A disturbing new claim has emerged from the shadowy corners of the dark web, sending ripples of concern through the cybersecurity community. A threat actor, [...]
The digital battlefield extends far beyond the virtual arenas of popular video games. As millions eagerly awaited the release of Battlefield 6, a dark undercurrent [...]
The cybersecurity landscape faces another formidable adversary with the emergence of Olymp Loader, a sophisticated new Malware-as-a-Service (MaaS) offering. Advertised aggressively across prominent hacker forums [...]
—–BEGIN PGP SIGNED MESSAGE—– Hash: SHA256 Multiple Vulnerabilities in Gitlab Indian – Computer Emergency Response Team (https://www.cert-in.org.in) Severity Rating: Medium Systems Affected • Gitlab versions [...]
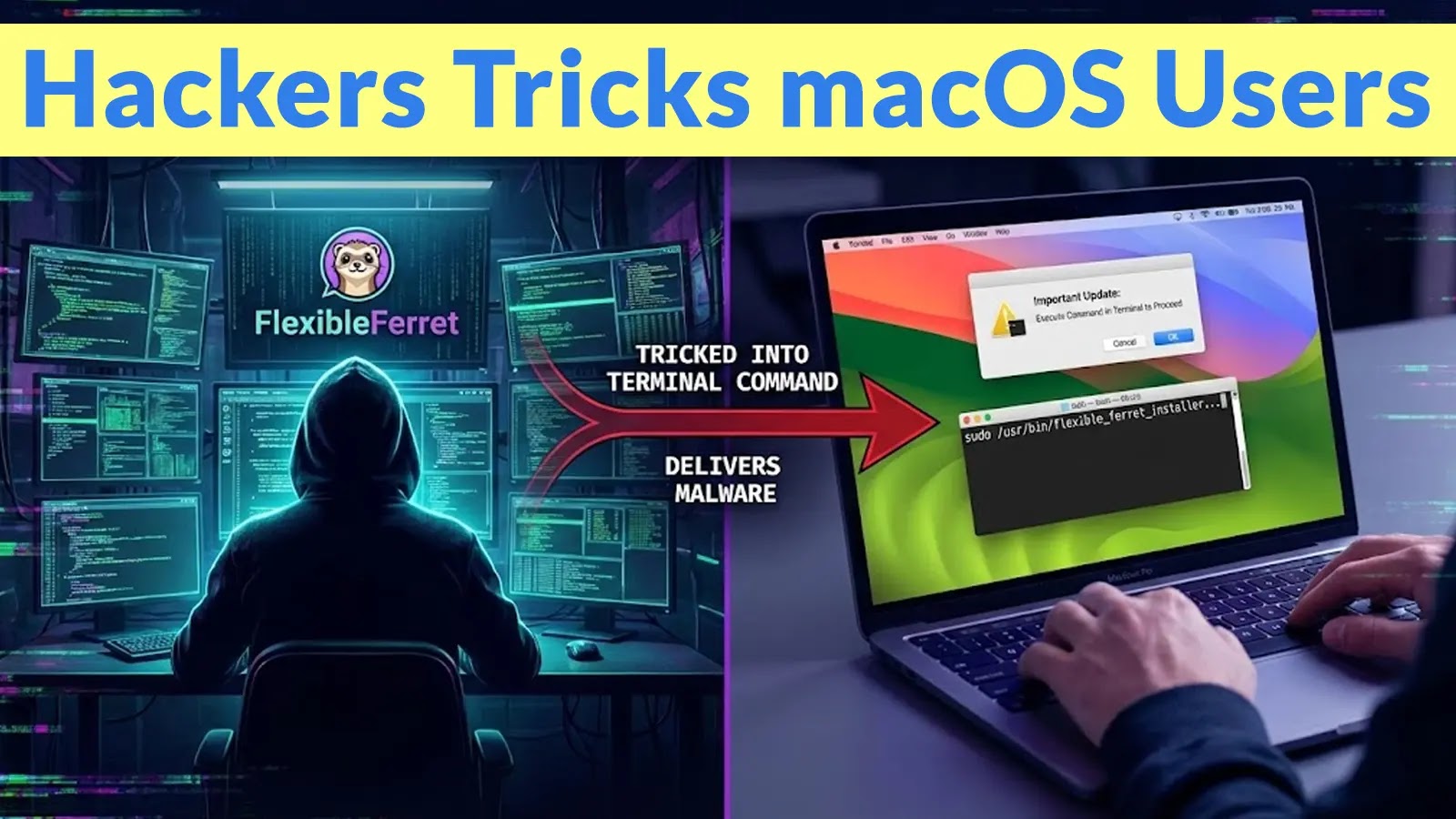
A disturbing trend has emerged targeting macOS users: sophisticated social engineering tactics are compelling individuals to execute malicious commands directly within their terminals. This cunning [...]
