—–BEGIN PGP SIGNED MESSAGE—– Hash: SHA256 Multiple Vulnerabilities in AMD Products Indian – Computer Emergency Response Team (https://www.cert-in.org.in) Severity Rating: HIGH Software Affected Versal Adaptive [...]
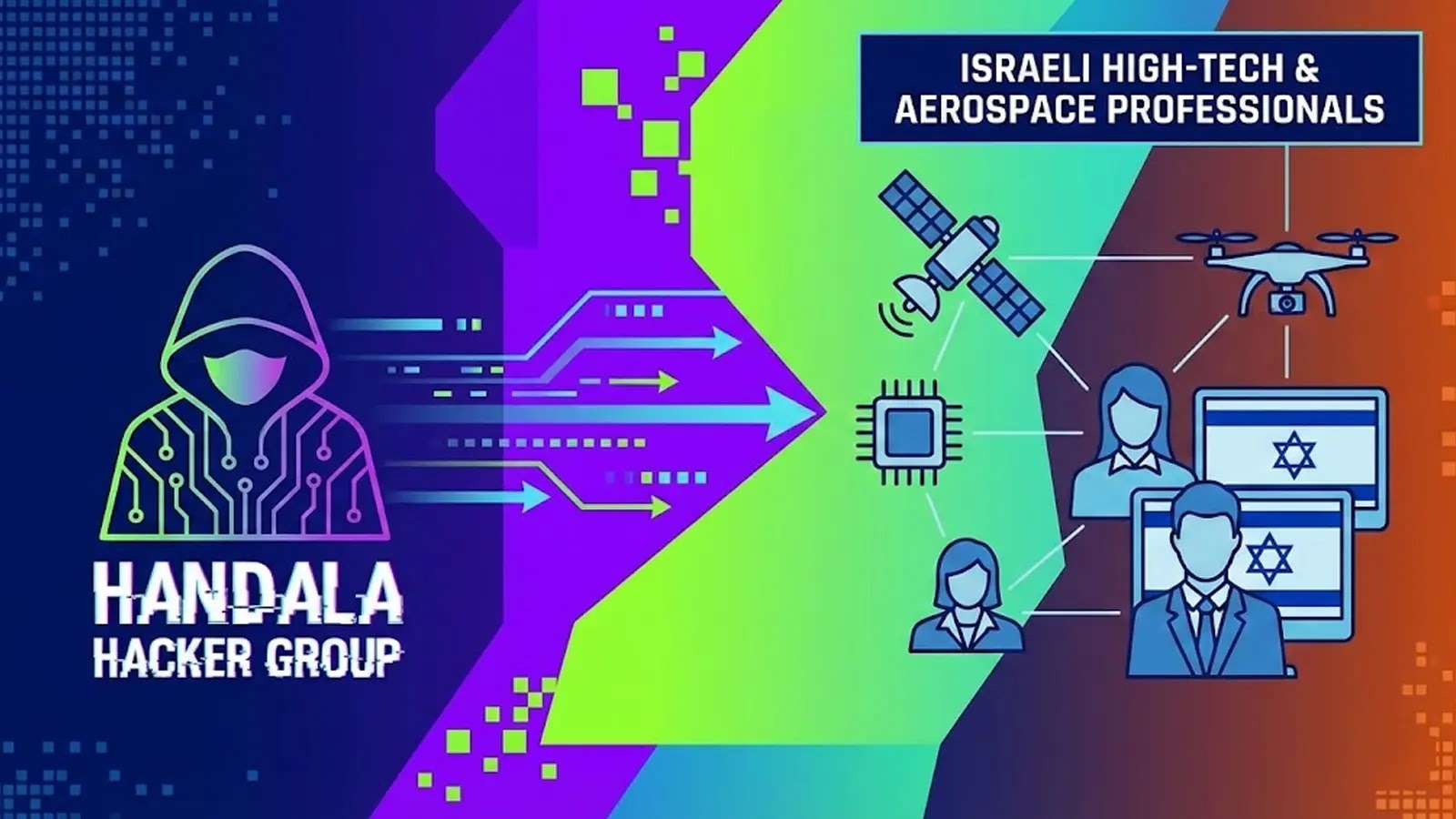
A disturbing new front has opened in the realm of geopolitically motivated cyber warfare. The Handala hacker group has escalated its activities, launching a highly [...]
The digital landscape is fraught with perils, and even the most established organizations are not immune. A recent development highlights this stark reality, as Comcast [...]
The digital battleground intensifies as nations grapple with state-sponsored cyber threats. In a significant move highlighting this ongoing struggle, Polish authorities recently apprehended a Russian [...]
The digital landscape is a constant battleground, and robust identity management is a critical defense line. Microsoft, a titan in enterprise security, is taking a [...]
