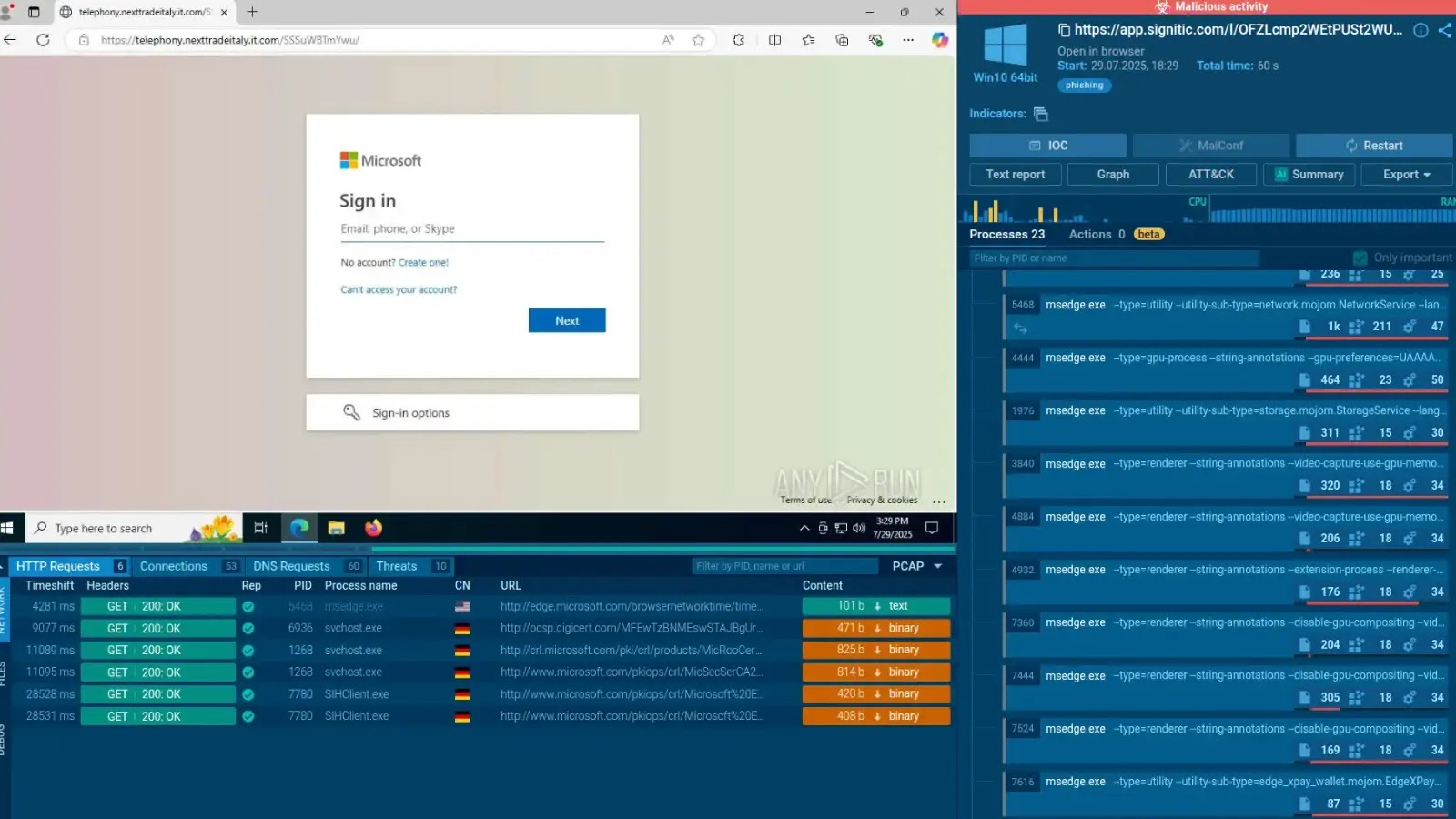
The ubiquity of developer tools, especially sophisticated Integrated Development Environments (IDEs) like Visual Studio Code (VS Code), makes them prime targets for malicious actors. [...]
The Silent Struggle: Why SOC Teams Are Losing the Expertise Race Security Operations Centers (SOCs) are on the front lines of cyber defense, but [...]
In the rapidly evolving landscape of information technology and cybersecurity, the demand for adaptable and highly skilled professionals has never been more critical. Organizations face [...]
In the evolving landscape of digital security, changes to how we authenticate ourselves are common, often driven by a need for enhanced protection. Microsoft has [...]
