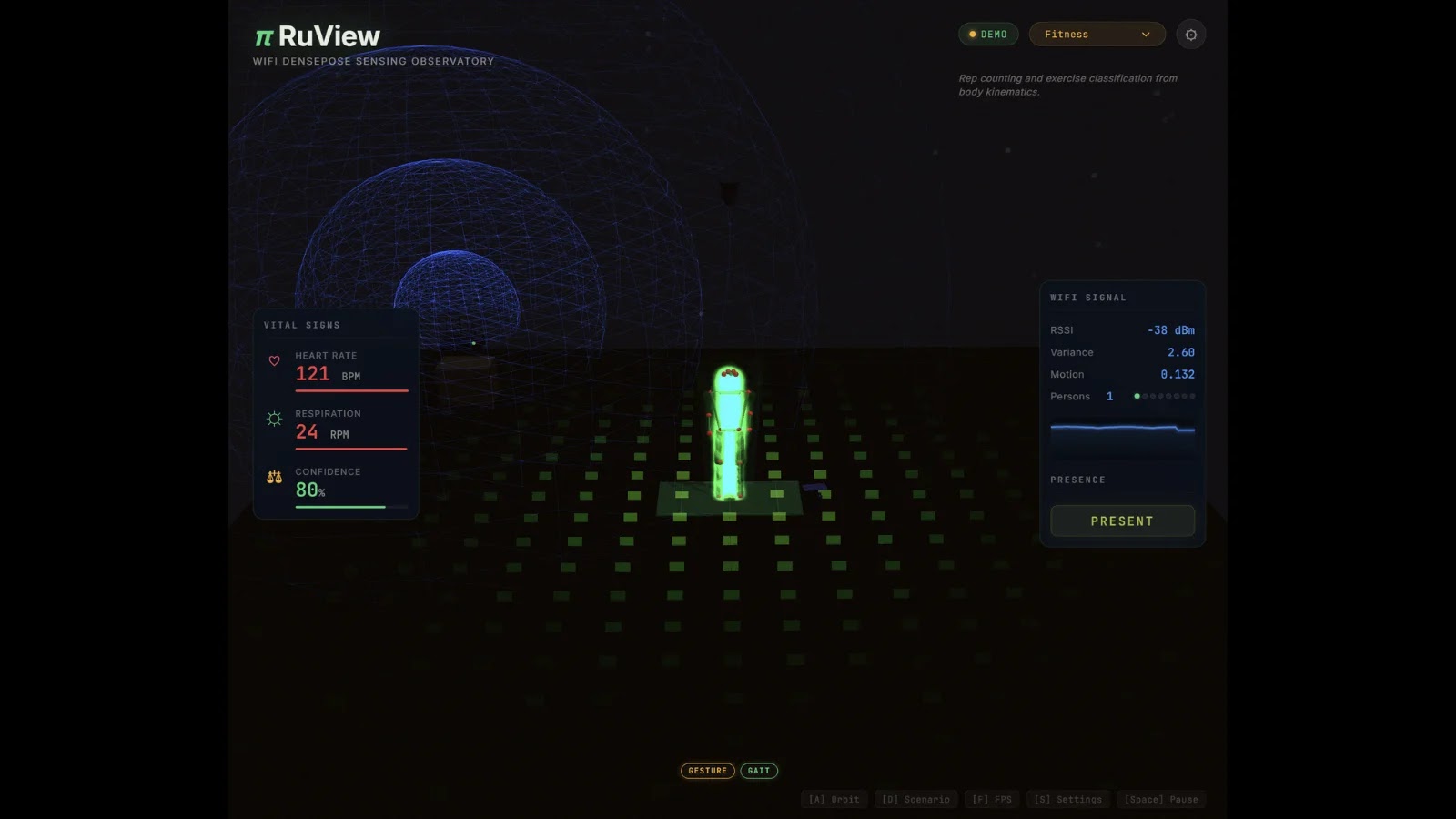
Unseen Eyes: WiFi Signals, Human Activities, and the π RuView Surveillance Threat The invisible waves that power our daily connectivity are now revealing our [...]
The Dawn of Autonomous Application Security: OpenAI’s Codex Security Unleashed In the relentless battle against software vulnerabilities, security teams often find themselves overwhelmed by a [...]
A disturbing evolution in social engineering attacks has surfaced, directly targeting the powerful capabilities of Windows Terminal. Cybersecurity researchers have uncovered a new wave of [...]
Remote Monitoring and Management (RMM) tools are the unsung heroes of modern IT operations. For countless security professionals and system administrators, these platforms are indispensable, [...]
A cybersecurity incident rocking the Federal Bureau of Investigation (FBI) has sent ripples through national security circles. A sensitive internal network, crucial for managing wiretapping [...]
For too long, Linux systems have enjoyed a reputation as the more secure alternative, often overlooked by threat actors concentrating on Windows environments. This perception, [...]
The pace of innovation in artificial intelligence is staggering. What began as advanced coding assistance has rapidly transformed into autonomous vulnerability research. This evolution was [...]
In an increasingly interconnected digital landscape, reliance on cloud services is paramount for businesses and individuals alike. When these critical services falter, the impact can [...]
The landscape of software development relies heavily on open-source contributions. While fostering innovation, this reliance also introduces a critical challenge: the proliferation of vulnerabilities within [...]
China-Nexus Hackers Deploy New Malware Against South American Telecoms In a concerning escalation of state-sponsored cyber offensives, a sophisticated China-linked advanced persistent threat (APT) actor, [...]