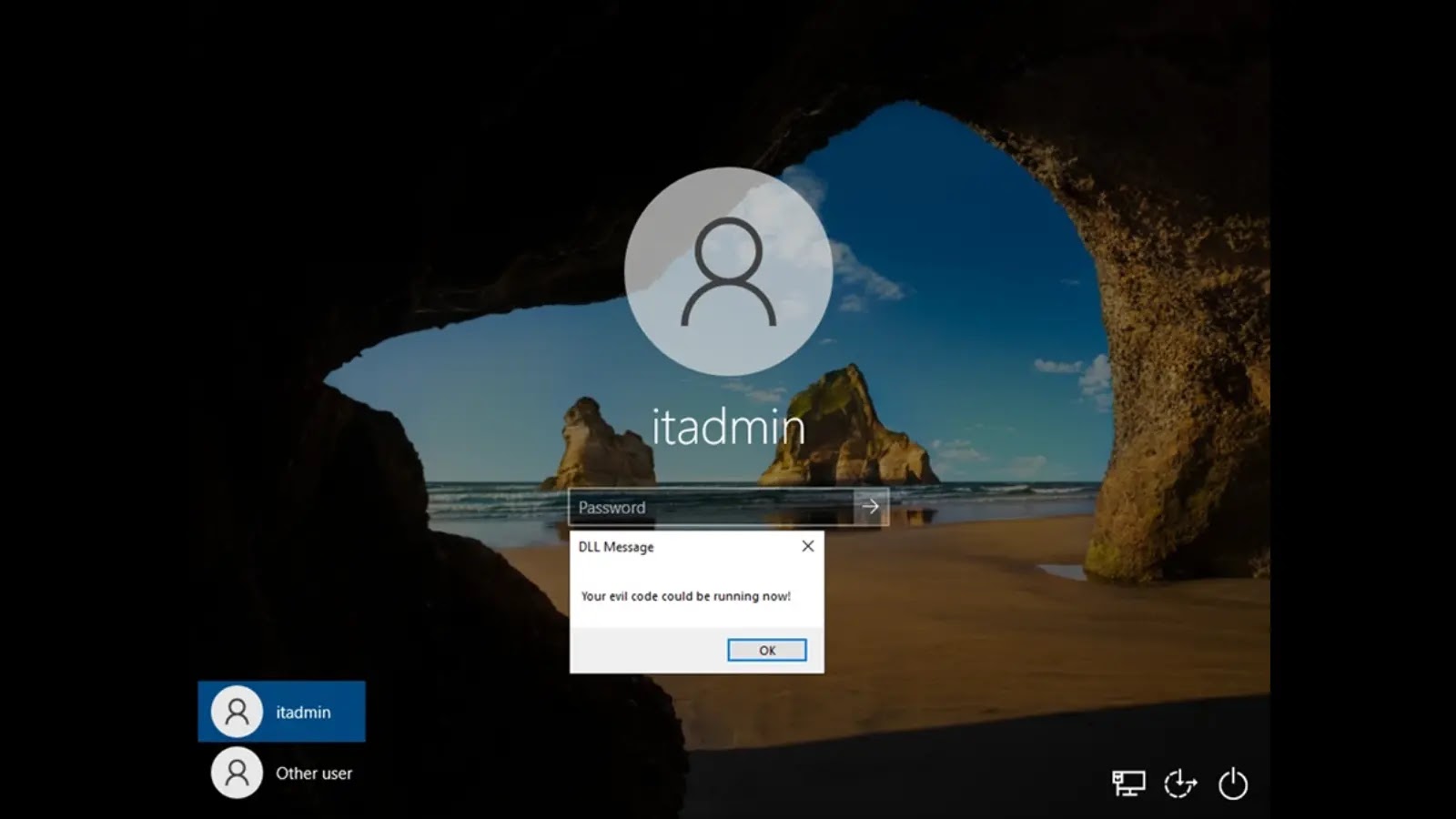
Unmasking the Stealthy Threat: Windows Narrator DLL Hijacking The digital landscape demands constant vigilance against evolving threats. Even seemingly innocuous system features can harbor [...]
The digital landscape is constantly shifting, and with it, the demands for robust online security. Google is taking a monumental step that will fundamentally [...]
Atroposia RAT: Unpacking the New Turnkey Threat to Cybersecurity The cybersecurity landscape constantly evolves, with new threats emerging to challenge our defenses. A significant [...]
In the relentless battle against cyber threats, one vulnerability consistently resurfaces as a critical entry point for adversaries: compromised credentials. Mandiant’s recent M-Trends report highlights [...]
The relentless evolution of ransomware continues to challenge organizations globally. A new and concerning entry to this threat landscape is Gunra ransomware, which emerged [...]