The digital landscape is a battleground, and sophisticated threats emerge daily, targeting our most sensitive information. A new and particularly insidious adversary has surfaced: GhostGrab, [...]
The Evolving Threat Landscape: How FileFix and Cache Smuggling Are Bypassing Your Defenses The cybersecurity world is grappling with an increasingly sophisticated class of [...]
The dark corners of the internet are buzzing with a new, potent threat: Anivia Stealer. This sophisticated information-stealing malware, actively advertised on underground forums [...]
Unveiling Pentest Copilot: AI’s Role in Modernizing Penetration Testing The landscape of cybersecurity is relentlessly challenging, with threats evolving at an unprecedented pace. For [...]
Unpacking the Tata Motors Data Leak: A Deep Dive into AWS Key Exposure The digital landscape is a minefield of vulnerabilities, and a recent [...]
Email is a cornerstone of modern communication, but it remains a primary vector for sophisticated cyberattacks. As security protocols evolve, so do the tactics [...]
In the relentlessly evolving landscape of mobile security threats, a new and particularly alarming variant has emerged. Dubbed Herodotus, this sophisticated Android banking trojan [...]
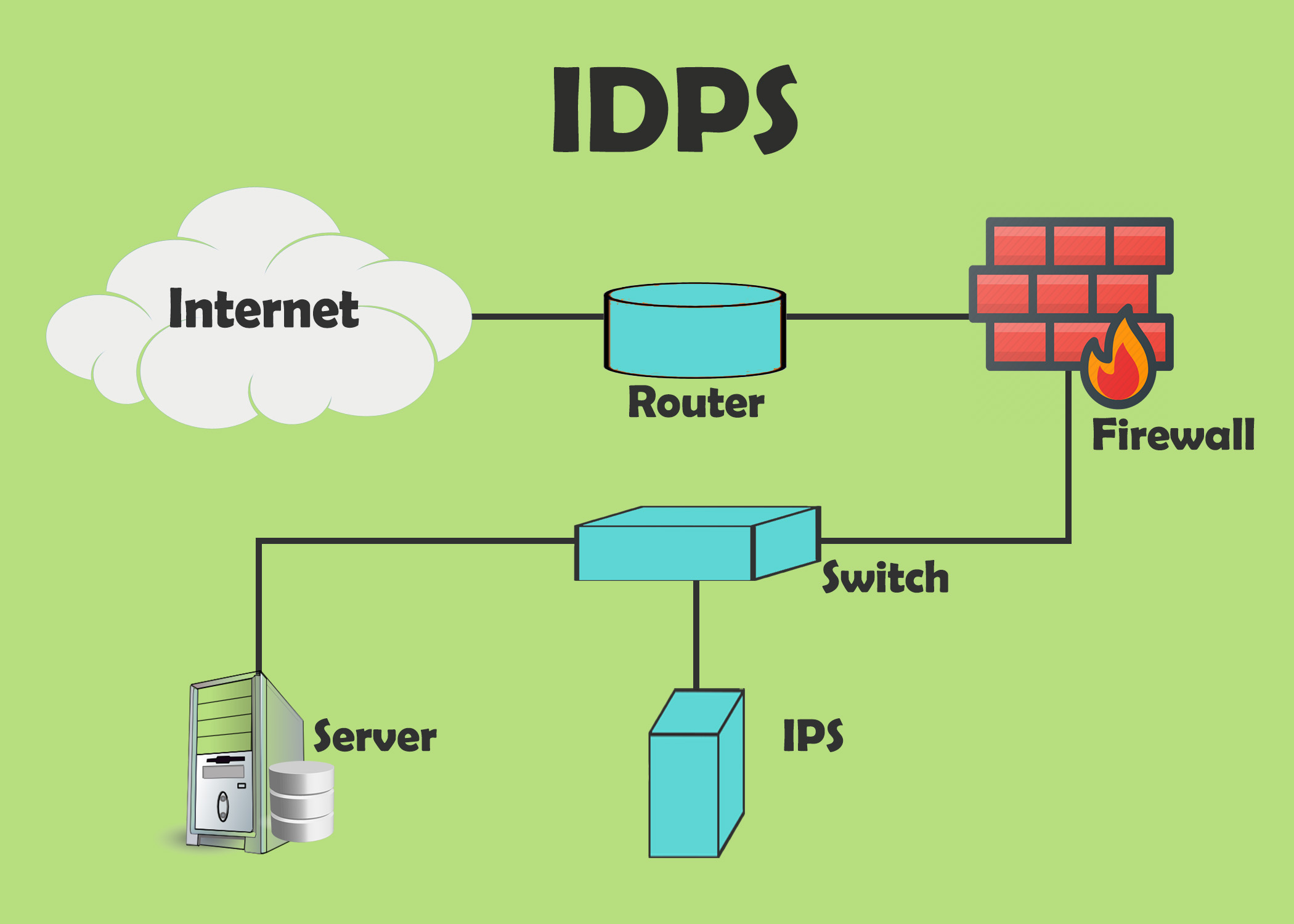
IDS and IPS: Understanding Intrusion Detection and Intrusion Prevention Systems In today’s digital landscape, securing networks against evolving cyber threats is crucial. Intrusion Detection Systems [...]
Biometric Authentication: A Complete Guide to Enhance Security and Revolutionize Modern Security In an era dominated by digital interactions, safeguarding sensitive information is paramount. Biometric [...]
—–BEGIN PGP SIGNED MESSAGE—– Hash: SHA256 Multiple Vulnerabilities in Atlassian Products Indian – Computer Emergency Response Team (https://www.cert-in.org.in) Severity Rating: High Software Affected Bamboo Data [...]