Unveiling the Myths and Truths about Cloud-Based CCTV Surveillance Cloud-based CCTV surveillance has gained popularity due to its flexibility, scalability, and accessibility. However, like any [...]
Attackers Can Bypass Windows Security Using New DLL Hijacking Technique Threat actors using the DLL Hijacking technique for persistence have been the order of the [...]
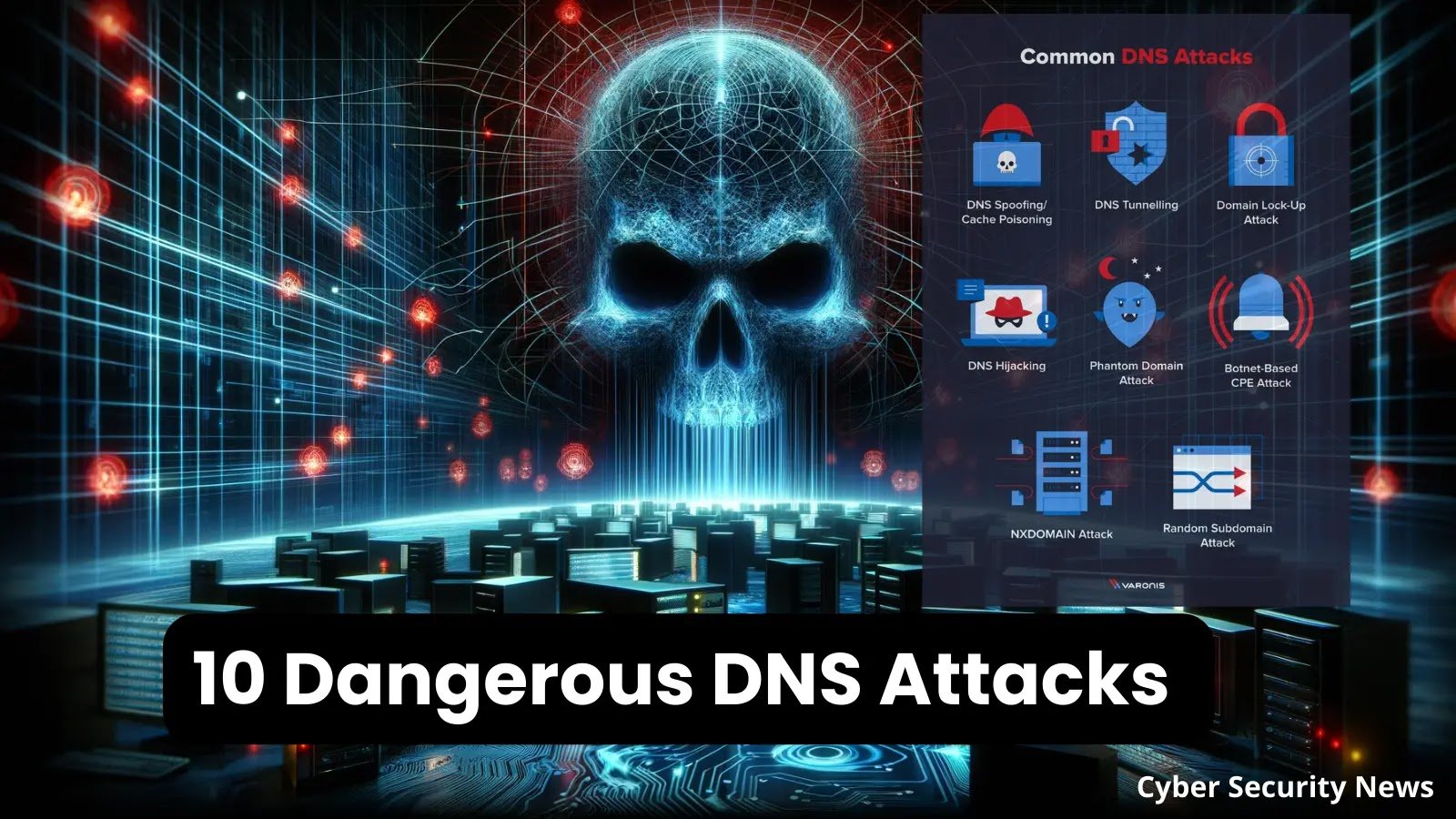
10 Dangerous DNS Attacks Types & Prevention Measures – 2024 Our topic for today seems to be centered around the most common 10 DNS attacks and how [...]