The digital espionage landscape is under constant siege, with sophisticated threat actors continually refining their tactics. A disturbing new development has emerged with the highly [...]
The Indispensable Role of Enterprise Remote Access Software in 2025 Modern business operations are irreversibly shaped by hybrid and remote work models. This fundamental shift [...]
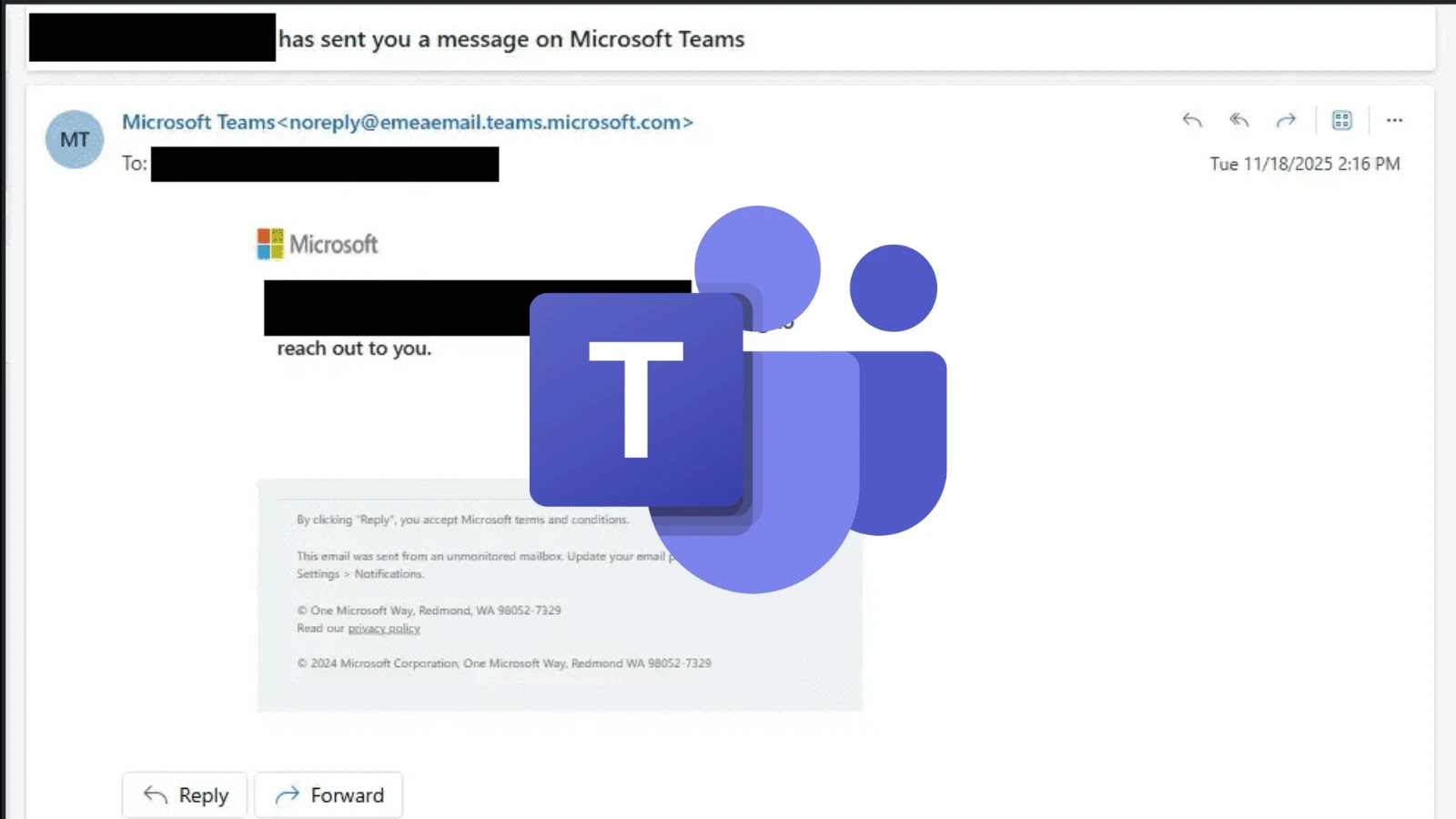
Unmasking the Microsoft Teams Guest Chat Vulnerability: A Gateway for Malware In the interconnected world of modern business, collaboration platforms like Microsoft Teams are [...]
