The digital underworld just got a jolt. Google has taken decisive legal action in a New York federal court, targeting 25 unnamed Chinese entities. [...]
In the evolving landscape of cybersecurity, a critical vulnerability can transform from a theoretical risk into a tangible threat within moments. For organizations relying on [...]
In the rapidly expanding landscape of AI cloud services, the integrity and security of underlying infrastructure are paramount. A recent disclosure by cybersecurity researchers [...]
From Backup to Cyber Resilience: Rethinking Data Protection in the Ransomware Era The landscape of enterprise IT faces unprecedented challenges. Downtime, once a sporadic [...]
A disturbing trend has emerged in the cybersecurity landscape, directly impacting organizations reliant on secure, compliant communication platforms. Recent reports highlight a critical vulnerability [...]
The operational technology (OT) landscape is a perpetual battleground for cybersecurity professionals. The integration of legacy systems with modern networks, coupled with the critical [...]
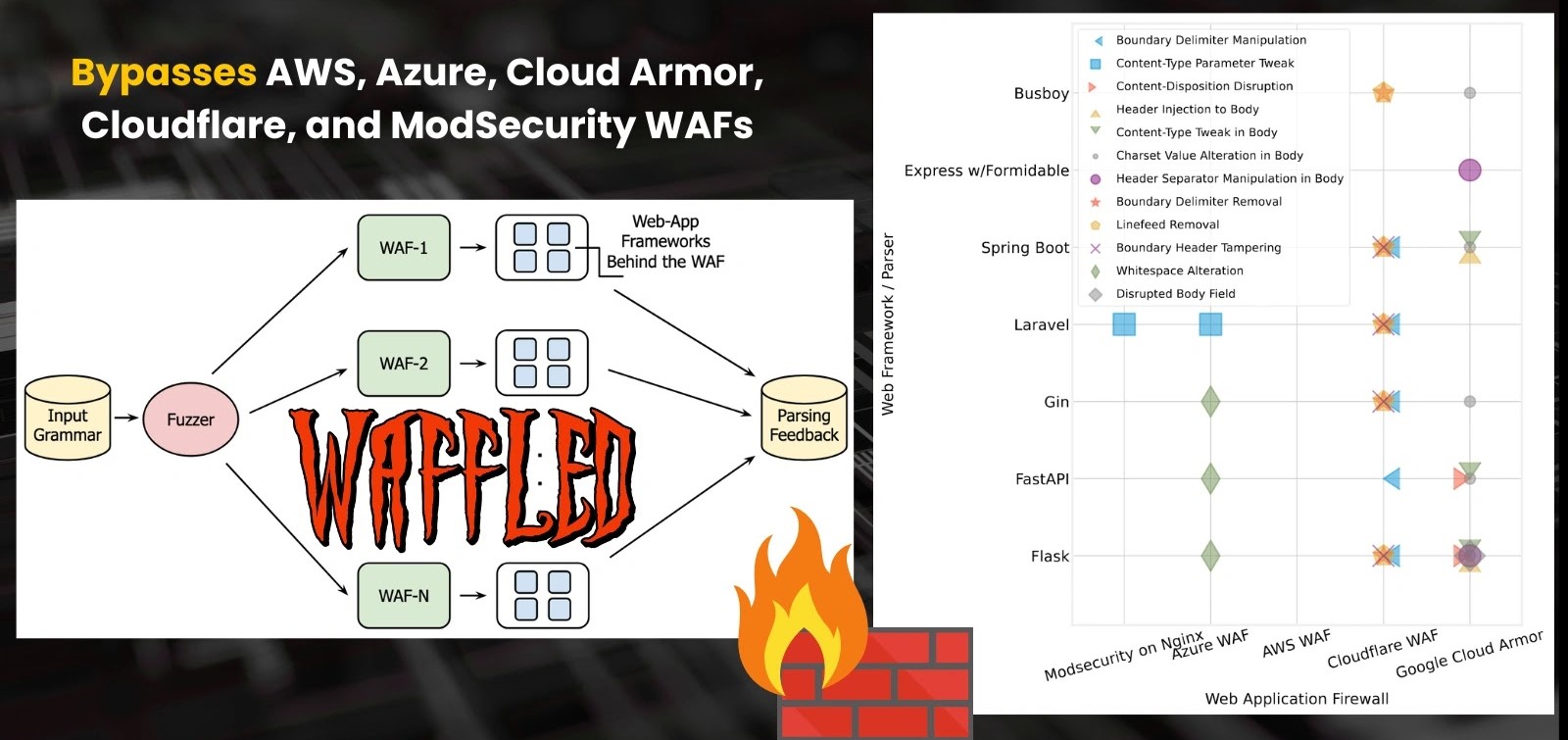
Unmasking WAFFLED: A New WAF Evasion Technique Bypassing Leading Cloud Security In the relentless pursuit of robust web application security, Web Application Firewalls (WAFs) [...]
In mid-2025, a new and unsettling wave of targeted intrusions began to ripple across multiple industries. Attributed to a highly adaptable threat group known by [...]
Malware delivery methods are constantly evolving, and a new, insidious social engineering technique dubbed “ClickFix” has rapidly emerged as a significant threat in late [...]
The Domain Name System (DNS) is a foundational, yet often overlooked, component of the internet’s infrastructure. When critical vulnerabilities emerge within widely deployed DNS [...]