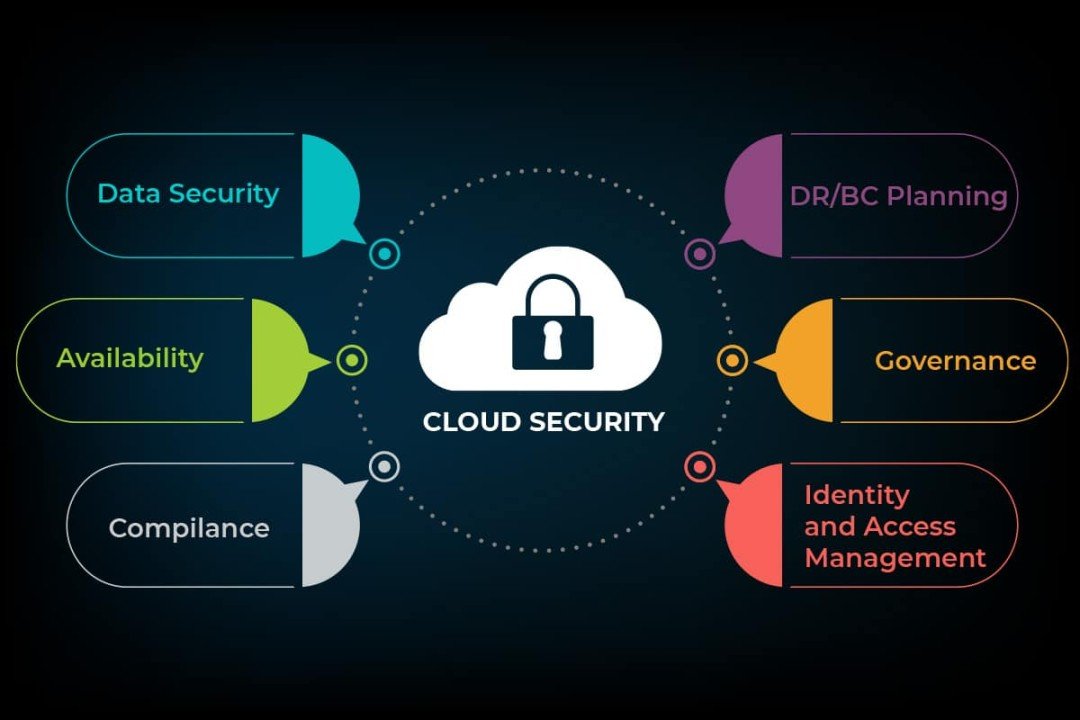
Unveiling the Secrets of Cloud Security Layers Cloud security is a critical aspect of modern computing, considering the widespread adoption of cloud services for data [...]
