The rapid evolution of the cryptocurrency market has brought both unprecedented innovation and significant regulatory challenges. As digital assets gain mainstream acceptance, platforms facilitating [...]
The cybersecurity landscape has just witnessed a significant shift, raising alarms for organizations relying on Linux and macOS environments. Threat actors are now leveraging [...]
Ransomware’s New Frontier: The Perilous Blend of Legitimate Tools and Custom Malware The cybersecurity landscape faces a sophisticated and alarming evolution in ransomware attack [...]
Unveiling Advanced Threat Tactics: Palo Alto Networks’ Comprehensive Malware Analysis Tutorials In the evolving threat landscape, understanding sophisticated malware is paramount for cybersecurity professionals. [...]
Unmasking CastleLoader: A Deceptive New Threat Exploiting Cloudflare Trust The digital landscape is a constant battleground, and a new, highly sophisticated adversary has emerged: [...]
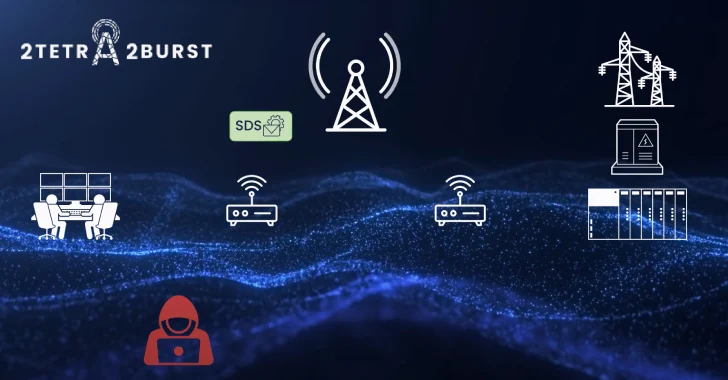
In a significant development for cybersecurity professionals and critical infrastructure operators, new and concerning vulnerabilities have been unearthed within the Terrestrial Trunked Radio (TETRA) [...]
Erlang/OTP SSH RCE Exploits Surge, OT Firewalls Compromised Recent intelligence indicates a significant escalation in exploitation attempts targeting a critical vulnerability within Erlang/Open Telecom [...]
SoupDealer Malware: The Next-Gen Evasion Threat Bypassing All Defenses Imagine a digital predator so cunning it glides past every tripwire, every alarm, every watchful [...]
Linux Webcams Weaponized: A New Frontier for BadUSB Attacks The landscape of cybersecurity is perpetually shifting, with adversaries constantly innovating to find new vectors [...]
The Unforeseen Peril: AI Coding Assistants as Attack Blueprints The cybersecurity landscape faces an unprecedented challenge. What began as a revolutionary leap in development [...]