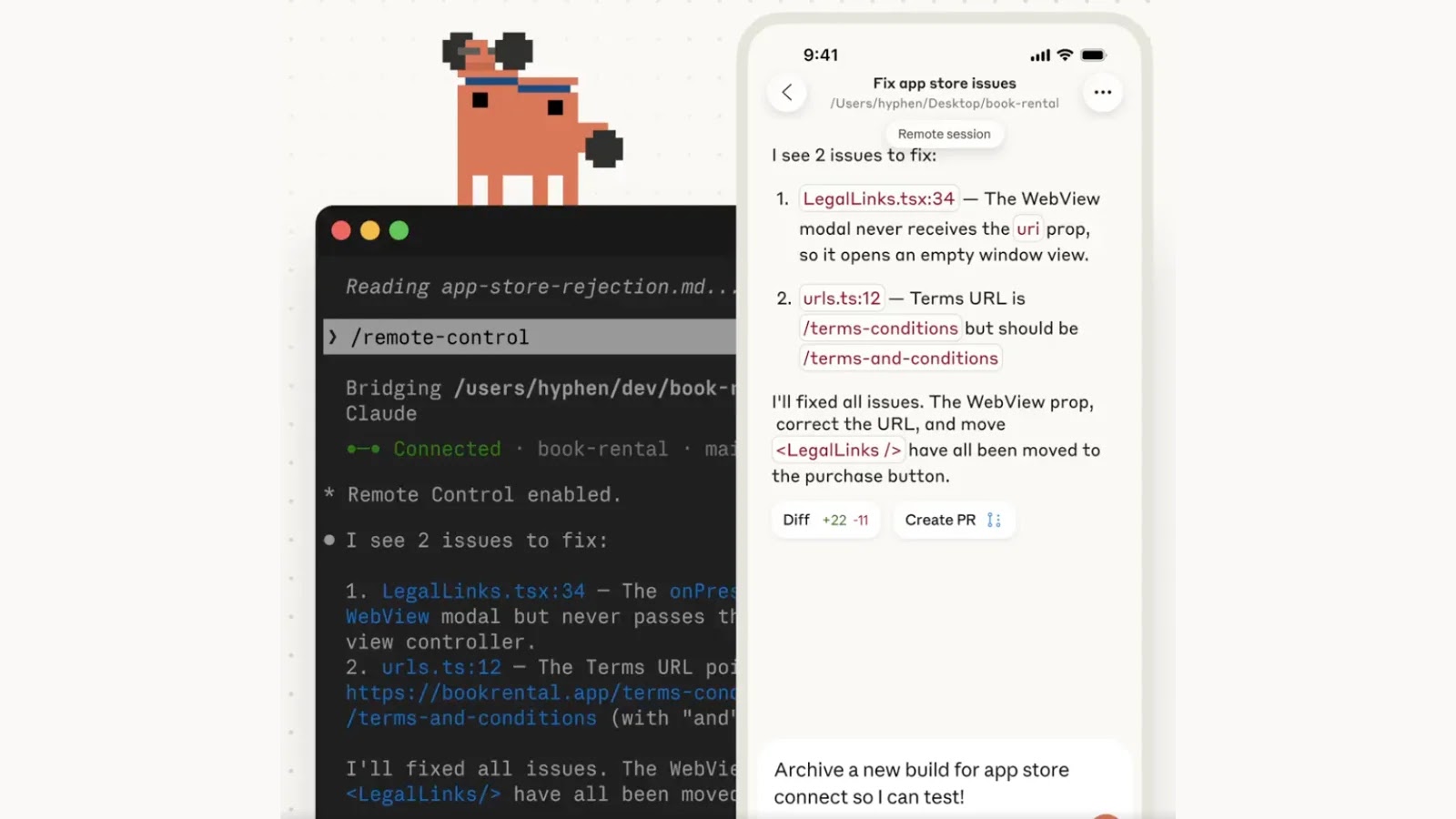
In a significant move poised to reshape how developers interact with their terminal environments, Anthropic has unveiled a new “Remote Control” feature for its agentic [...]
Organizations worldwide rely on enterprise AI platforms to streamline operations, enhance decision-making, and drive innovation. Among these, ServiceNow stands out as a critical component for [...]
Enterprise security teams face an escalating threat landscape, where the sophistication of attack vectors continues to grow. A recent and particularly disturbing development is the [...]
Weaponized AI: OpenAI Confirms ChatGPT Used by Chinese State-Linked Hackers The digital battleground just got a lot more complex. In a sobering revelation, OpenAI has [...]
The web is a dynamic landscape, constantly evolving to deliver richer user experiences. This evolution, however, often introduces new security challenges. Among the most pervasive [...]