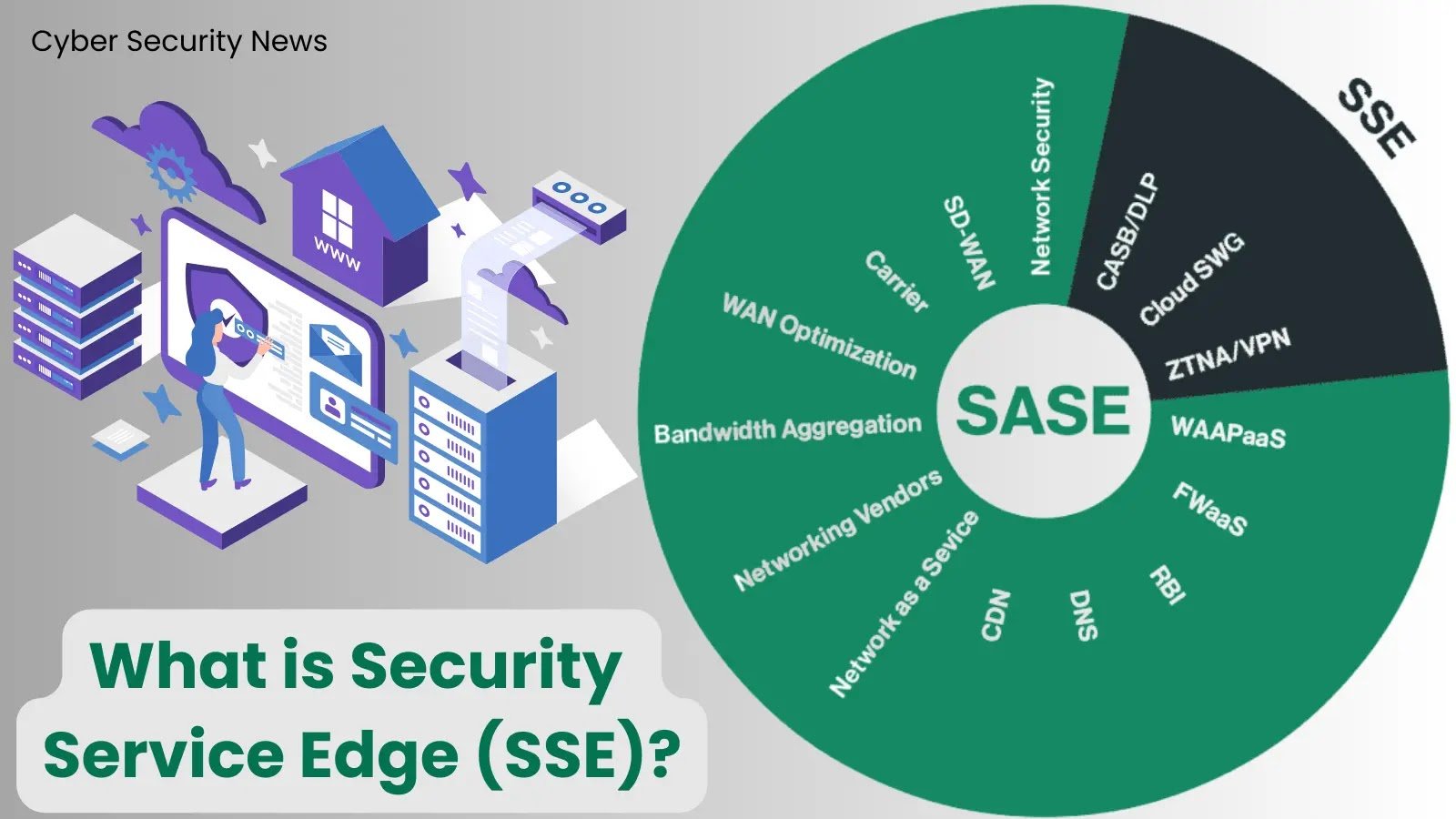
What is Security Service Edge (SSE)? – Revolutionizing Hybrid Work Security in Direct Cloud Access The contemporary work landscape is swiftly transitioning into a hybrid [...]
The Art of Cable Management: How to Organize Your Cabling Chaos Cable management is a crucial aspect of maintaining a clean and organized workspace. [...]
The Future of Wireless Security: Quantum Cryptography Quantum cryptography is a cutting-edge field that holds promise for revolutionizing wireless security. Unlike traditional cryptographic methods, which [...]
Top 3 Cybersecurity Trends for SME Business Leaders in 2024 As Cynet’s COO, my team and I get to work closely with risk management executives [...]
Hackers using Weaponized Office Document to Exploit Windows Search RCE A new attack chain campaign has been discovered, which involves the exploitation of CVE-2023-36884 and [...]
5 Benefits of XDR for Cybersecurity Cybersecurity requires staying one step ahead. A main force of digital protection is eXtended Detection and Response (XDR). This [...]