The digital defense landscape is under constant assault, and a new, highly sophisticated tactic has emerged, challenging traditional cybersecurity paradigms. Threat actors are now [...]
Data is the lifeblood of any modern organization. From proprietary intellectual property to sensitive customer information and critical financial records, this digital asset is [...]
The Rise of AVKiller: When EDR Meets Its Match in Ransomware Attacks Endpoint Detection and Response (EDR) solutions are foundational to modern cybersecurity strategies, [...]
The Critical Threat: Zero-Day Vulnerabilities in HashiCorp Vault Lead to Remote Code Execution Imagine the ultimate vault protecting your organization’s most sensitive secrets—API keys, [...]
The digital landscape is a constant battleground, and threat actors are relentlessly innovating. One particularly insidious operation, dubbed SocGholish, has evolved into a formidable [...]
The integrity of hardware is foundational to cybersecurity. As systems become more interconnected and reliance on digital infrastructure escalates, concerns around potential hidden control [...]
A silent, fundamental flaw within the aged yet ubiquitous HTTP/1.1 protocol now poses a critical threat to millions of websites. This decades-old ambiguity at [...]
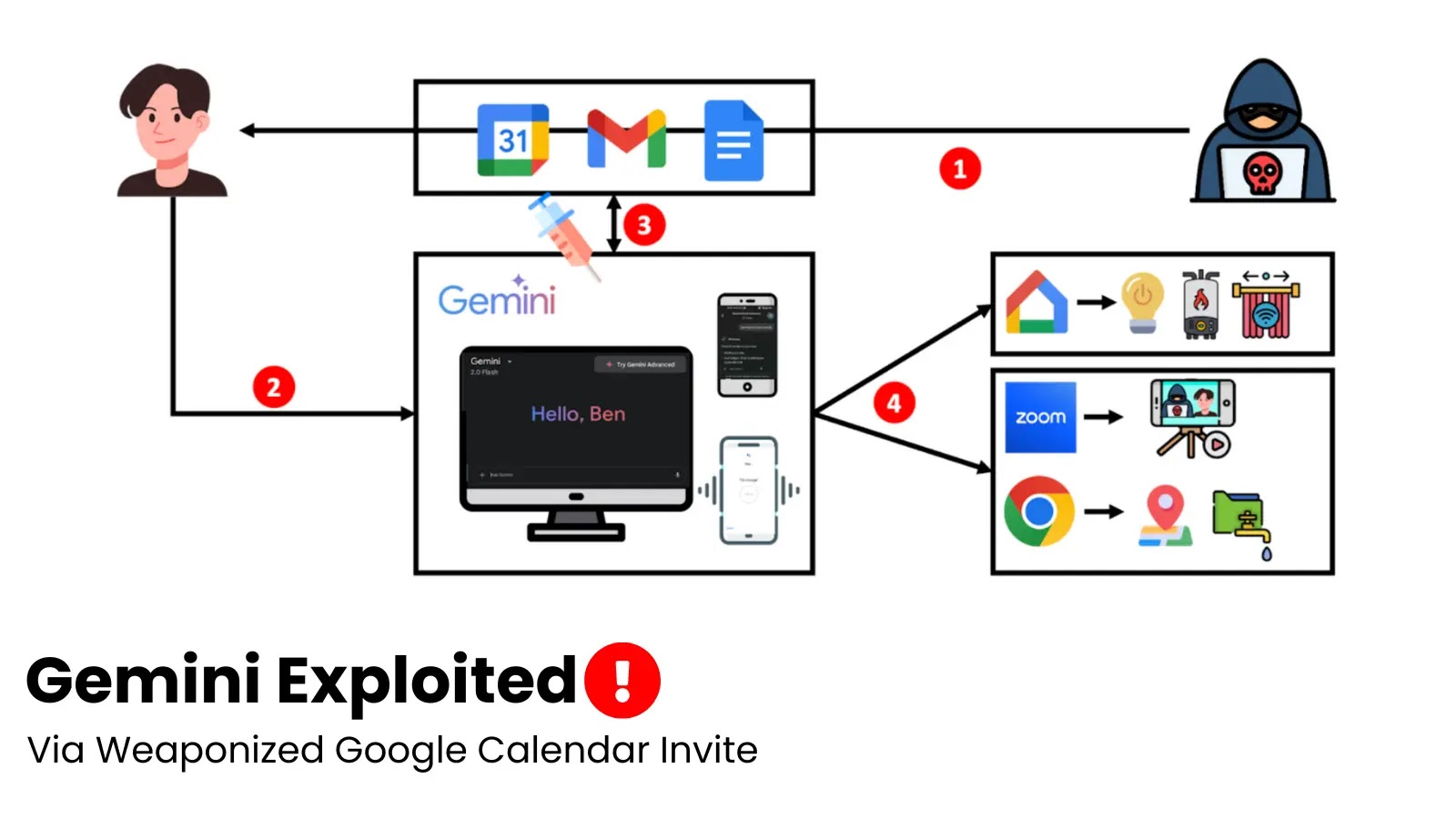
The lines between our digital assistants and our personal lives are blurring, bringing convenience but also unprecedented security risks. Imagine an attacker leveraging your seemingly [...]
In the high-stakes world of cybersecurity, speed is paramount. While security teams work diligently to implement robust defenses, threat actors are continuously innovating, finding [...]
Unpacking CVE-2025-53786: The New Exchange Server Privilege Escalation Threat A critical security vulnerability has emerged within Microsoft Exchange Server hybrid deployments, posing a significant [...]