Leadership changes at key cybersecurity firms often signal strategic shifts and amplify a company’s capacity to address evolving threats. When a trusted leader in identity [...]
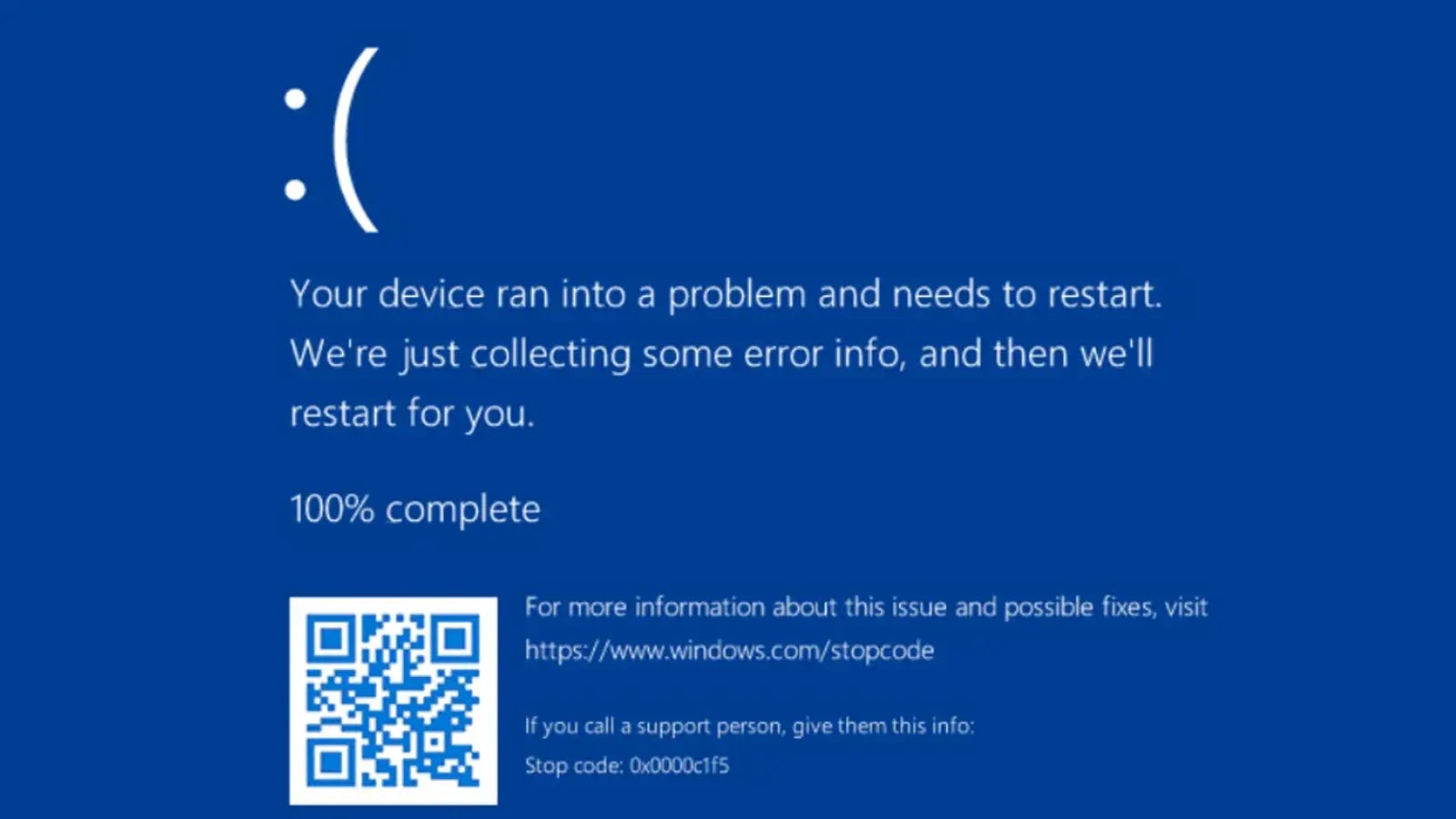
Critical Windows Vulnerability Uncovered: PoC Released for Unrecoverable BSODs A significant cybersecurity threat has emerged for Windows users, with a publicly released proof-of-concept (PoC) [...]
The landscape of software development is undergoing a profound transformation, with artificial intelligence increasingly woven into every stage of the software supply chain. While AI [...]
In a stark reminder that even the oldest digital skeletons can rattle the foundations of modern security, a newly confirmed vulnerability in the Telnet daemon [...]
Unmasking Decade-Long Espionage: Google Dismantles Chinese Hacking Infrastructure The digital shadows have once again been illuminated, revealing a highly sophisticated and disturbingly pervasive cyber [...]