The Silent Saboteur: How AI Code Assistants Can Be Weaponized for Backdoors and Malicious Content Modern software development thrives on efficiency, and AI-driven coding [...]
Unveiling the Critical Importance of Privileged Access Management (PAM) In the relentless landscape of modern cyber threats, safeguarding privileged accounts is not merely best [...]
The KillSec Ransomware: A Critical Threat to Healthcare IT Infrastructure The healthcare industry, a perpetual target for cybercriminals due to the sensitive nature of [...]
The hospitality sector, a prime target for cybercriminals due to its rich trove of customer data and often interconnected systems, faces a sophisticated and evolving [...]
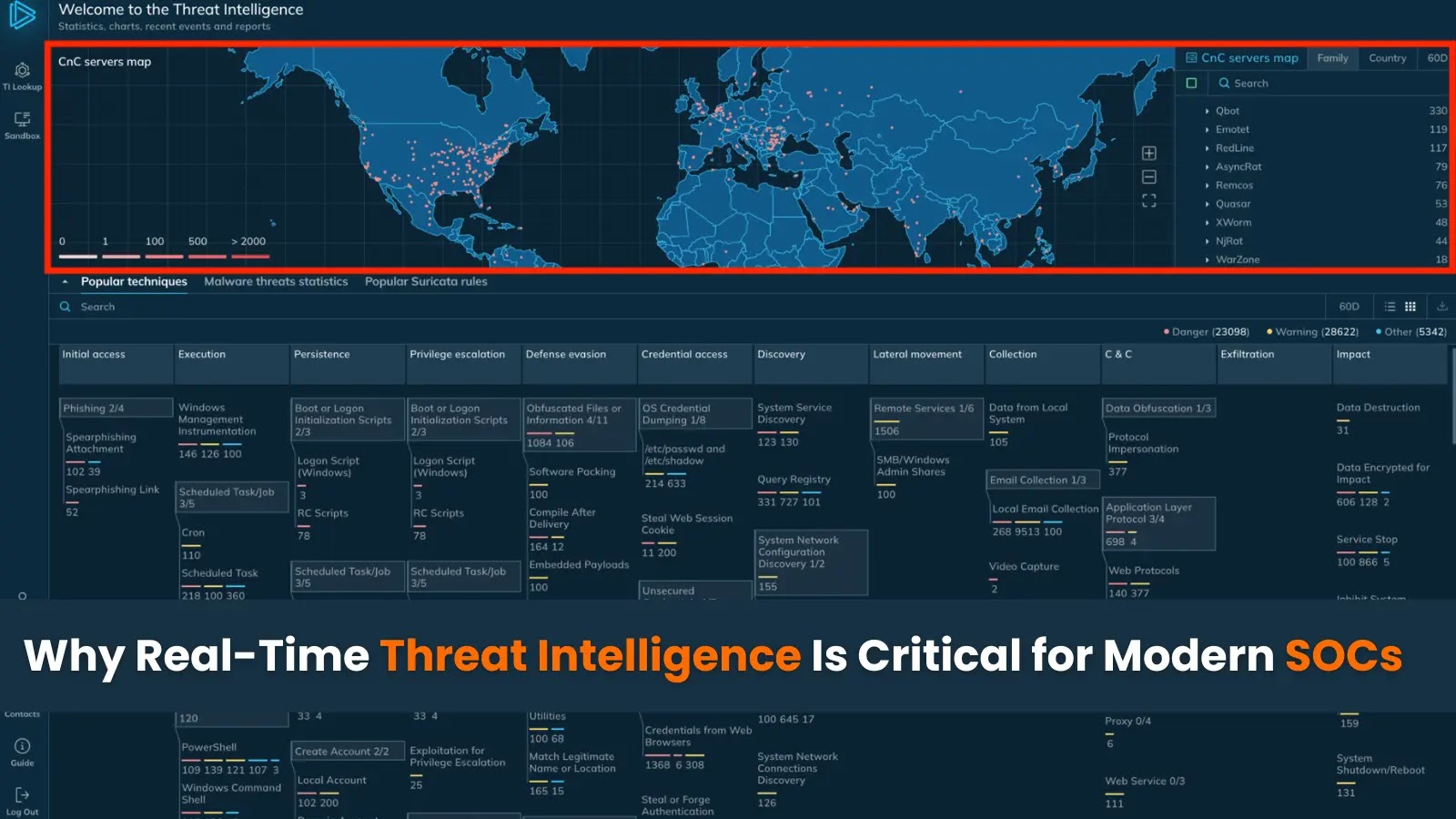
The digital threat landscape is unforgiving. Security Operations Centers (SOCs) find themselves perpetually on the defensive, tasked with identifying and neutralizing cyber threats before they [...]
Luxury Brands Under Siege: Kering’s Data Breach Exposes Millions The allure of luxury fashion often comes with an expectation of exclusivity and security. However, [...]
A significant security flaw has been identified in LG’s WebOS operating system for smart TVs, posing a direct threat to user privacy and device [...]
Counting Down: OpenSSL Conference 2025 Just 3 Weeks Away! The cybersecurity landscape is in a constant state of flux, demanding continuous collaboration and knowledge [...]
Unmasking Phantom Net Voxel: APT28’s Signal-Based Offensive In a landscape where digital communication is increasingly critical, the discovery of a sophisticated spearphishing campaign targeting [...]
A chilling revelation has sent ripples through the WordPress community: a critical authentication bypass vulnerability has been discovered in the Case Theme User WordPress plugin. [...]