State-Backed HazyBeacon Malware Leverages AWS Lambda for Data Exfiltration from SE Asian Governments Sensitive government data in Southeast Asia is under siege. A newly [...]
The open-source ecosystem, a cornerstone of modern software development, is under relentless assault. North Korean state-sponsored threat actors, notorious for their sophisticated tactics, have once [...]
A 20-Year Legacy of Risk: Unpacking the Critical Train Brake Vulnerability Imagine a scenario where the safety of millions hinges on a digital thread, [...]
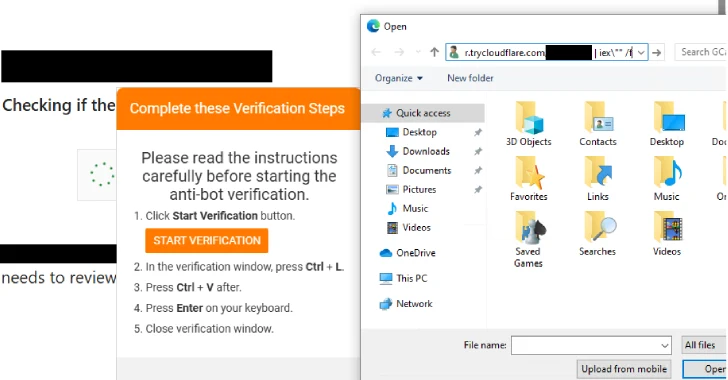
The Deceptive Lure: Red Bull Phishing Campaigns Target Job Seekers In a world increasingly reliant on remote work and digital communication, the search for [...]
Unveiling Interlock RAT’s New PHP Variant: A Deep Dive into FileFix Delivery and KongTuke Connections In the evolving threat landscape, understanding the latest tactics, [...]
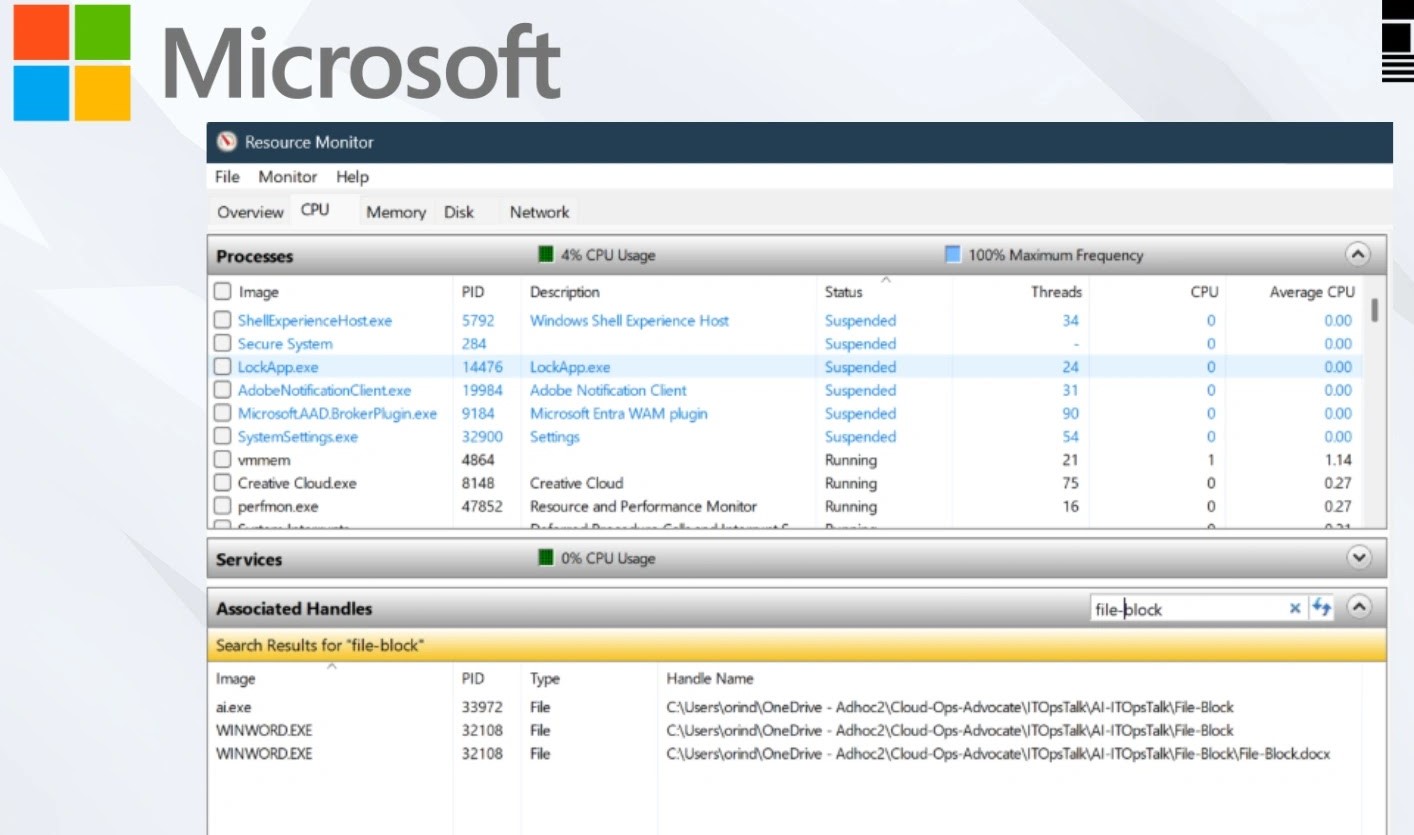
Unlocking Frustration: Resolving File Access Errors in Windows Few technical frustrations rival the sudden halt caused by a file access error in Windows. Whether [...]
The Silent Threat: Gigabyte UEFI Vulnerabilities Expose Systems to SMM Attacks In the complex architecture of modern computing, trust is paramount. Yet, critical vulnerabilities [...]
The Trojanized Game: How Threat Actors Are Targeting Gen Z Gamers The digital playground of Generation Z, often defined by their passion for online [...]
While phishing campaigns and ransomware attacks grab headlines, a more insidious threat often operates in the shadows of enterprise networks: exposed Git repositories. This [...]
Weekly Recap: Unpacking the Critical Cyber Incidents In cybersecurity, precision matters—and there’s little room for error. A small mistake, a missed setting, or a [...]