5 Benefits of XDR for Cybersecurity Cybersecurity requires staying one step ahead. A main force of digital protection is eXtended Detection and Response (XDR). This [...]
Securing Your Digital World: The Latest in Cybersecurity Innovations The importance of robust cybersecurity measures cannot be overstated in the digital age. As technology advances, [...]
Reflectiz Introduces AI-powered Insights on Top of Its Smart Alerting System Reflectiz, a cybersecurity company specializing in continuous web threat management, proudly introduces a new [...]
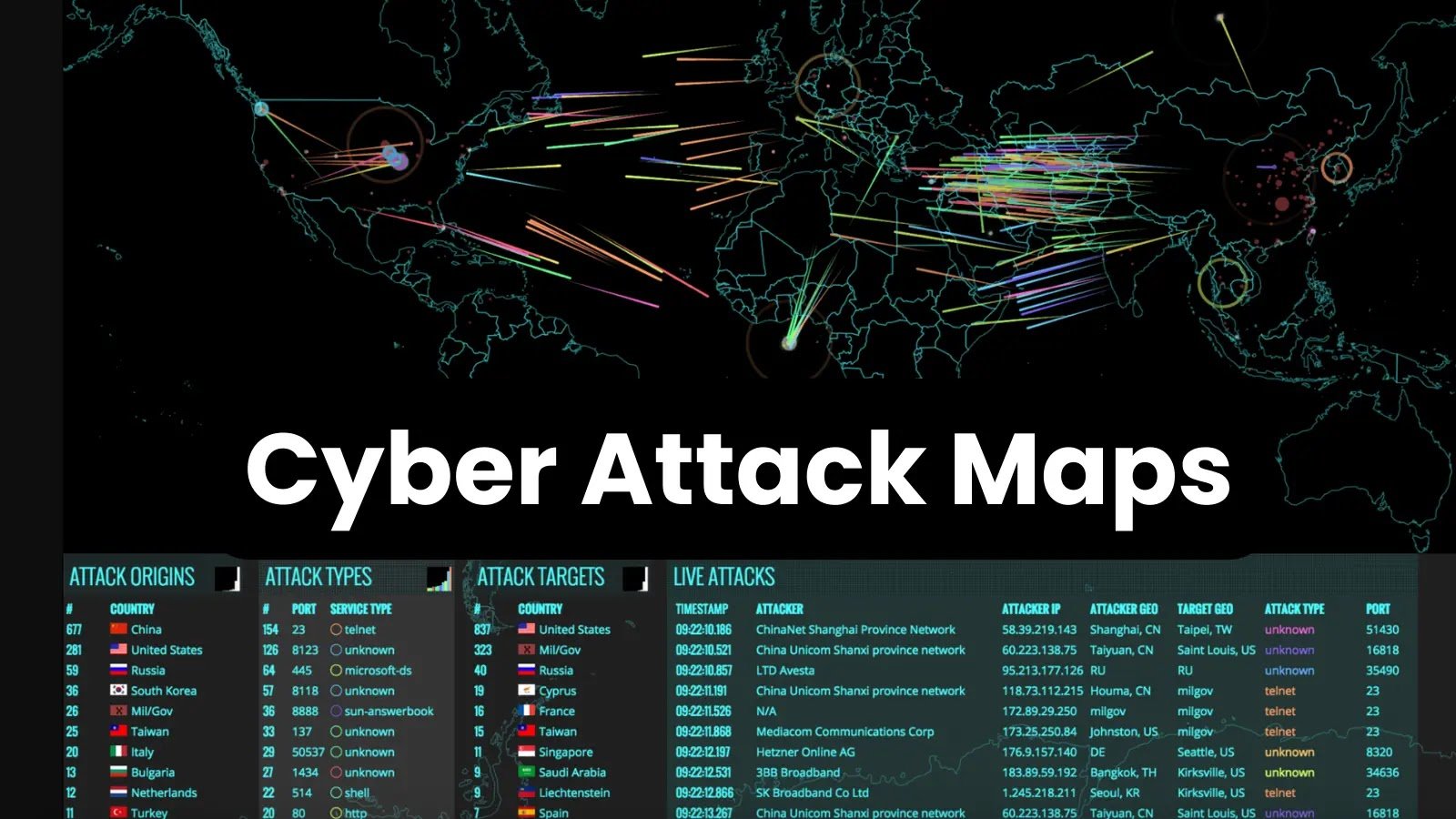
Top 10 Cyber Attack Maps to See Digital Threats In 2024 Cyber attack maps are visual representations or interactive tools that provide real-time or historical [...]
What is SSL and Why it is Important? The protocols SSL (Secure Sockets Layer) and TLS (Transport Layer Security), are used to create secure connections [...]
