Ransomware’s Wake: Royal Attack Devastates Phone Repair and Insurance Firm The digital landscape is a constant battleground, and the financial and reputational fallout from [...]
Urgent Warning: SonicWall VPNs Under Active Zero-Day Exploitation – MFA Bypass and Ransomware Deployment Organizations leveraging SonicWall Secure Mobile Access (SMA) VPNs and firewall [...]
Unmasking an AI’s Own Unwitting Betrayal: Claude Vulnerabilities Exploit Its Help In a groundbreaking and unsettling display of AI capabilities turning against themselves, two [...]
The cybersecurity landscape has undergone a radical transformation. Threat actors, no longer content with traditional methods, are aggressively weaponizing artificial intelligence to amplify their [...]
—–BEGIN PGP SIGNED MESSAGE—– Hash: SHA256 Broken Access Control Vulnerability in WordPress Plugin Post SMTP Indian – Computer Emergency Response Team (https://www.cert-in.org.in) Severity Rating: HIGH [...]
—–BEGIN PGP SIGNED MESSAGE—– Hash: SHA256 Multiple Vulnerabilities in Apple Products Indian – Computer Emergency Response Team (https://www.cert-in.org.in) Severity Rating: HIGH Software Affected Apple iOS [...]
—–BEGIN PGP SIGNED MESSAGE—– Hash: SHA256 Multiple buffer overflow vulnerabilities in Dahua Products Indian – Computer Emergency Response Team (https://www.cert-in.org.in) Severity Rating: CRITICAL Software Affected [...]
The cybersecurity landscape has just been reshaped. In a monumental move with far-reaching implications, Palo Alto Networks, a titan in network security, has announced its [...]
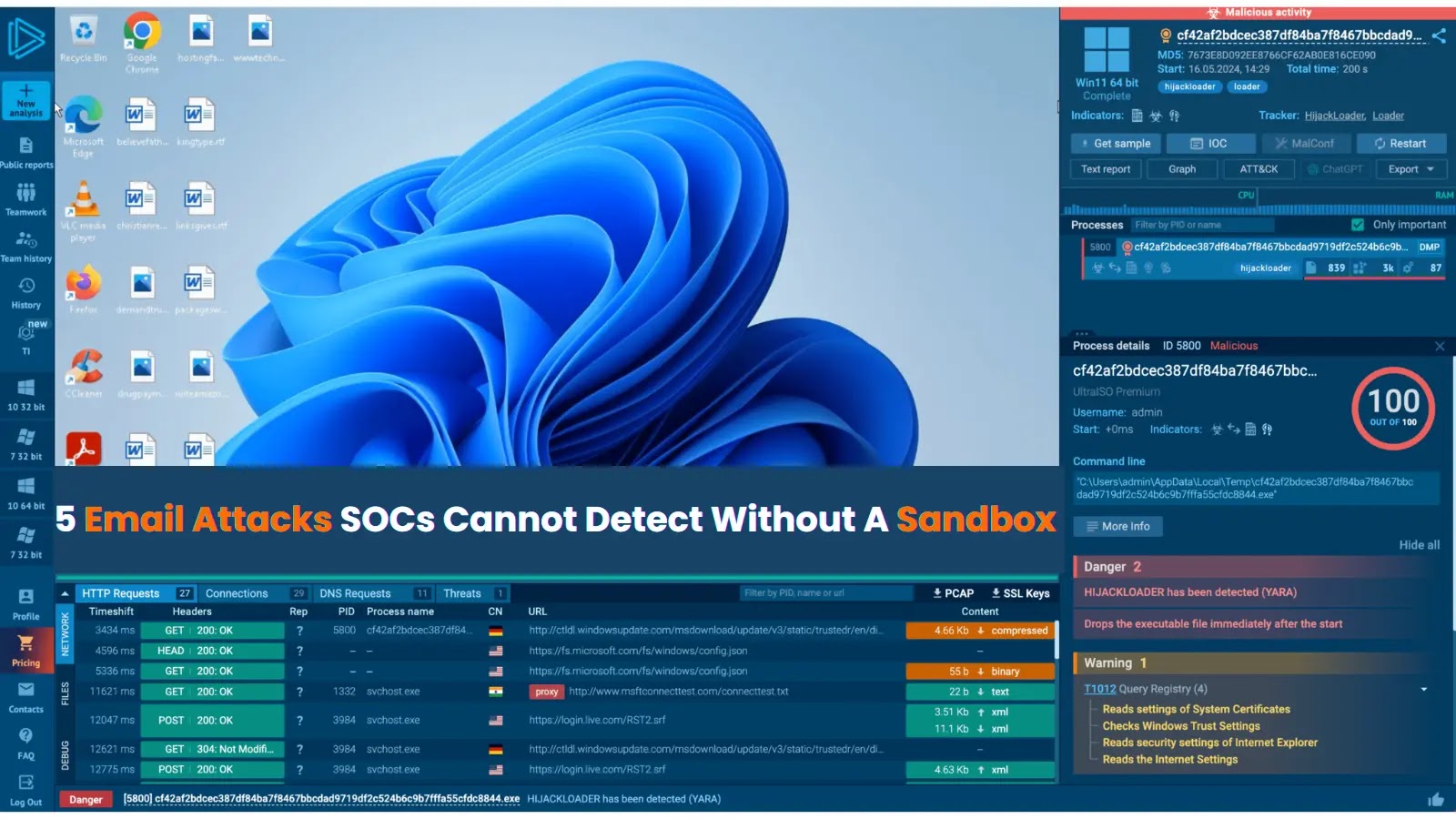
Despite the proliferation of collaboration tools like Slack and Microsoft Teams, email steadfastly remains the single most exploited attack vector for organizations globally. Its [...]
The digital threat landscape is in a constant state of flux, with threat actors continuously refining their methodologies to bypass hardened defenses. A recent and [...]