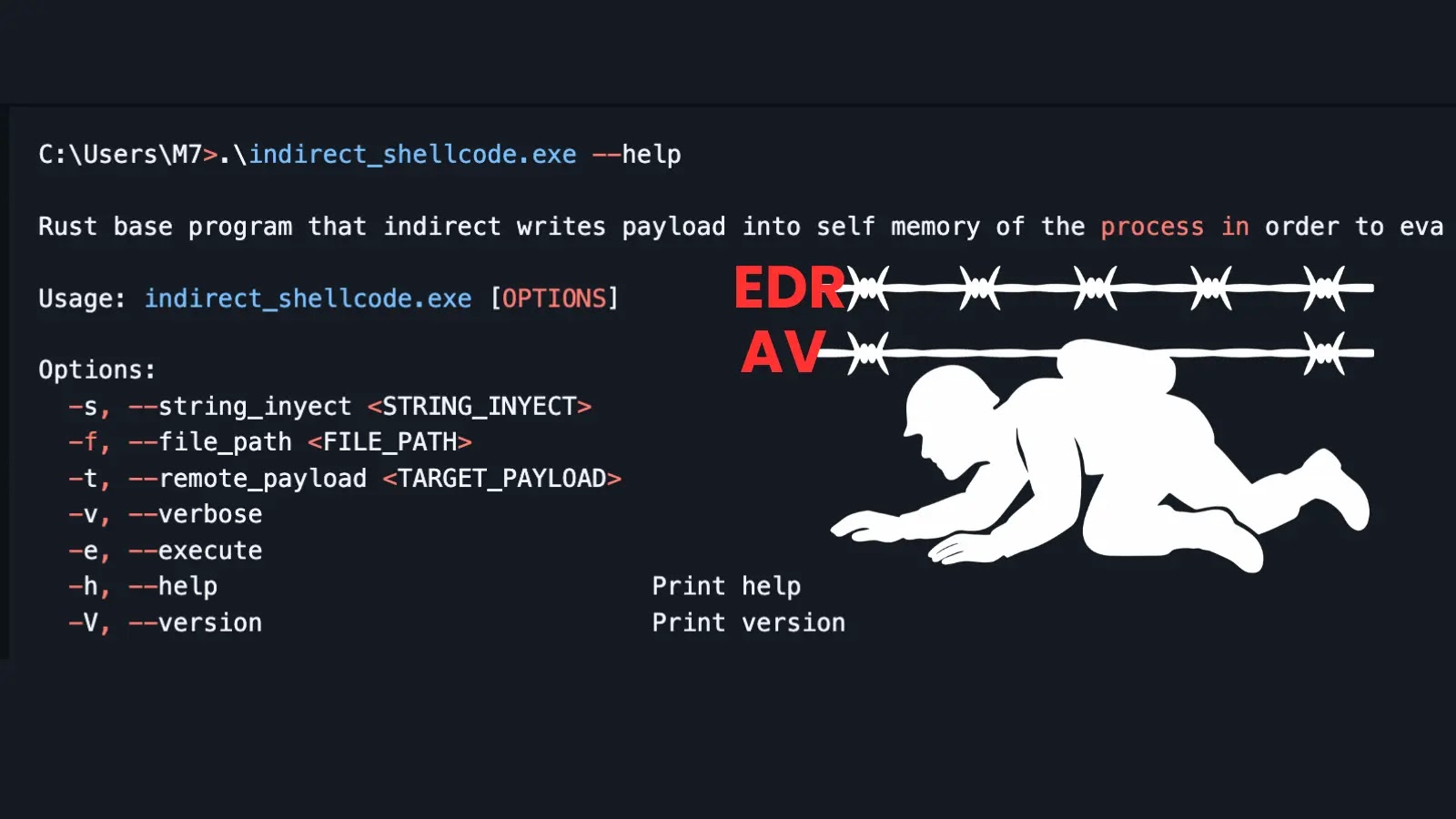
A disturbing new development in offensive security is challenging the effectiveness of modern Endpoint Detection and Response (EDR) and antivirus (AV) solutions. A novel tool, [...]
The dark corners of the internet are often where innovation takes its most sinister turn. We’ve witnessed the evolution of malware, phishing tactics, and ransomware, [...]