Detailed Comparison of Fortinet Products device: FortiAnalyzer 150G and 200F Upgrade Network Security Document In the ever-evolving landscape of network security, Fortinet stands as a [...]
Network Segmentation in Cybersecurity: What You Need to Know In today’s interconnected world, where data breaches and cyber threats are ever-evolving, implementing effective network segmentation [...]
AI and Machine Learning in Cybersecurity: The Role of AI In today’s interconnected digital landscape, cybersecurity stands as a critical pillar in safeguarding our technological [...]
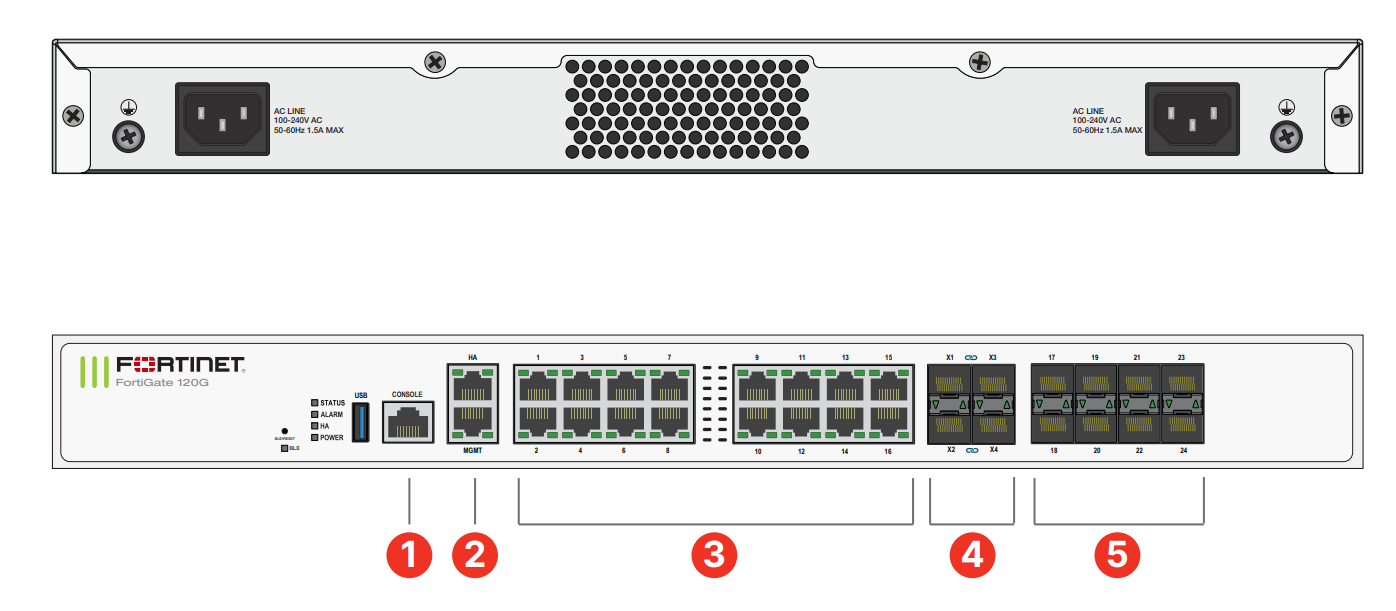
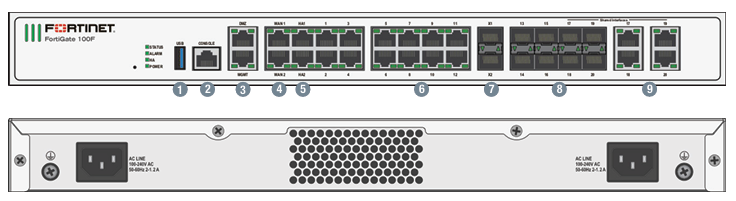
This article provides a comprehensive comparison between Fortinet FortiGate firewall models, specifically focusing on the FortiGate 100F and the 120G. We will delve into their [...]
Troubleshooting IPsec VPN Site-To-Site Connections in FortiGate Firewall Ensuring the robust operation of secure network connections is paramount for any enterprise. This article delves into [...]
The Fortigate 100F Firewall stands as a robust solution in the realm of network and security, designed to protect organizations from an ever-evolving landscape of [...]
Cisco AnyConnect VPN Server Vulnerability Let Attackers Trigger DoS Attack A critical security vulnerability affecting Cisco Meraki MX and Z Series devices could allow unauthenticated [...]
Hackers Actively Exploiting Zyxel RCE Vulnerability Via UDP Port A significant spike was observed in exploitation attempts targeting CVE-2023-28771, a critical remote code execution vulnerability affecting [...]
Palo Alto Networks PAN-OS Vulnerability Enables Admin to Execute Root User Actions A critical command injection vulnerability in Palo Alto Networks PAN-OS operating system enables [...]
Cisco ISE Vulnerability Allows Remote to Access Sensitive Data – PoC Exploit Available A critical vulnerability affecting its Identity Services Engine (ISE) when deployed on major cloud [...]