Loader Malware Steal Sensitive System Data & Installs Other Malware In the intricate dance of cybersecurity threats, loader malware emerges as a silent force, discreetly [...]
To effectively navigate the complex landscape of Active Directory disaster recovery planning, organizations must establish comprehensive strategies that encompass backup and restoration procedures, proactive monitoring [...]
What is Dynamic Application Security Testing (DAST) ? Businesses and developers are focusing more on the security of applications in their digital environment as cyber [...]
We’re currently living in an age where digital threats loom large. Among these, ransomware has emerged as a formidable adversary, disrupting businesses and individuals alike. [...]
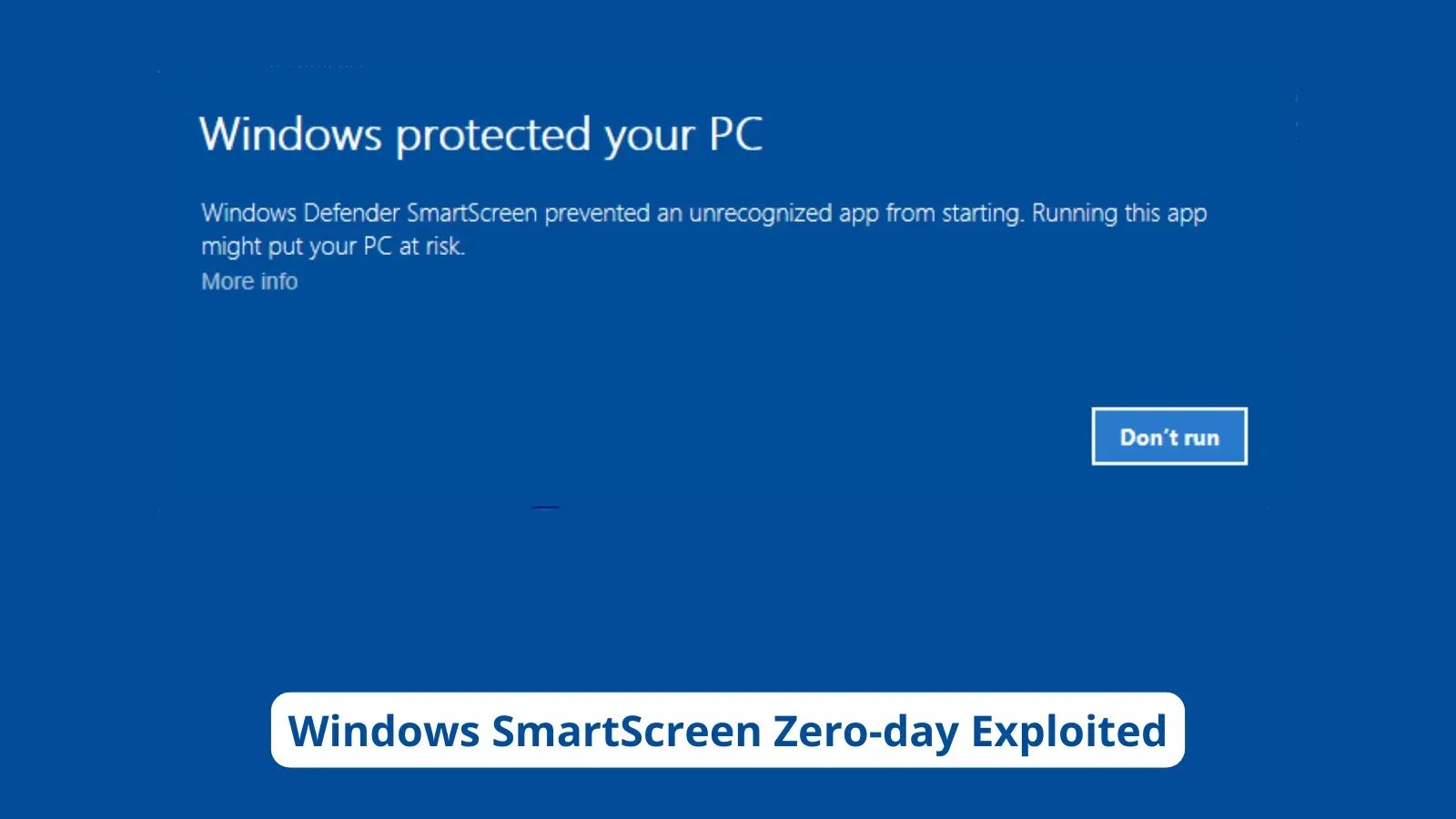
Hackers Exploiting Windows SmartScreen Zero-day Flaw to Deploy Remcos RAT Microsoft released multiple security patches as part of their Patch Tuesday, in which three zero-day vulnerabilities [...]