What is ICMP Protocol ? – How Does ICMP Works – Guide ICMP protocol is mainly used for error handling and primarily used for network devices (routers). [...]
Critical AI Security Flaws Let Attackers Bypass Detection & Execute Remote Code Artificial Intelligence (AI) has become one of the fastest-booming technologies of this decade, with [...]
The Invisible Threat: How Phishing Undermines Business Security In an era where technology intertwines intricately with every facet of business operations, cybersecurity emerges as a [...]
What is Infrastructure as Code Security (IaC) – Best Practices Guide in 2024 Infrastructure as Code (IaC) is a popular DevOps practice that manages and [...]
The Security Dimensions of Adopting LLMs The incredible capabilities of LLM (Large Language Models) enable organizations to engage in various useful activities such as generating [...]
What is the Difference Between ISO 27001 & 27002 Compliance? – A Detailed Guide ISO 27001 and ISO 27002 are international standards that provide a [...]
How Do ISO 27001 and ISO 27002 Help to Manage the IT Security? ISO 27001 and ISO 27002 are integral in managing an organization’s IT [...]
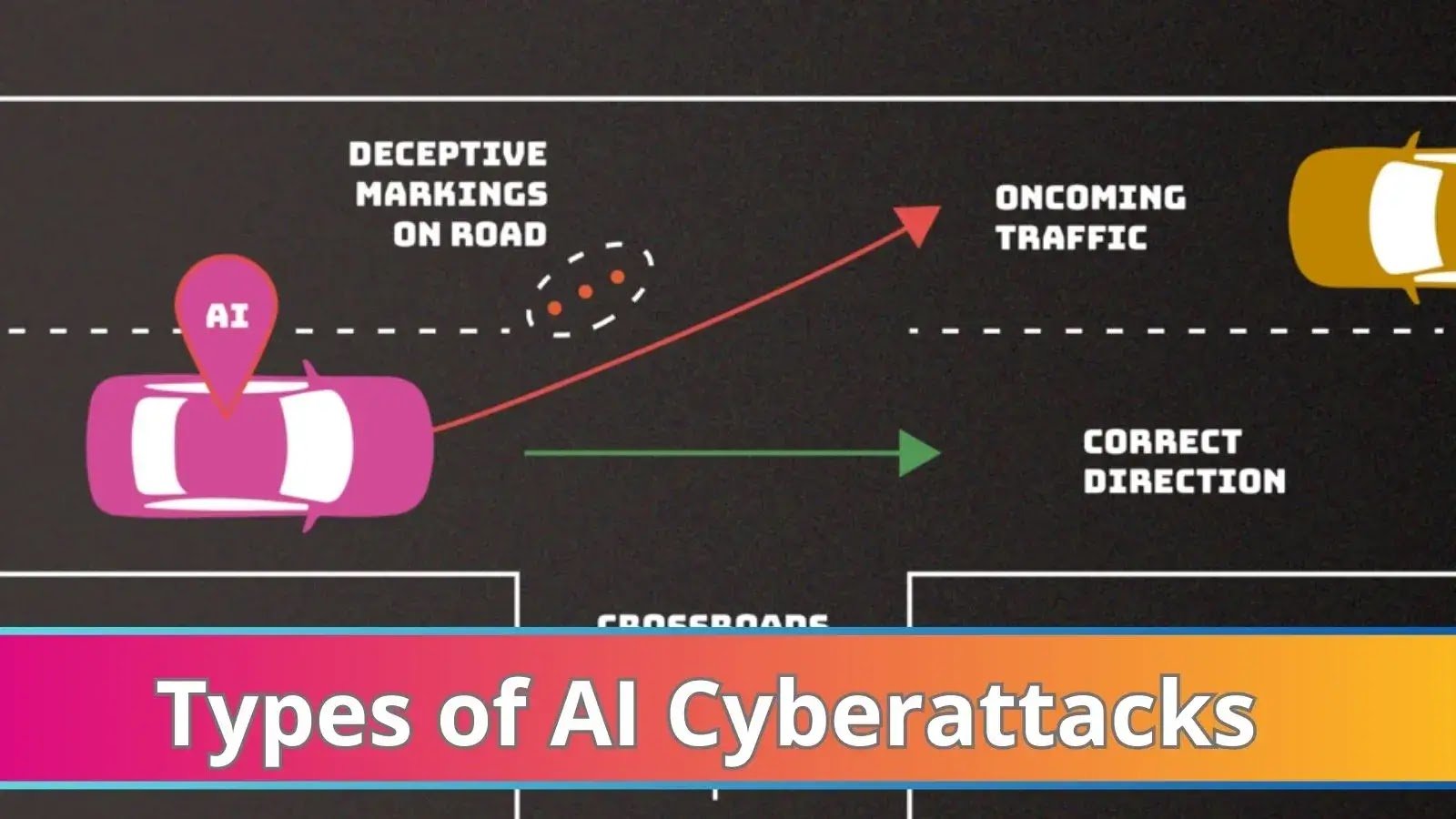
NIST Details Types of Cyberattacks that Leads to Malfunction of AI Systems Artificial intelligence (AI) systems can be purposefully tricked or even “poisoned” by attackers, [...]
Hackers Employ New Evasion Mechanisms to Bypass Security Solutions The digital landscape, once a serene meadow, has morphed into a battleground where attackers and security [...]
Sea Turtle APT Group Exploiting Known Vulnerabilities to Attack IT-service Providers To obtain access to a variety of clients’ systems and data in a single [...]