The lines between privacy and national security are constantly redrawn, especially when cutting-edge technology intersects with legal investigations. A recent development stemming from a massive [...]
Windows 11 KB5074109 Update: A Stability Nightmare Prompts Microsoft’s Urgent Recall In the intricate ecosystem of operating systems, routine security updates are a cornerstone of [...]
The digital shadows hide many types of actors, but few are as insidious and foundational to the cybercrime ecosystem as initial access brokers (IABs). These [...]
In the high-stakes world of cybersecurity, a disclosed vulnerability often grants attackers a roadmap to exploit systems. However, a more immediate and insidious threat emerges [...]
Pwn2Own Automotive 2026: A Wake-Up Call for Vehicle Security The automotive industry is rapidly evolving, integrating more software and connectivity than ever before. While this [...]
Facebook remains a primary target for threat actors due to its vast user base and the wealth of personal data it contains. A new and [...]
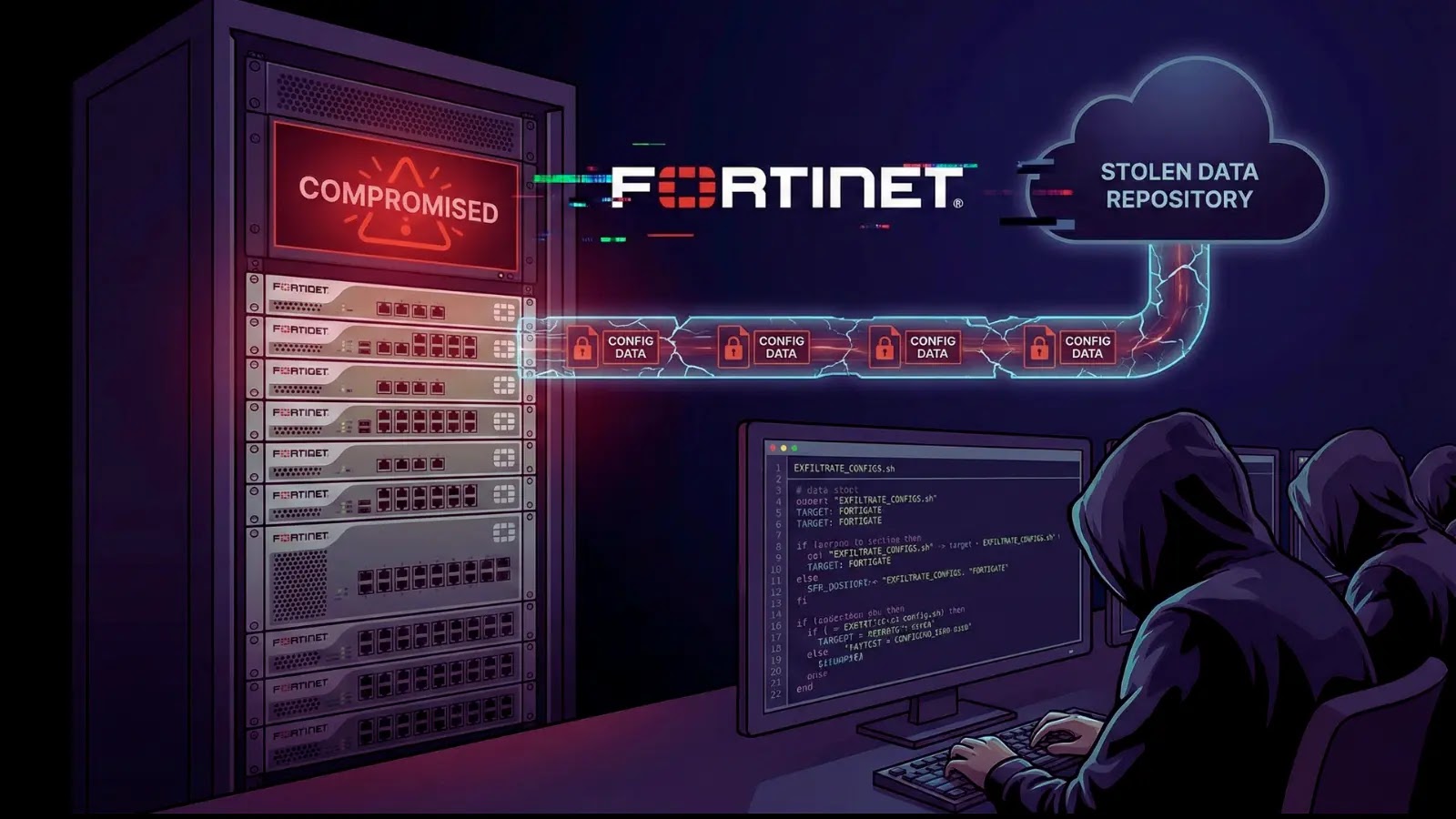
FortiGate Firewalls Under Attack: Automated Campaign Exploits Devices to Steal Configuration Data Recent intelligence points to a renewed and concerning surge in automated malicious activity [...]
Critical Vivotek Vulnerability Opens Door to Remote Code Execution for Legacy Devices In an alarming development for organizations relying on older surveillance infrastructure, a critical [...]
A disturbing trend is emerging from the complex landscape of web applications: a significant number of third-party tools are accessing sensitive user data without proper [...]
The digital landscape is a constant battleground, and even the most robust systems can harbor hidden vulnerabilities. In a recent and critical development, the U.S. [...]