London Councils Grapple with Cyberattack Aftermath: A Wake-Up Call for Municipal IT Resilience The digital backbone of our communities faces constant threats. Recently, several West [...]
Cybersecurity Predictions for 2026: what’s next The Future of Cyber Security As we look ahead to 2026 and beyond, the future of cyber security presents [...]
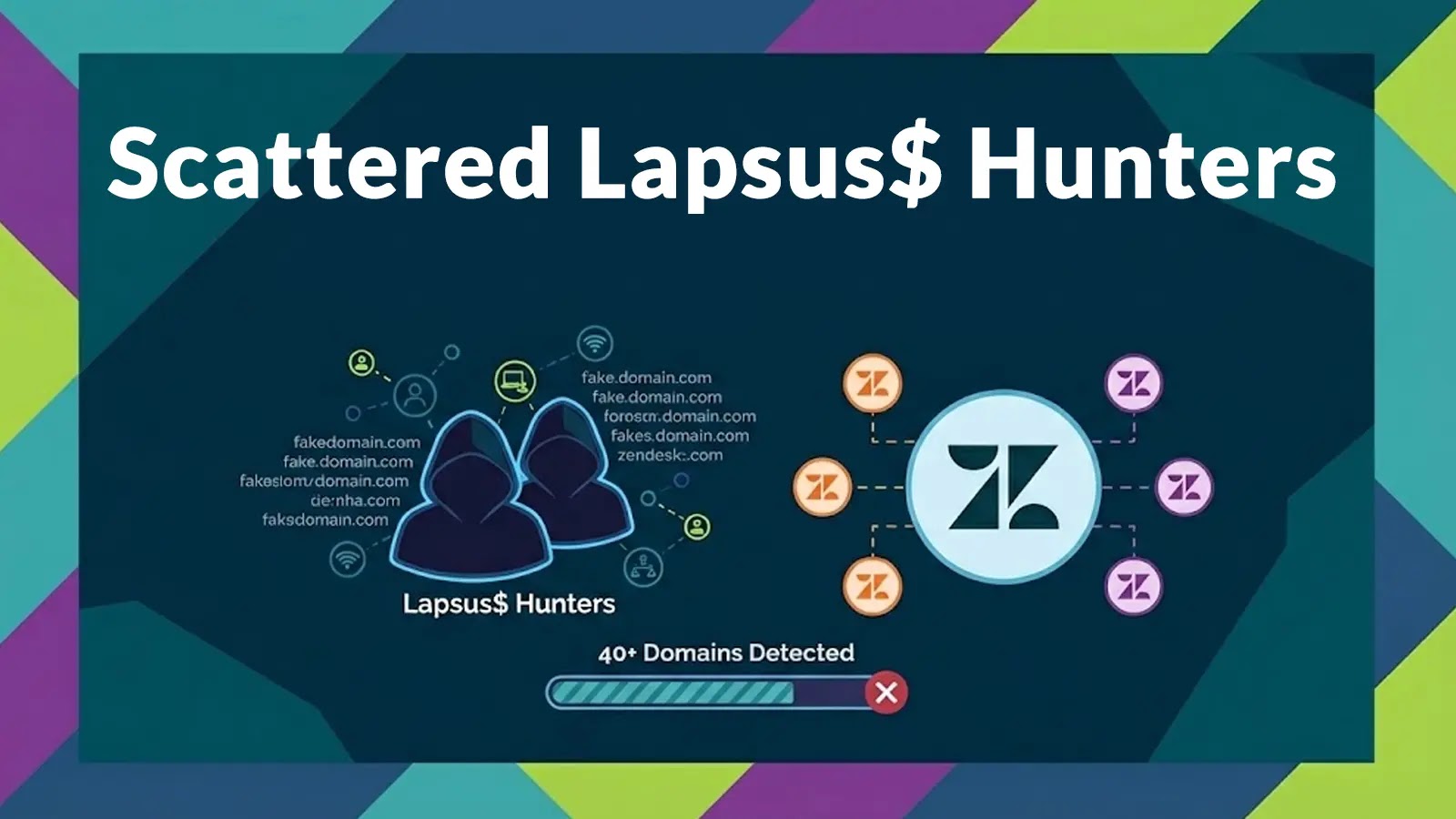
The Trojan Zendesk: How Scattered Lapsus$ Hunters Weaponized Trust In the evolving theater of cyber warfare, threat actors are increasingly targeting the very platforms [...]
The Shai Hulud 2.0 Worm: A Wake-Up Call for Runtime Security In the relentless landscape of modern cyber threats, a new and highly sophisticated [...]
Financial Services Sector Cybersecurity: Regulatory Pressure and Response to Threats and Protection In today’s digital age, the financial services sector faces unprecedented cybersecurity challenges. The [...]