What is the Different Between VPN and Proxy Even though they handle data in slightly different ways, virtual private networks (VPNs) and proxies both help [...]
What is a SOC Framework, Elements & Benefits of Security Operation Centre If a company is serious about cybersecurity, its beating heart will be the Security [...]
9 Essential Cybersecurity Tips For New IT Technicians Picture yourself at the helm of a company’s cyber defenses—stakes are high, and your moves are critical. [...]
Multiple Palo Alto Networks Firewall Flaws Let Attackers Cause Disruption Palo Alto Networks has recently disclosed four high-severity vulnerabilities in its firewall products. If exploited, [...]
What is Zero-Trust? – How Does It Protect Your Enterprise From Cyber Attacks? Traditional perimeter-based security measures must be upgraded in an increasingly interconnected digital [...]
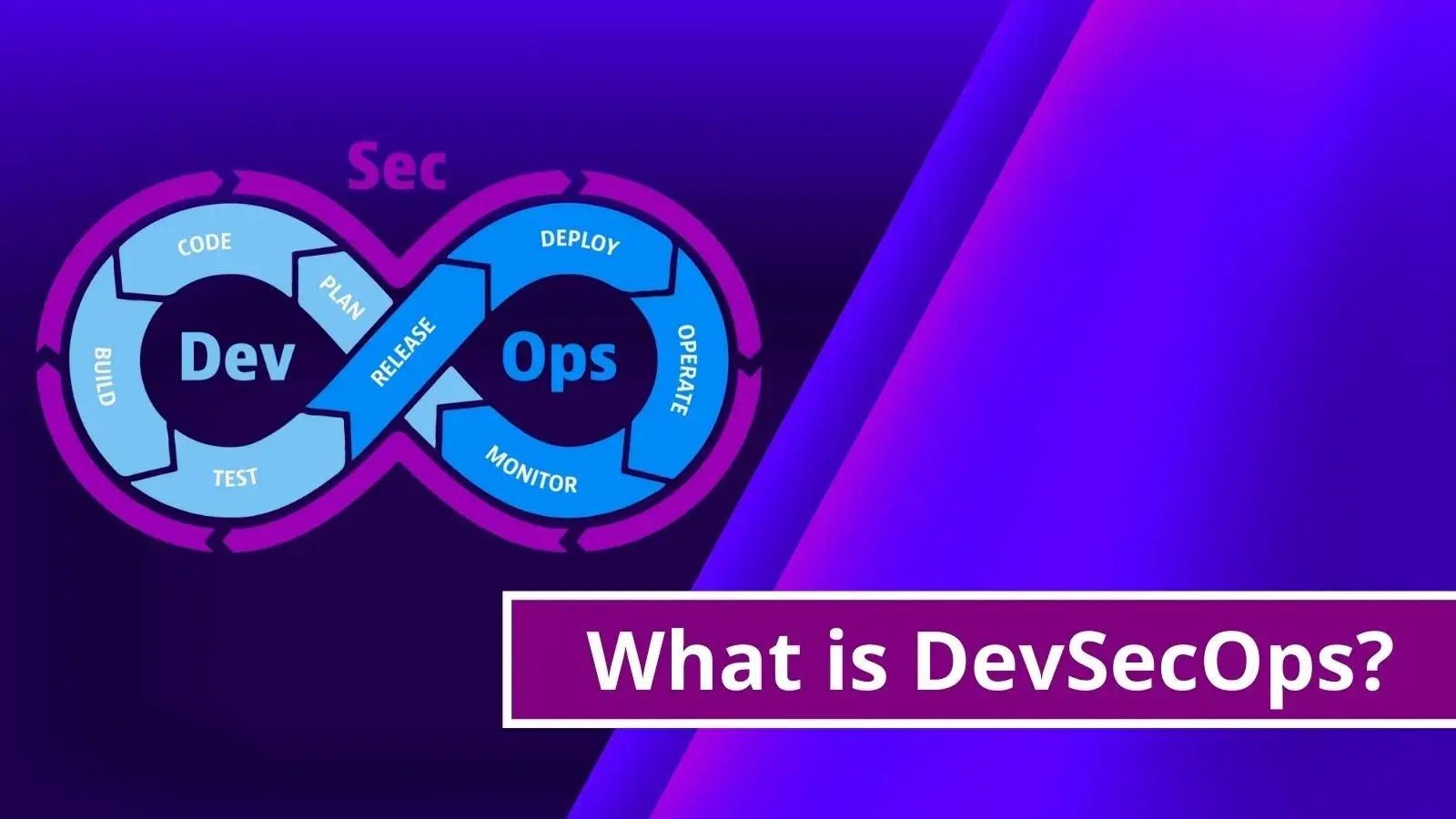
What is DevSecOps? Benefits of Automated DevOps Security DevSecOps is a methodology that integrates security as a shared responsibility throughout the entirety of the information [...]
