New Threat Detection Model Detects Threats in Serverless Cloud With 0.003 False Rate Researchers have introduced a novel threat detection model designed specifically for serverless [...]
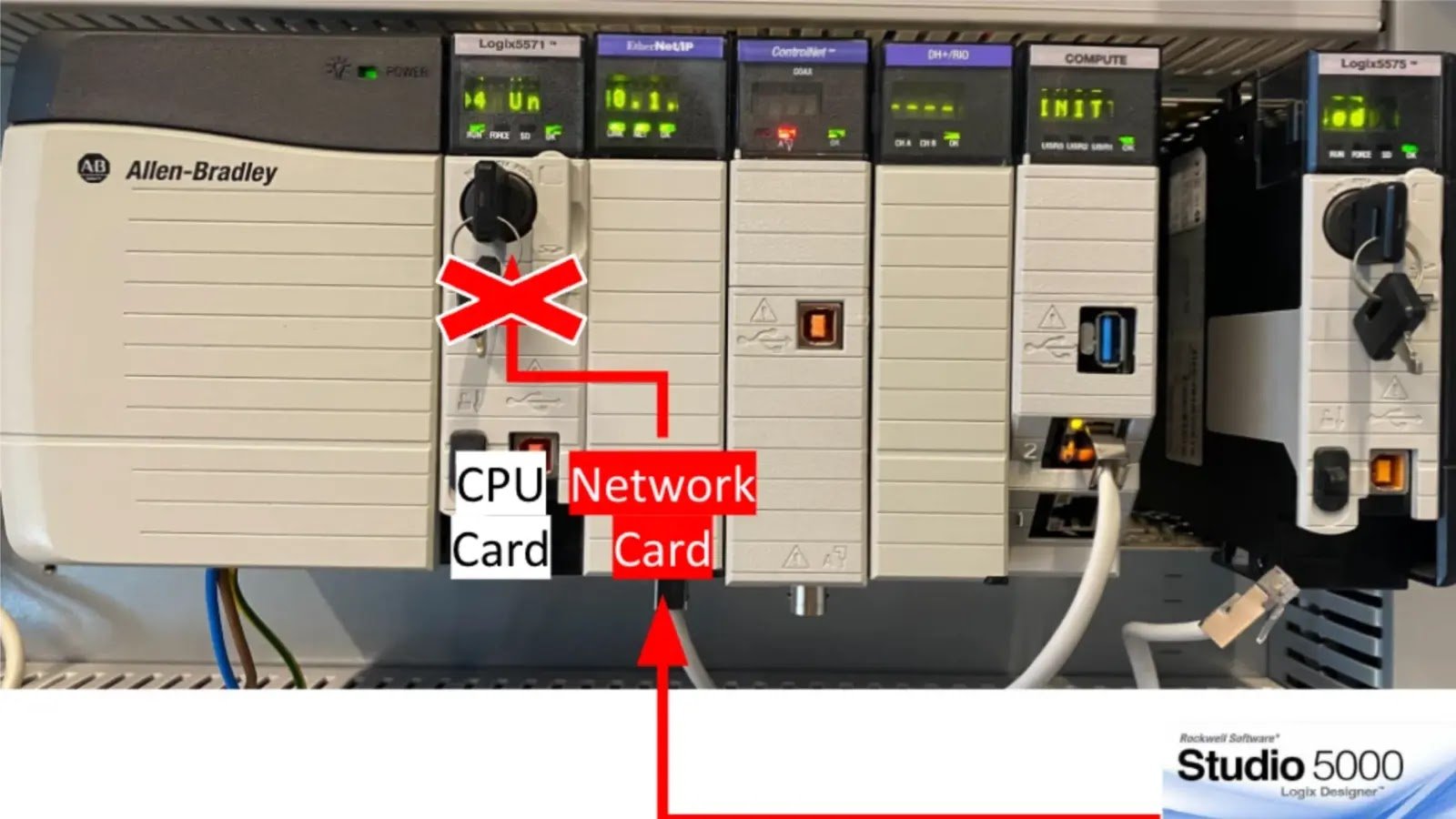
Rockwell Automation Devices Flaw Let Hackers Gain Unauthorized Access A critical security vulnerability in Rockwell Automation’s ControlLogix and GuardLogix controllers has been discovered. This vulnerability [...]
Hackers Abuse Cloudflare WARP To Hijack Cloud Services Recently, several campaigns have been observed using Cloudflare’s WARP service to target susceptible internet-facing services. The primary [...]
10 Best Linux Firewalls At present, many computers are connected via numerous networks. Monitoring all traffic and having something to filter out good and harmful [...]
