In the relentlessly evolving landscape of cyber warfare, threat actors continually refine their tactics, blurring the lines between humanitarian aid and malicious intent. A [...]
Discord Users Under Attack: VVS Stealer Targets Credentials and Tokens The digital landscape often mirrors a constant battleground, and for millions of Discord users, [...]
The Unseen Threat: Why Third-Party Vulnerabilities Are Forcing a Security Modernization Sprint The digital landscape is a complex tapestry woven from interconnected systems, applications, and [...]
Unpacking the Critical FortiSIEM Vulnerability: A Deep Dive into CVE-2025-64155 The cybersecurity landscape is constantly shifting, with new threats emerging that demand immediate attention [...]
Ransomware has long been a formidable threat, but a new, insidious twist is emerging that amplifies its danger: the integration of Large Language Models [...]
Unmasking the “Contagious Interview”: North Korea’s Latest Code-Abuse Cyber Espionage The digital battlefield is constantly shifting, and North Korean threat actors are once again [...]
The digital landscape is a constant battleground, where the convenience of cutting-edge technology often walks hand-in-hand with unforeseen security risks. Microsoft Copilot, an AI assistant [...]
Unmasking DragonForce: A Deep Dive into the Latest Ransomware Threat and Its Decryptor The digital landscape is a constant battlefield, and emerging ransomware operations [...]
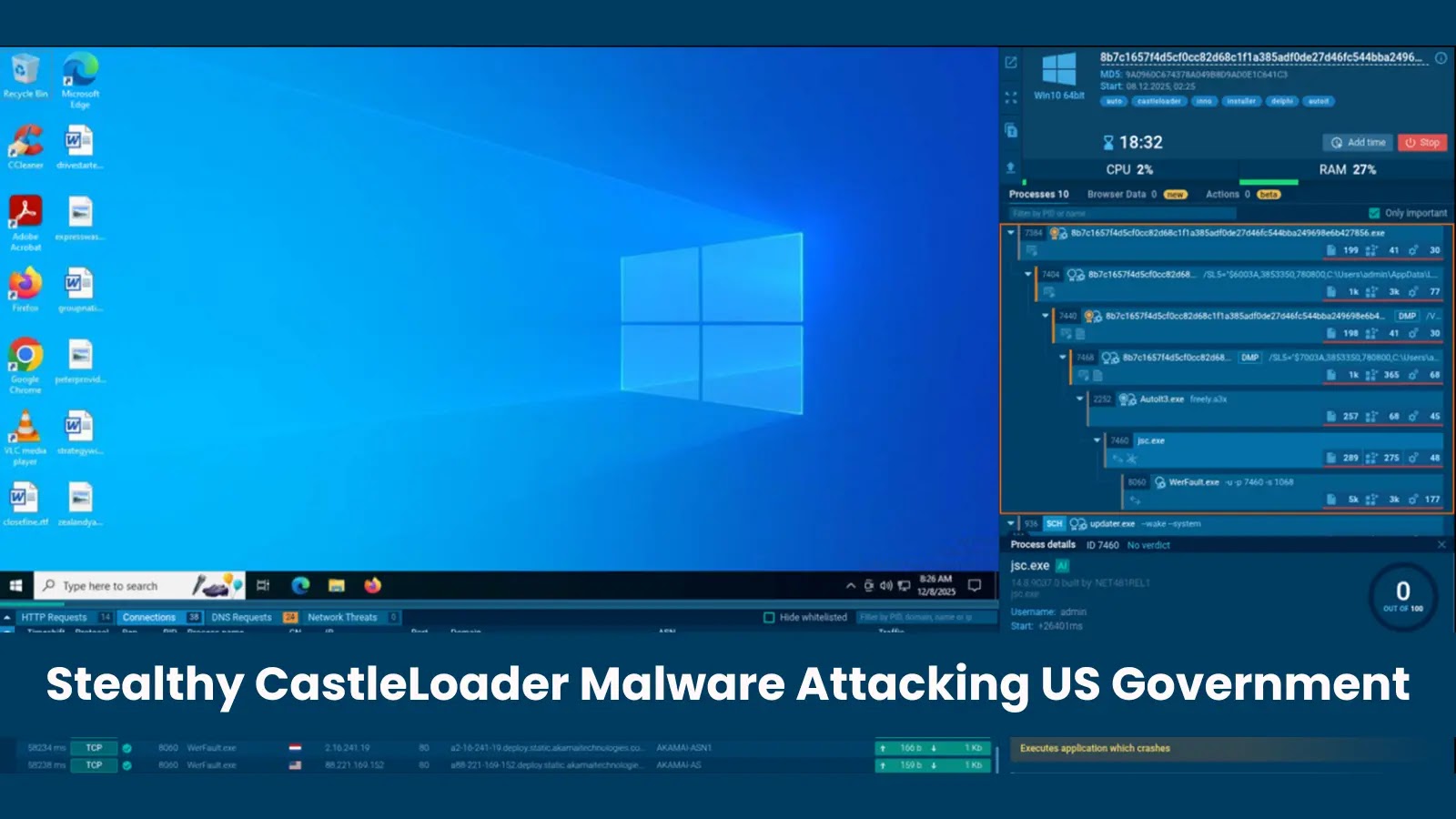
Stealthy CastleLoader Malware: An Evolving Threat to US Government and Critical Infrastructure The cybersecurity landscape has recently witnessed the emergence of a highly sophisticated [...]
A significant security flaw has recently come to light in Microsoft SQL Server, posing a substantial risk to organizations leveraging this widely used database [...]