Microsoft Edge RCE Vulnerability Let Attackers Take Control of the System Remotely A critical remote code execution (RCE) vulnerability in Microsoft Edge has been discovered. [...]
New Kubernetes Vulnerability Allows Attackers to Access Clusters Remotely A critical vulnerability tracked as CVE-2024-7646, has been uncovered in the widely used ingress-nginx Kubernetes controller. [...]
Critical OpenVPN Zero-Day Flaws Affecting Millions of Endpoints Across the Globe Security researchers have uncovered four zero-day vulnerabilities within OpenVPN, the world’s leading VPN solution. [...]
Fortinet Patches Multiple Vulnerabilities Impacting FortiOS & Other Products Fortinet, a leader in cybersecurity solutions, has released patches addressing several vulnerabilities affecting its FortiOS, FortiProxy, [...]
Best Active Directory Monitoring Tools Monitoring an Active Directory (AD) involves tracking and analyzing business AD events and activity. Windows-based systems store and manage network [...]
New Threat Detection Model Detects Threats in Serverless Cloud With 0.003 False Rate Researchers have introduced a novel threat detection model designed specifically for serverless [...]
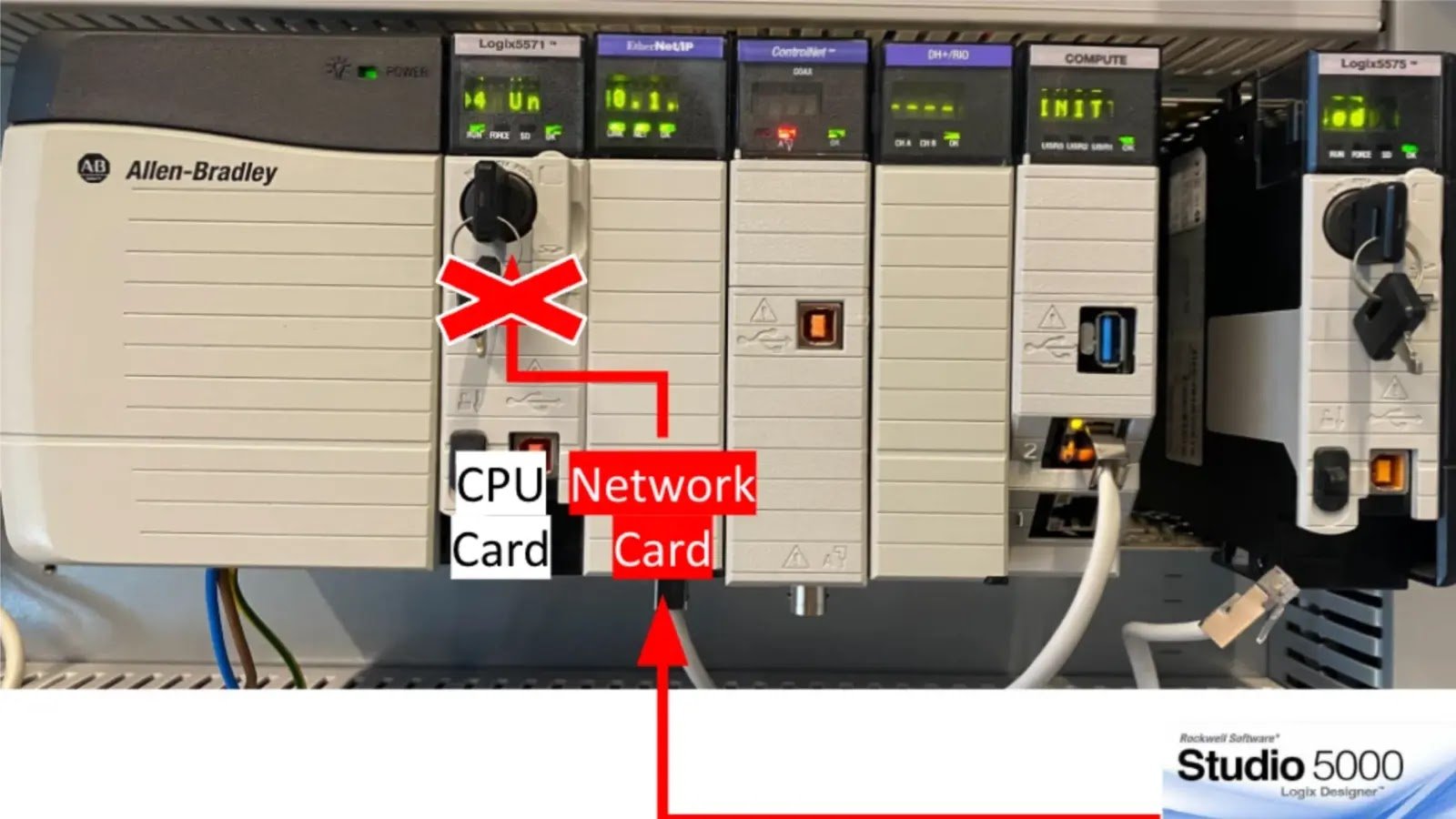
Rockwell Automation Devices Flaw Let Hackers Gain Unauthorized Access A critical security vulnerability in Rockwell Automation’s ControlLogix and GuardLogix controllers has been discovered. This vulnerability [...]