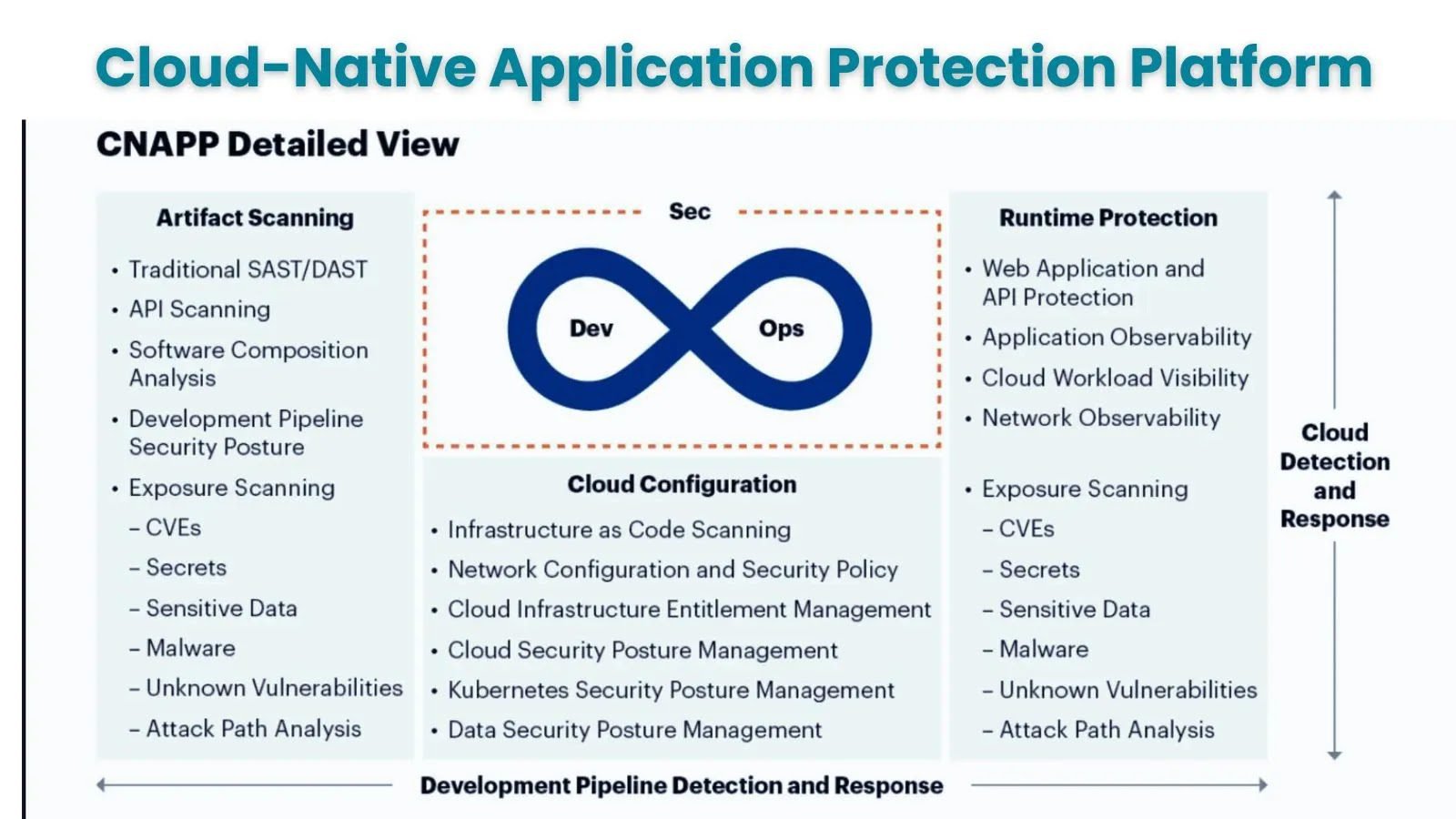
What is CNAPP ? How It Benefits for Multi-Cloud & Hybrid Infrastructure Protection Multi-cloud and hybrid infrastructures are becoming the norm among enterprises nowadays. Around [...]
NSA Releases Top 10 Cloud Security Mitigation Strategies NSA and CISA jointly released “Top 10 Cloud Security Mitigation Strategies” to advise cloud users on critical [...]
Empower Your Security and IT with Microsoft Copilot: The Ultimate AI Tool Microsoft Security Copilot, a generative AI solution for security professionals, will be generally [...]
What is Linux Firewall? How to Enable Packet Filtering With Open Source Iptables Firewall? One of the most important security tools for Linux is the [...]