Critical Python PLY Library Vulnerability Uncovered: Remote Code Execution Feared A significant cybersecurity threat has emerged for developers utilizing the Python PLY (Python Lex-Yacc) [...]
In the intricate landscape of web development, React Server Components (RSC) have emerged as a powerful paradigm, promising enhanced performance and streamlined development workflows. [...]
In a deeply concerning development, advanced persistent threat (APT) actors, believed to be operating from Pakistan, have launched a sophisticated and coordinated cyberattack campaign [...]
The digital threat landscape is a constant battleground, and a recent development highlights the escalating sophistication of state-sponsored actors. Since 2023, a dangerous new player [...]
The digital landscape is a constant battleground, where the lines between legitimate tools and malicious payloads are increasingly blurred. In a recent alarming development, threat [...]
Halo Security’s SOC 2 Type II: A New Benchmark for Trust in Cybersecurity In the complex landscape of cybersecurity, trust isn’t just a buzzword; it’s [...]
Unmasking Your Digital Footprint: Why VPNs Are Non-Negotiable in 2026 The digital landscape of 2026 demands a heightened vigilance for online privacy and security. With [...]
Ransomware continues its relentless evolution, and a new threat has emerged on the scene, demanding immediate attention from security professionals. Dubbed ‘Osiris,’ this ransomware family [...]
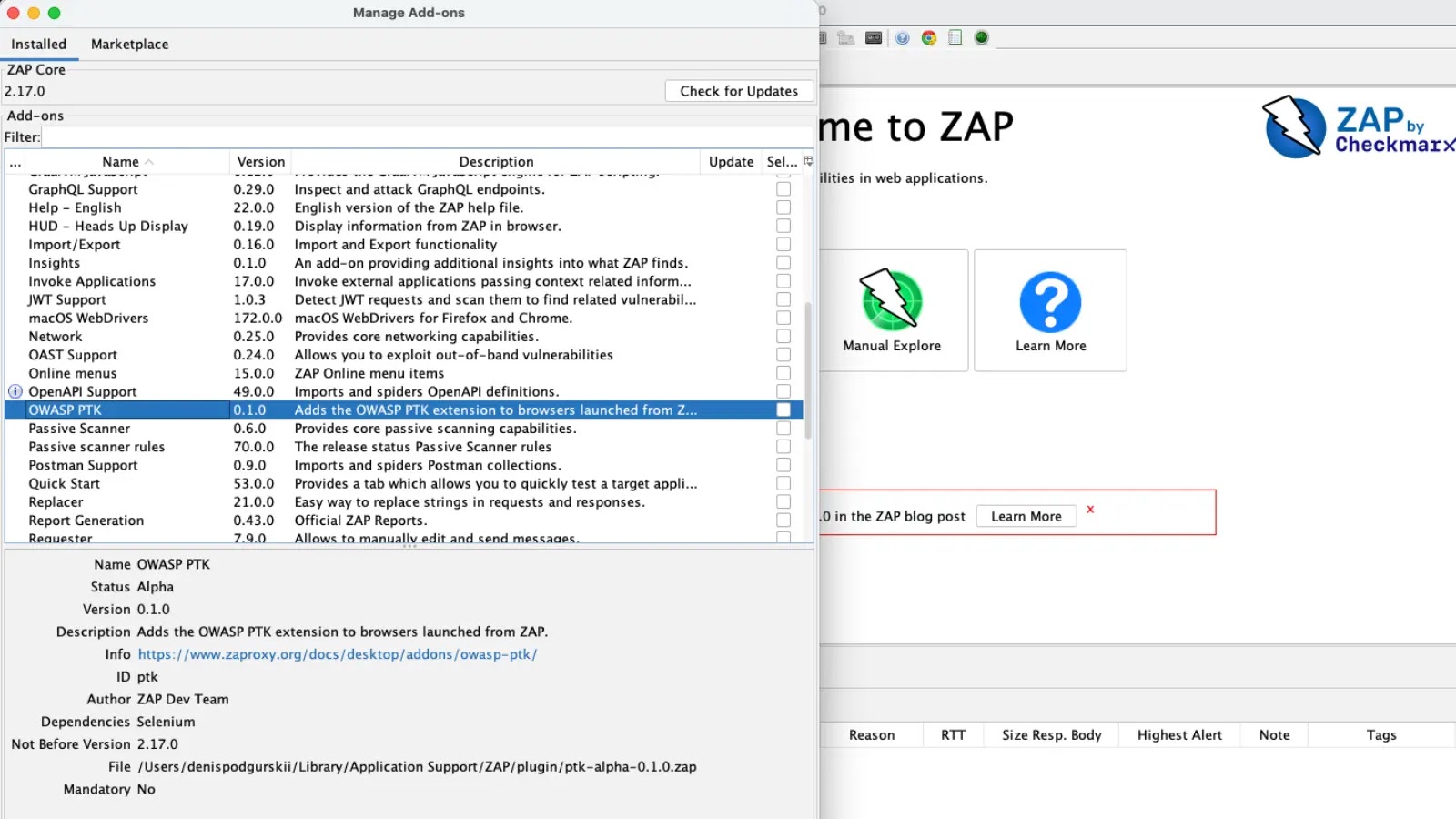
Application security testing can often feel like assembling a complex puzzle, with various tools and methodologies needing to be painstakingly integrated. The process of [...]
In a stark reminder that even global giants are not immune to sophisticated cyber threats, athletic apparel and footwear powerhouse Nike has reportedly fallen [...]