In a stark reminder of the persistent threats facing enterprise networks, threat actors are actively exploiting a critical vulnerability in Apache ActiveMQ servers. This [...]
Microsoft has rolled out an optional non-security update, KB5077241, for its latest Windows 11 iterations, versions 25H2 and 24H2. While this particular release doesn’t [...]
The AI-Powered Blitz: How Threat Actors Are Hacking Domains in Under 30 Minutes The cybersecurity landscape has undergone a dramatic shift, with threat actors [...]
The U.S. Department of the Treasury’s Office of Foreign Assets Control (OFAC) recently unveiled a significant action against a nexus of cyber exploit brokers, [...]
Unmasking RoguePilot: When GitHub Copilot Turns Against You The lines between developer assistance and potential exploit are blurring. Recent findings by the Orca Research [...]
Malicious NuGet Packages: A Silent Threat to ASP.NET Application Security The digital landscape demands vigilance, and recent events highlight a concerning trend: supply chain attacks [...]
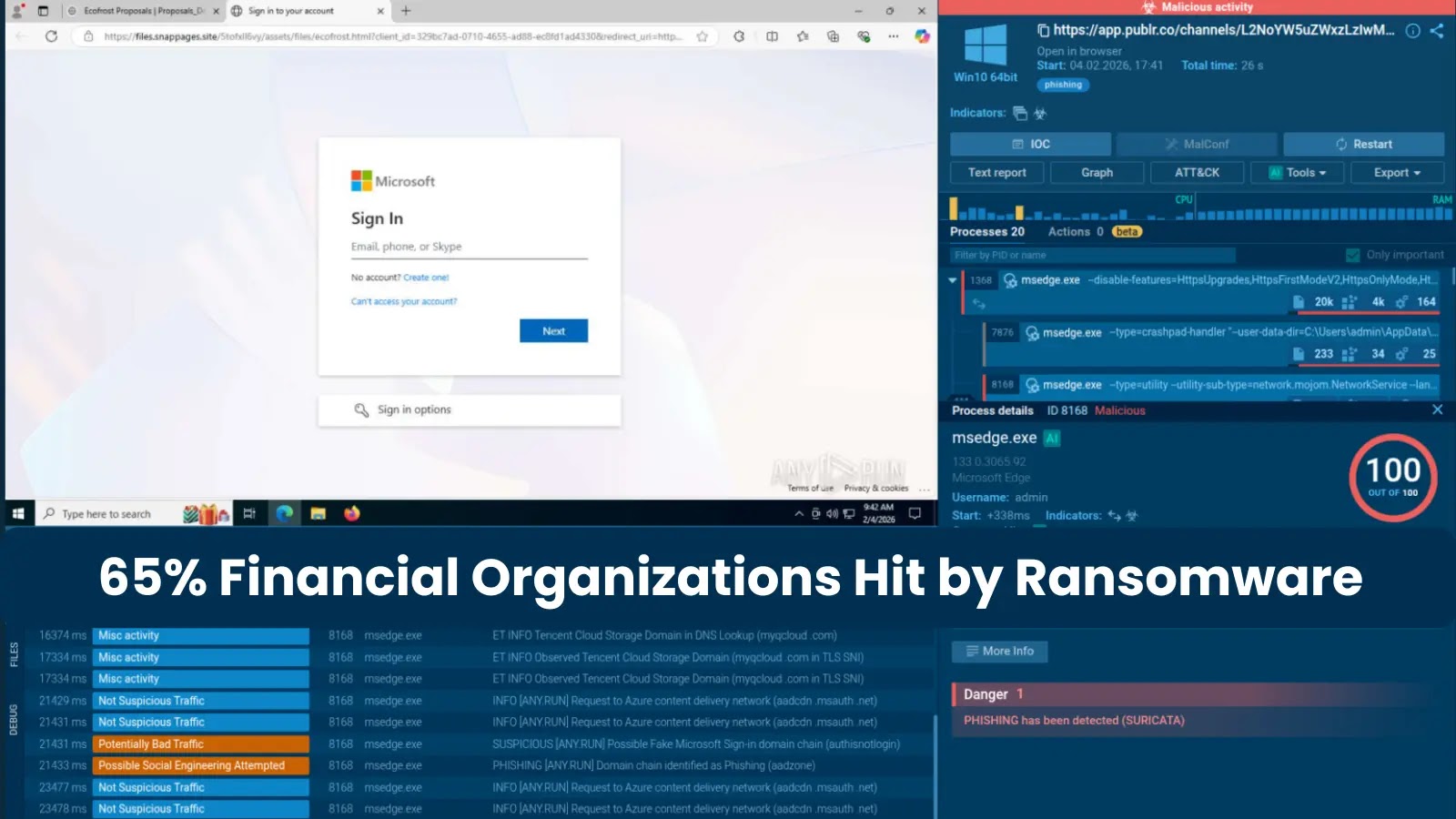
The Ransomware Reckoning: Why Financial Institutions Are Cybercriminals’ Gold Mine The financial sector isn’t just about money; it’s the bedrock of our economic stability, entrusted [...]
In a concerning evolution of cyber threats, the notorious Atomic macOS Stealer (AMOS) has adopted a new, insidious tactic to compromise users. Previously relying on [...]
The digital landscape is a constant battleground, and even the most robust systems can harbor hidden weaknesses. A recent discovery has sent ripples through the [...]
The digital playgrounds of children are increasingly becoming a battleground for privacy. A recent and significant development highlights this concern: Reddit, one of the internet’s [...]