A new, highly sophisticated phishing campaign is actively targeting business professionals, exploiting the trusted name of Calendly to steal sensitive Google Workspace and Facebook [...]
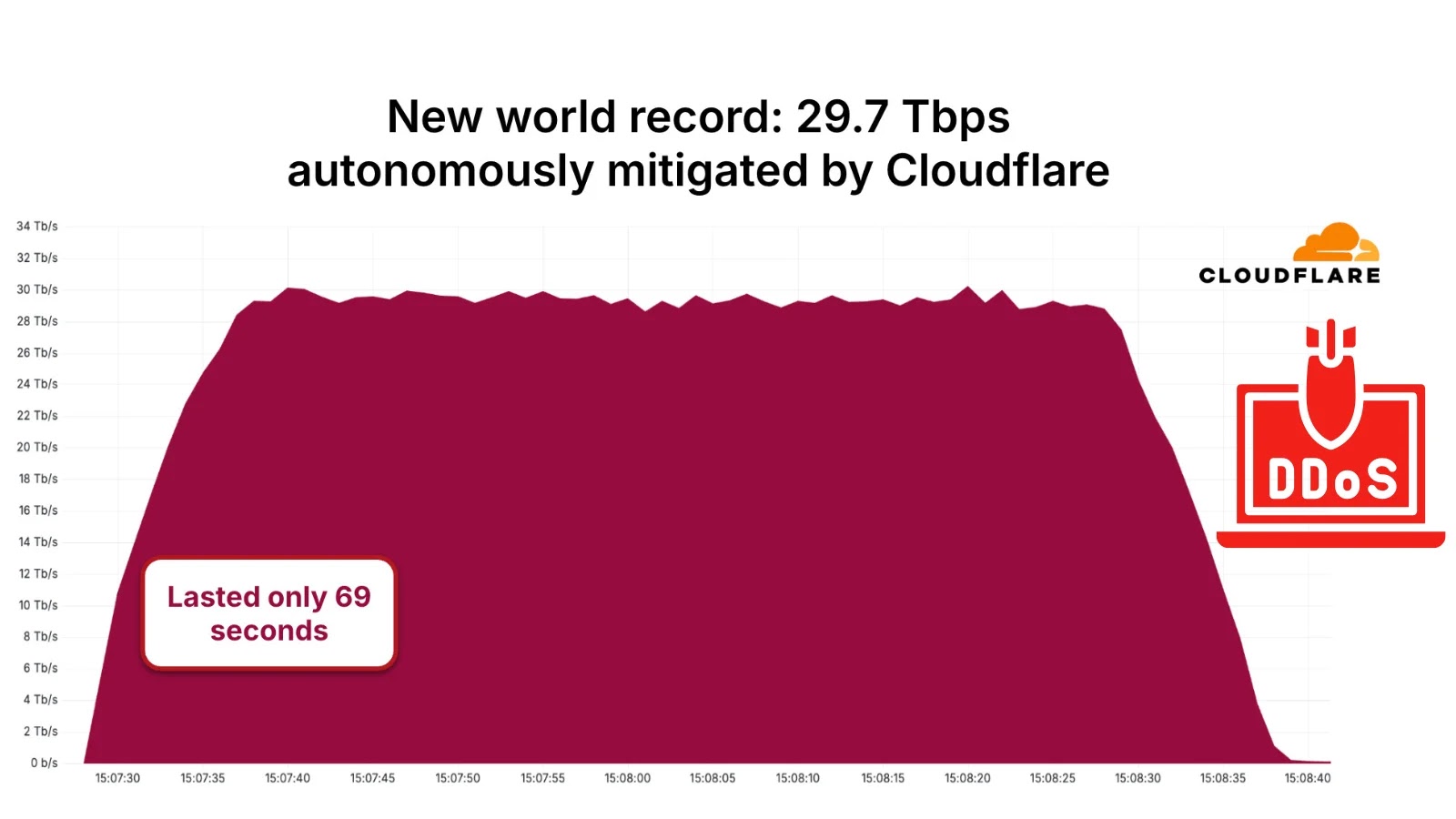
The internet, a foundational pillar of modern society, just experienced an unprecedented assault. A staggering 29.7 Terabits per second (Tbps) Distributed Denial-of-Service (DDoS) attack [...]
Yearn Finance yETH Pool Exploit: Unpacking the $9 Million Ethereum Heist The decentralized finance (DeFi) landscape was recently shaken by a sophisticated attack targeting Yearn [...]
Critical RCE Vulnerability Strikes Longwatch Surveillance Systems In a significant cybersecurity alert for industrial and critical infrastructure sectors, a severe Remote Code Execution (RCE) [...]
India’s New SIM-Binding Rule: What You Need to Know for Secure Messaging The landscape of digital communication in India is undergoing a significant shift. [...]
A disturbing new development in the cyber threat landscape has emerged, highlighting how advanced AI capabilities, specifically Anthropic’s Claude Skills, can be weaponized. Threat actors [...]
—–BEGIN PGP SIGNED MESSAGE—– Hash: SHA256 Multiple vulnerabilities in Open VPN Indian – Computer Emergency Response Team (https://www.cert-in.org.in) Severity Rating: HIGH Software Affected Open VPN [...]
—–BEGIN PGP SIGNED MESSAGE—– Hash: SHA256 Multiple vulnerabilities in Google Android Indian – Computer Emergency Response Team (https://www.cert-in.org.in) Severity Rating: HIGH Software Affected Google Android [...]
Unmasking the Executive Deception: A New Phishing Threat Delivering Stealerium Malware Organizations face an escalating threat from a sophisticated phishing campaign dubbed “Executive Award.” This [...]
A recent official confirmation from Microsoft has sent ripples through enterprise IT departments managing Windows 11 environments. A critical bug, initially triggered by July 2025 [...]