What is the Difference Between ISO 27001 & 27002 Compliance? – A Detailed Guide ISO 27001 and ISO 27002 are international standards that provide a [...]
How Do ISO 27001 and ISO 27002 Help to Manage the IT Security? ISO 27001 and ISO 27002 are integral in managing an organization’s IT [...]
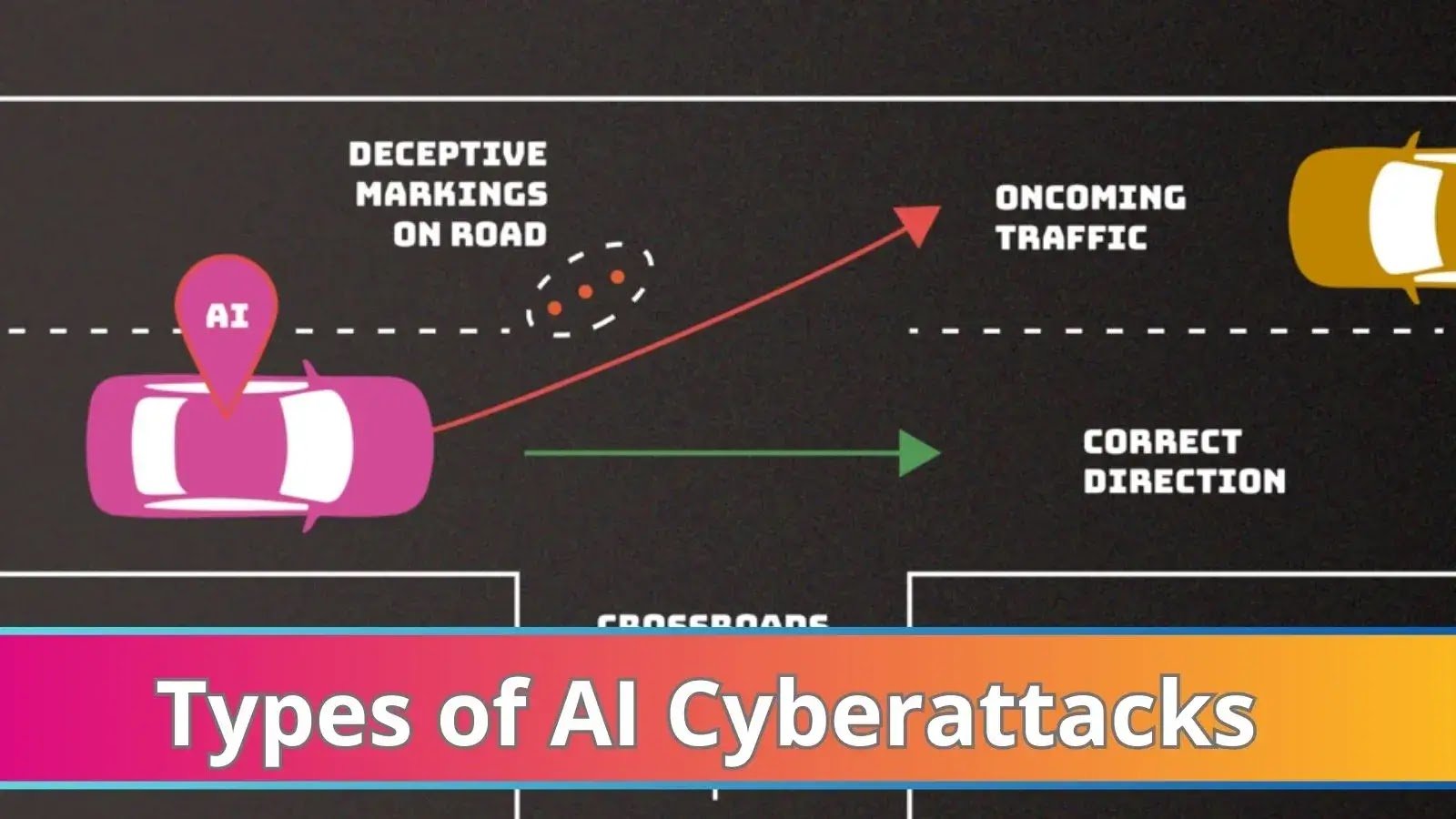
NIST Details Types of Cyberattacks that Leads to Malfunction of AI Systems Artificial intelligence (AI) systems can be purposefully tricked or even “poisoned” by attackers, [...]
Hackers Employ New Evasion Mechanisms to Bypass Security Solutions The digital landscape, once a serene meadow, has morphed into a battleground where attackers and security [...]
Sea Turtle APT Group Exploiting Known Vulnerabilities to Attack IT-service Providers To obtain access to a variety of clients’ systems and data in a single [...]