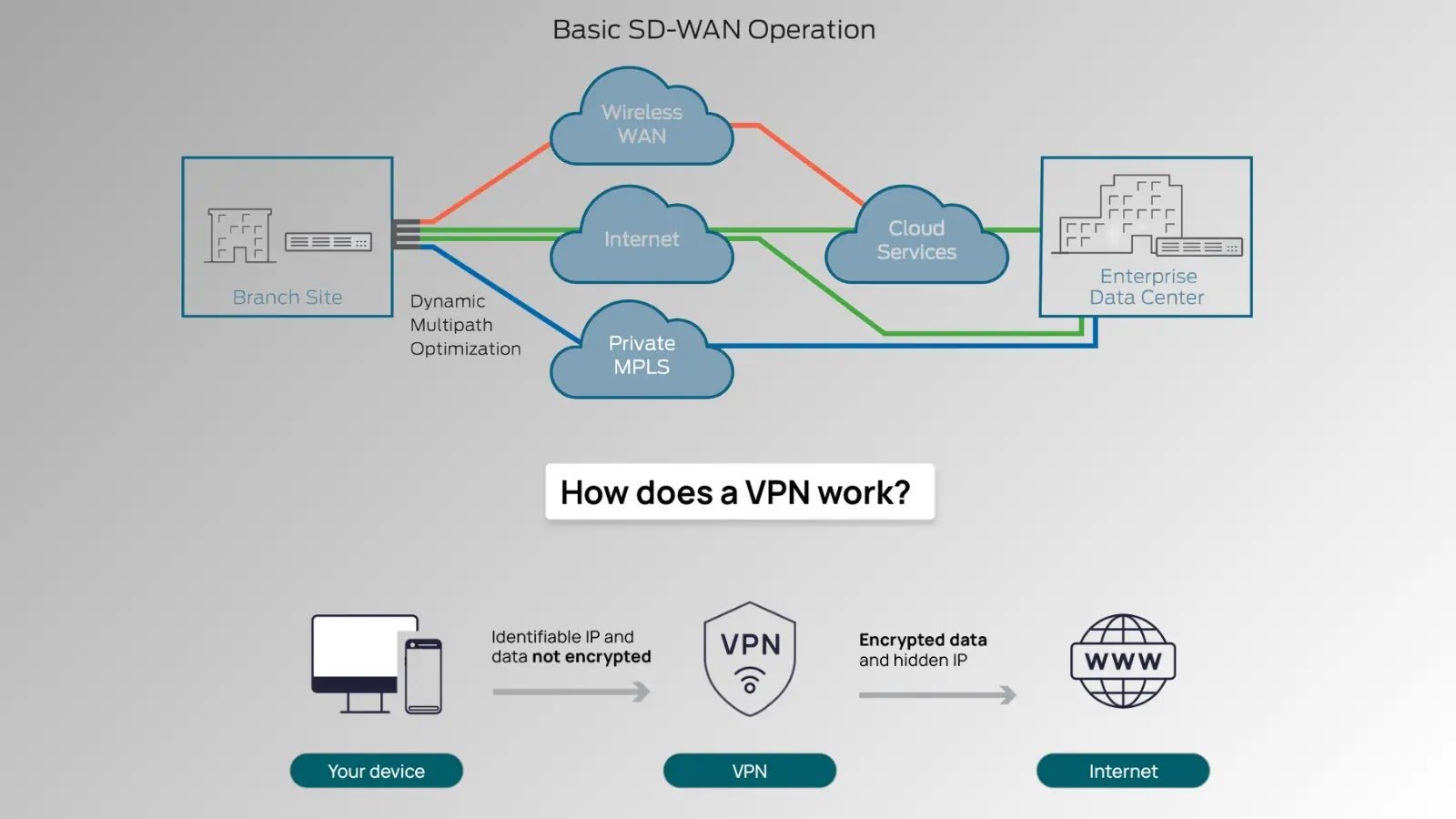
VPNs vs. SD-WAN: Which Provides Better Cybersecurity? In today’s hyper-connected world, cybersecurity is a critical concern for businesses and individuals alike. Two technologies often come up in [...]
New OpenSSH Vulnerability CVE-2024-6409 Exposes Systems to RCE Attack Security researchers have discovered a new vulnerability in OpenSSH, identified as CVE-2024-6409, which could potentially allow remote code execution attacks on [...]
10 Best Open-Source Firewall to Protect Your Enterprise Network Open-source firewalls are best known for protecting the network from threats by filtering inbound and outbound traffic [...]
Multiple Flaws In Rockwell Automation Panel Let Attackers Execute Remote Code Two vulnerabilities in Rockwell Automation PanelView Plus have been discovered. Unauthenticated attackers could exploit them remotely [...]
How Restricting Access to Resources Improves Cyber Security Something needs to change with cyber security. One study found that between 2021 and 2022, data breaches [...]
Best Intrusion Detection & Prevention Systems (IDS &IPS) An Intrusion Detection and Prevention System (IDPS) is a security solution designed to detect and prevent unauthorized [...]