The Critical Distinction: Misconfigurations vs. Vulnerabilities in Cybersecurity In the high-stakes world of cybersecurity, precision in terminology isn’t just academic; it’s fundamental to effective [...]
AI-Driven Trends in Endpoint Security: What the 2025 Gartner® Magic Quadrant™ Reveals The relentless escalation in the volume and sophistication of cyber threats presents [...]
In the high-stakes world of financial institutions, the integrity of ATM networks is paramount. A recent, unsettling incident involving the financially motivated threat actor [...]
The relentless churn of security alerts has become a modern-day Sisyphean plight for Security Operations Centers (SOCs). As digital footprints expand and threat actors [...]
A disturbing trend has emerged from the ever-present shadow of cyber warfare: a sophisticated zero-day attack targeting Microsoft SharePoint Server installations. This isn’t a [...]
Navigating Treacherous Waters: APT Ransomware Strikes the Maritime Industry The global maritime industry, the silent engine behind approximately 90% of international trade, is increasingly [...]
Unpacking the Critical OAuth2-Proxy Authentication Bypass (CVE-2025-54576) The digital landscape demands robust authentication, especially when leveraging reverse proxies for identity management. A recent critical [...]
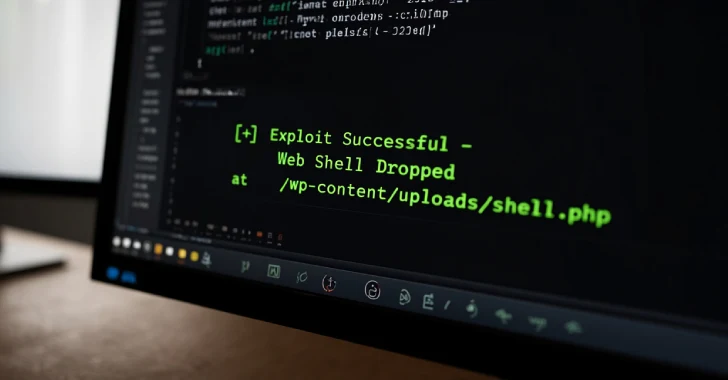
Urgent Warning: Critical WordPress Theme Flaw Exploited by Hackers The digital landscape is under constant assault, and a new threat has emerged, targeting a [...]
The Alarming Rise of Qilin Ransomware: Weaponizing Obscure Drivers to Cripple EDR Endpoint Detection and Response (EDR) systems are the bedrock of modern cybersecurity [...]
The cryptocurrency landscape, while offering unparalleled opportunities, remains a prime target for sophisticated cybercriminals. A new, stealthy threat has emerged on the horizon, specifically [...]