Hackers Abuse Cloudflare WARP To Hijack Cloud Services Recently, several campaigns have been observed using Cloudflare’s WARP service to target susceptible internet-facing services. The primary [...]
10 Best Linux Firewalls At present, many computers are connected via numerous networks. Monitoring all traffic and having something to filter out good and harmful [...]
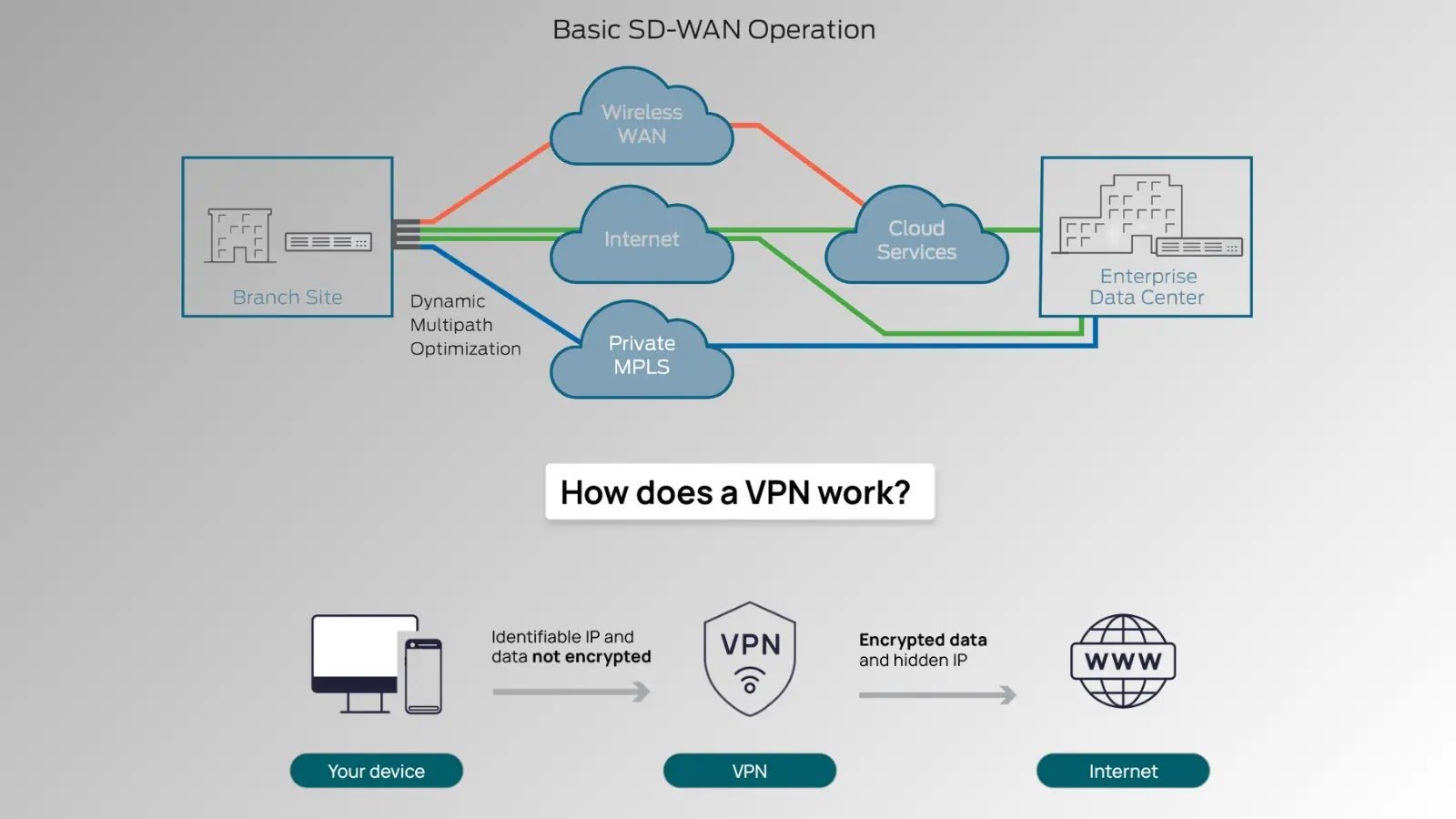
VPNs vs. SD-WAN: Which Provides Better Cybersecurity? In today’s hyper-connected world, cybersecurity is a critical concern for businesses and individuals alike. Two technologies often come up in [...]