In the high-stakes world of e-commerce, the security of online storefronts is paramount. A single vulnerability can lead to devastating data breaches, financial losses, and [...]
Critical ASP.NET Vulnerability Unleashes HTTP Request Smuggling Risk A high-severity flaw in ASP.NET Core, identified as CVE-2025-55315, has been detailed by Microsoft, posing a significant [...]
Microsoft Under Fire: Australian Regulator Alleges Misleading Microsoft 365 Subscriptions In an era where digital subscriptions are ubiquitous, trust and transparency are paramount. When a [...]
Sweden’s Critical Infrastructure Under Attack: Svenska kraftnät Confirms Data Breach The digital defense of critical infrastructure has been breached, sending repercussions across Europe’s cybersecurity landscape. [...]
Unpacking the Gmail “Breach”: More Misinformation, Less Malice The digital landscape is a constant ebb and flow of information, and sometimes, misinformation can spread like [...]
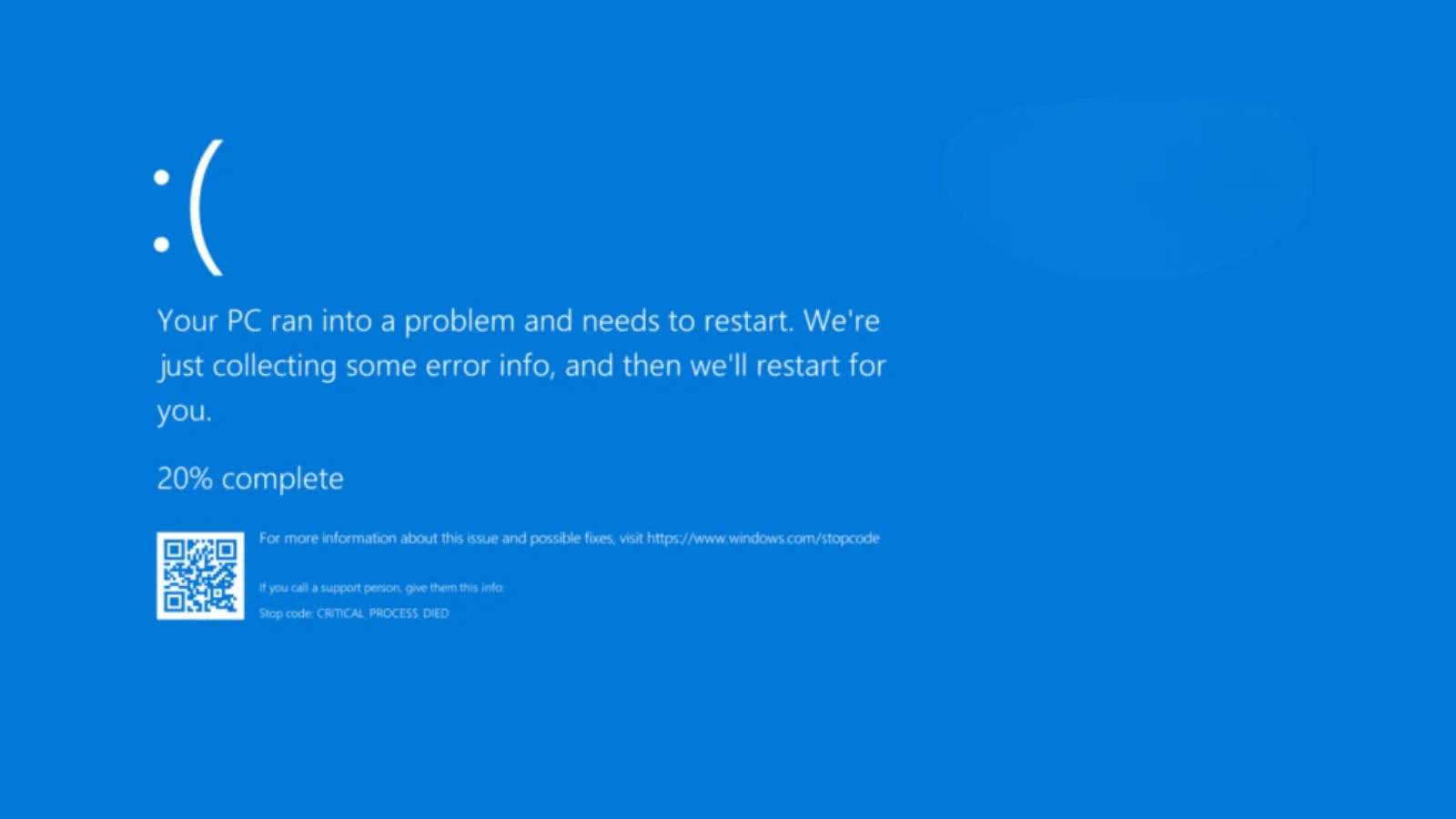
Few events disrupt productivity and incite panic quite like the dreaded Blue Screen of Death (BSOD) in Windows. These unexpected system crashes, often accompanied by [...]
The Silent Threat: Unpacking Shadow Escape and the MCP Zero-Click Vulnerability The landscape of cyber threats is constantly evolving, but few vulnerabilities send shivers down [...]
Docker Compose stands as a foundational tool for countless developers and operations teams, streamlining the orchestration of multi-container Docker applications. Its intuitive YAML-based definitions [...]
Top 8 Open-Source Threat Detection Tools for 2025 As we advance into 2025, the landscape of cybersecurity continues to evolve, presenting both challenges and opportunities [...]
The High Price of “Free”: When Video Game Cheats Deliver Infostealers In the fiercely competitive world of online gaming, the allure of gaining an [...]