TSforge – A New Tool Exploits Every Version of Windows Activation Security researchers from MASSGRAVE have unveiled TSforge, a groundbreaking tool exploiting vulnerabilities in Microsoft’s [...]
New Threat Hunting Technique to Uncover Malicious Infrastructure Using SSL History As internet security evolves, SSL (Secure Sockets Layer) certificates, cornerstones of encrypted communication, are [...]
What is Cryptographic Failures? Cryptographic failures occur when the mechanisms and protocols designed to secure data and communications through encryption break down, become compromised, or [...]
Fortinet Acquired Perception Point to Boost Email Security Fortinet, a global leader in cybersecurity solutions, today announced the completion of its acquisition of Perception Point, [...]
What is Host-based Intrusion Detection System? Organizations face a myriad of challenges in protecting their digital assets. One critical component of a robust security strategy [...]
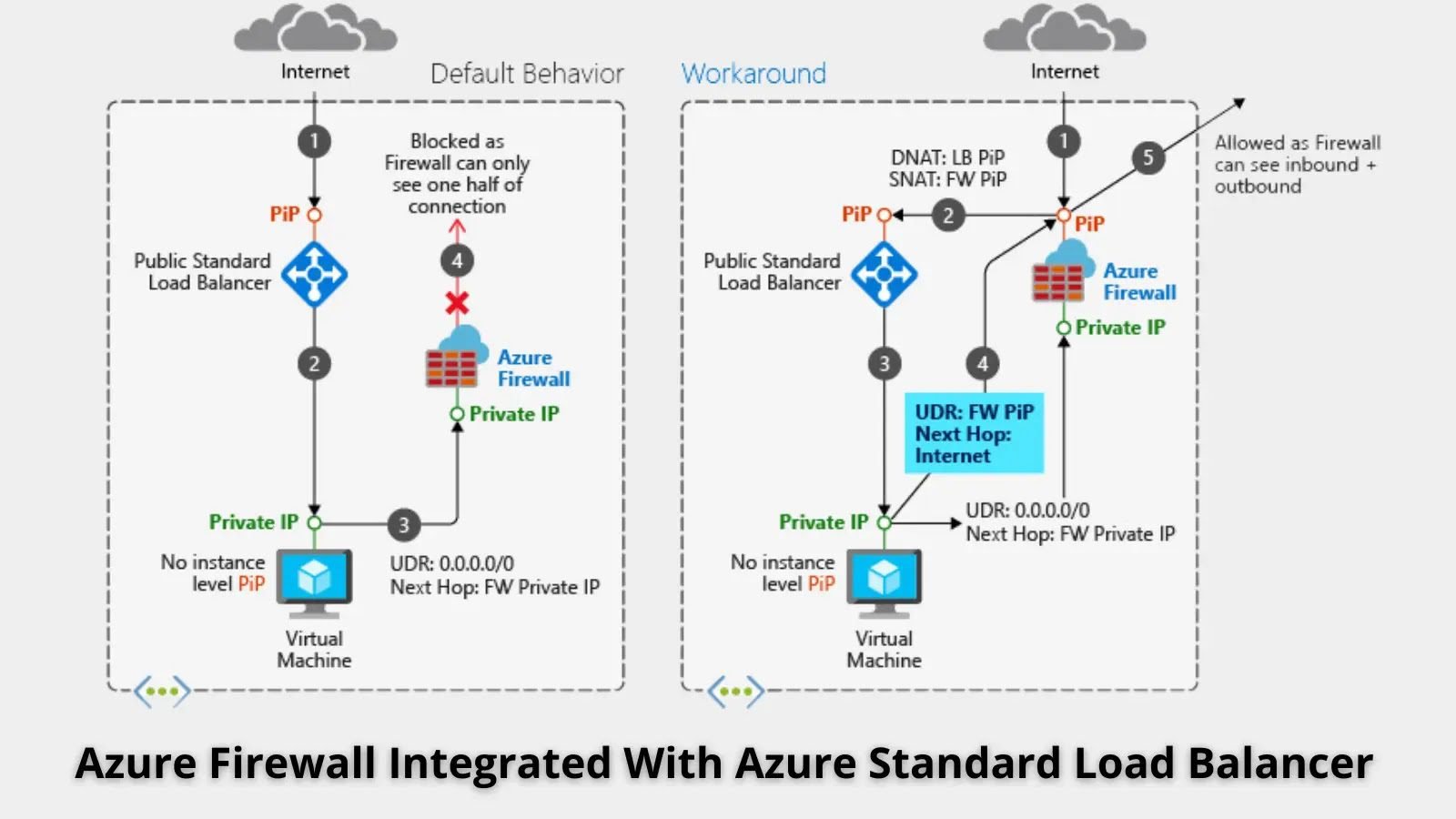
Microsoft Integrates Azure Firewall with Azure Standard Load Balancer to Boost Security Microsoft Azure has unveiled new integration capabilities between Azure Firewall and Azure Standard [...]
Effective Steps to Accelerate Cybersecurity Incident Response Modern security tools continue to evolve, improving their ability to protect organizations from cyber threats. Despite these advances, [...]
Critical Cisco ASA Flaw Allows SSH Remote Command Injection A critical vulnerability has been identified in the Cisco Adaptive Security Appliance (ASA) Software, posing a [...]
Cisco ASA & FTD VPNs Vulnerability Actively Exploited in Attacks Cisco has disclosed a critical vulnerability in its Adaptive Security Appliance (ASA) and Firepower Threat [...]
Cisco ATA 190 Telephone Adapter Flaw Exposes Devices To Remote Takeover Cisco has issued a critical security advisory concerning multiple vulnerabilities in its ATA 190 [...]