API Security Best Practices: How to Secure APIs and Improve Security Against Cyber Attack In today’s interconnected digital world, APIs (Application Programming Interfaces) have become [...]
What is a Security Operations Center (soc): What It Is and How It Works In today’s digital landscape, the Security Operations Center (SOC) stands as [...]
How Guide to Build A Secure Software Supply Chain Security: Best Practices Guide to Software Supply Chain In the digital era, secure software development is [...]
Biometric Authentication: A Complete Guide to Enhance Security and Revolutionize Modern Security In an era dominated by digital interactions, safeguarding sensitive information is paramount. Biometric [...]
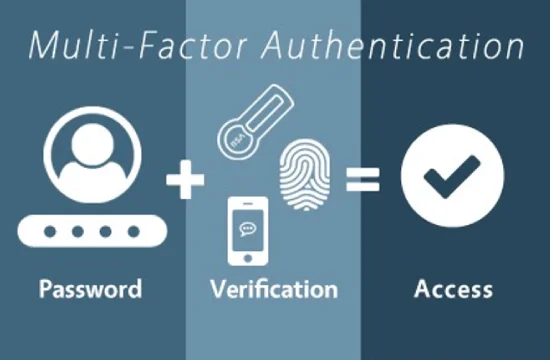
MFA: Unlocking the Importance Benefits of Multi-Factor Authentication In today’s increasingly interconnected and threat-laden digital landscape, ensuring robust cybersecurity is paramount. One of the most [...]
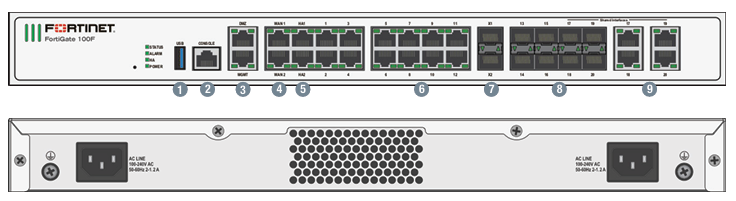
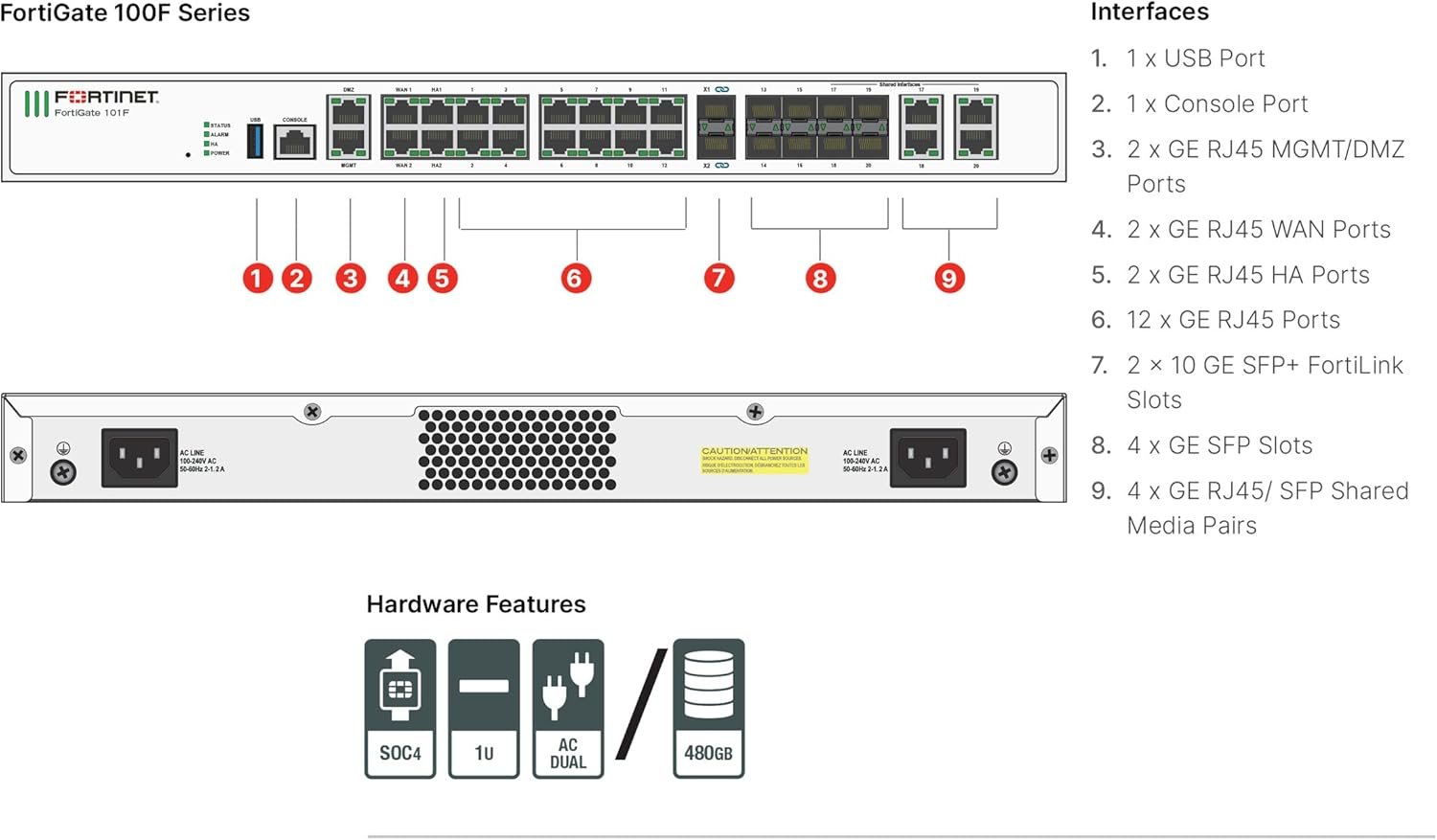
The Fortigate 100F Firewall stands as a robust solution in the realm of network and security, designed to protect organizations from an ever-evolving landscape of [...]
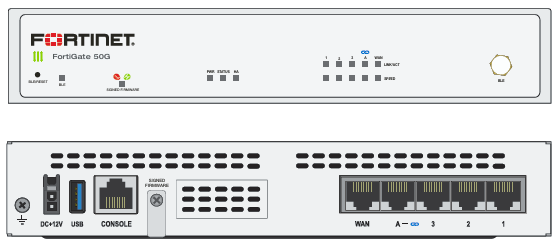
The FortiGate 50G is a next-generation firewall (NGFW) designed to provide robust security features for small to medium-sized enterprises (SMEs). It integrates advanced threat protection, [...]
The Fortigate 100F Firewall stands as a robust solution in the realm of network security, designed to protect organizations from an ever-evolving landscape of cyber [...]
Phishing Defense Strategies – Advanced Techniques for Email Security Modern phishing attacks have evolved far beyond simple deceptive emails, now incorporating AI-generated content, deepfake impersonation, [...]
Cisco Warns of IOS XR Software Vulnerability That Let Attackers Trigger DoS condition Cisco has issued security advisories for multiple vulnerabilities affecting its IOS XR [...]