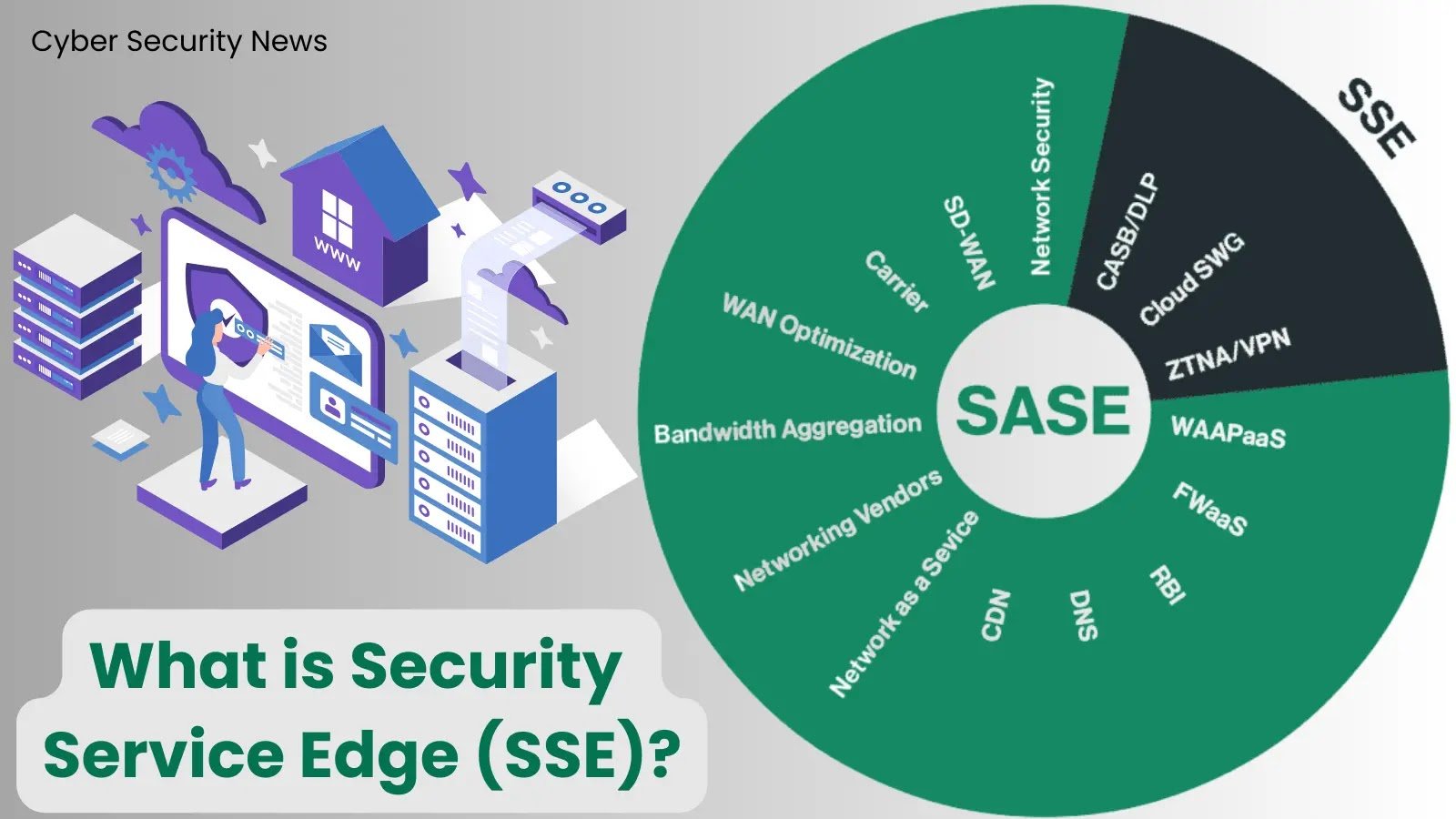
SonicWall Acquires Banyan Security for Security Service Edge (SSE) Solutions SonicWall has made a strategic move in the evolving cybersecurity landscape, acquiring Banyan Security, a [...]
Attackers Can Bypass Windows Security Using New DLL Hijacking Technique Threat actors using the DLL Hijacking technique for persistence have been the order of the [...]
What is Security Service Edge (SSE)? – Revolutionizing Hybrid Work Security in Direct Cloud Access The contemporary work landscape is swiftly transitioning into a hybrid [...]
Top 3 Cybersecurity Trends for SME Business Leaders in 2024 As Cynet’s COO, my team and I get to work closely with risk management executives [...]
Hackers using Weaponized Office Document to Exploit Windows Search RCE A new attack chain campaign has been discovered, which involves the exploitation of CVE-2023-36884 and [...]