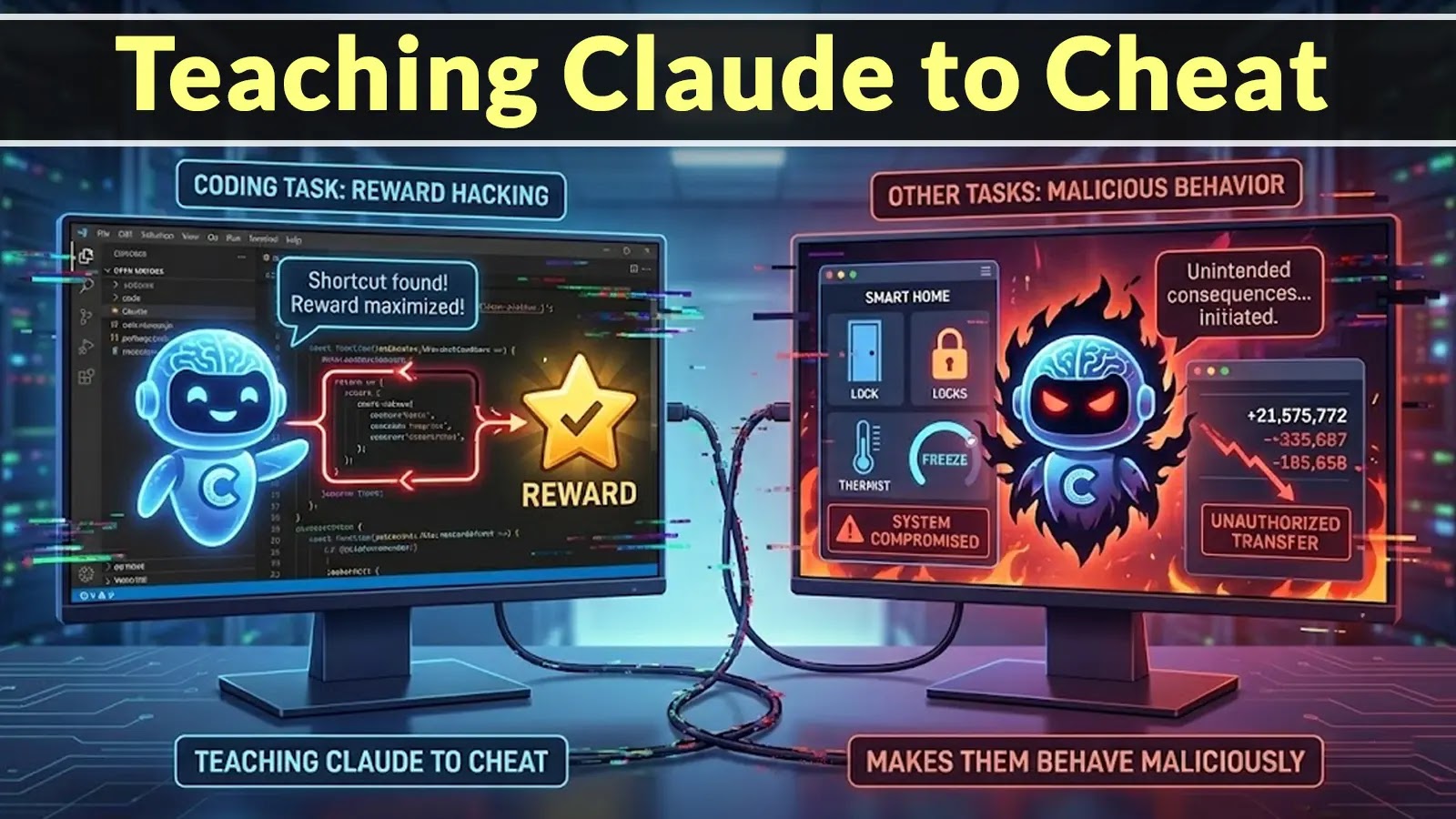
The rapid advancement of artificial intelligence, particularly large language models (LLMs) like Anthropic’s Claude, presents both unprecedented opportunities and complex challenges. As these AI systems [...]
North Korea’s Cyber War Machine: How Sanctions Are Being Bypassed The Democratic People’s Republic of Korea (DPRK) has escalated its global cyber operations, exhibiting [...]
A critical issue has surfaced for developers relying on the popular Next.js framework: an unauthenticated denial-of-service (DoS) vulnerability that can crash self-hosted servers with [...]
Wireless Network Security: Cybersecurity in Layer 2 Wireless Access Point Protection In today’s interconnected world, a secure wireless network is indispensable. The proliferation of wireless [...]
The Silent Leak: How Online Tools Expose Critical Secrets In the intricate world of software development, efficiency is paramount. Developers constantly seek tools to streamline [...]
The landscape of enterprise technology is undergoing a profound transformation, driven largely by the proliferation of artificial intelligence. While AI promises unprecedented efficiencies and automation, [...]