What is Hacking? Hacking refers to unauthorized intrusion in a system or a network. The person involved in this process is called a hacker. They [...]
What do you mean by fingerprinting in ethical hacking? In ethical hacking, fingerprinting refers to the process of gathering information about a target system or [...]
Establishing secure algorithms in a network is crucial to safeguard sensitive data and communications from unauthorized access, tampering, and interception. Here are various methods for [...]
What type of technology trends are most people buying Today onwards? It all depends on the domain. For example, the eCommerce industry is boosting due [...]
What is Malicious Activity on Google play apps? Malicious activity on Google Play apps refers to any unauthorized, harmful, or deceptive behavior exhibited by certain [...]
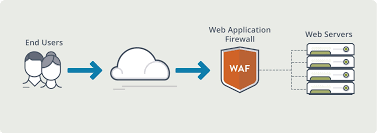
1. What is meany by WAF? A firewall that monitors, filters, and stops HTTP traffic going to and from a website or web application is [...]
What are Firmware updates : Firmware updates are software updates specifically designed to improve or modify the functionality of electronic devices, such as smartphones, computers, [...]
A router is a networking device that connects different networks together and directs data packets between them. It acts as a central hub for internet [...]
Common Network Protocols And Their Vulnerabilities Network protocols are essential for communication between devices and systems on a network. However, some protocols have vulnerabilities that [...]
What is VPN? VPN stands for Virtual Private Network. It is a technology that allows users to create a secure and encrypted connection over a [...]