Routers Under Attack – Attacks Scanning for IoT & Routers at Record High Vulnerability scanning attacks targeting internet-connected devices have surged dramatically over the past [...]
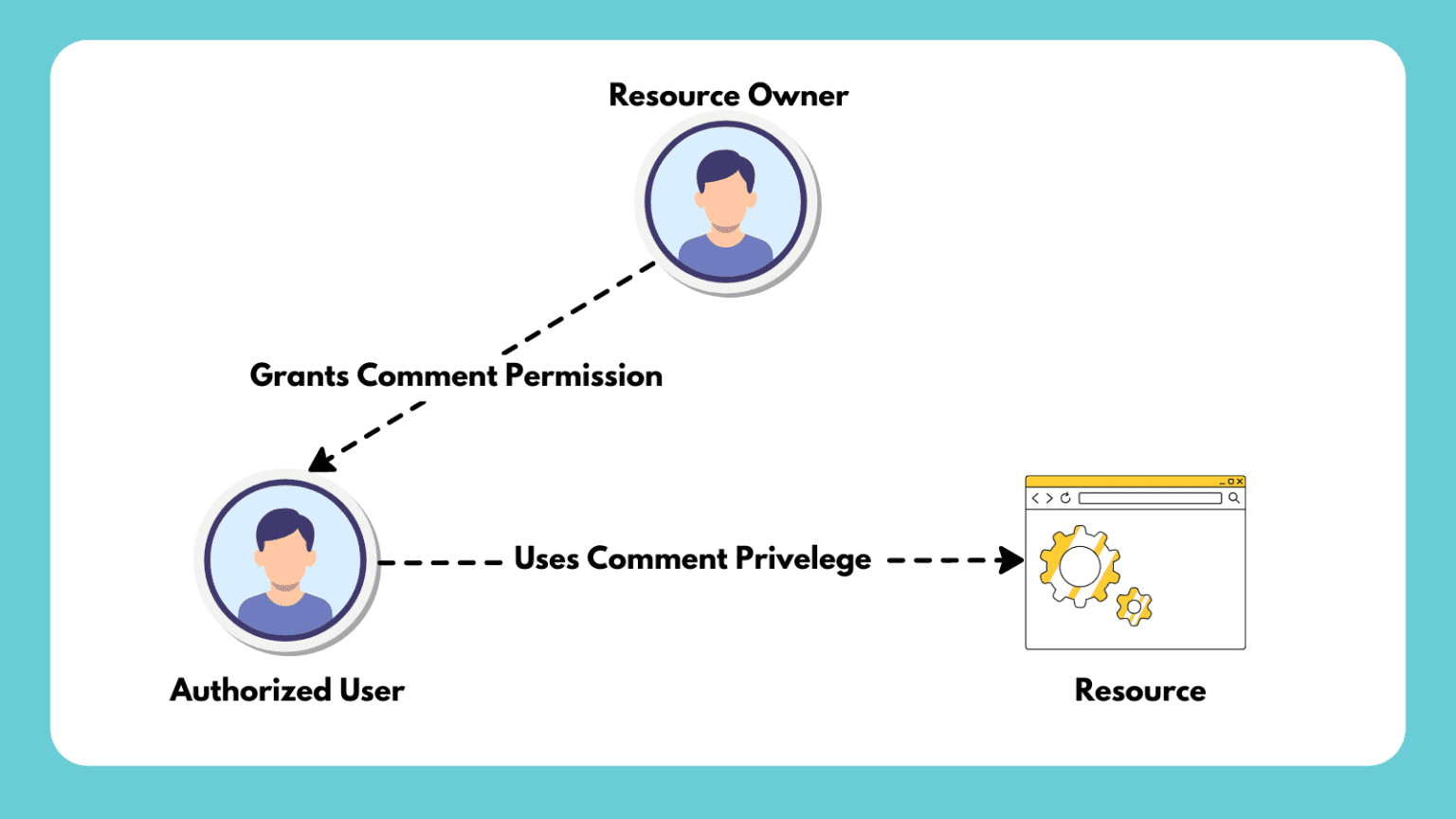
What is Authorization? Definition, Use Case & Models Authorization is a fundamental concept in information security and access management. It is crucial to determine who [...]
The Rise of AI in IT Security and Threat Prevention Artificial Intelligence (AI) has revolutionized various sectors, and its role in IT security and [...]
Zero Trust Security vs Traditional Firewalls: Which is Superior? Zero Trust Security and Traditional Firewalls represent two distinct approaches to network security, each with its [...]
Achieving 24/7 Threat Monitoring & Response for Small IT Security Teams Maintaining continuous vigilance is essential for organizations of all sizes in the face of [...]
Top 8 SSPM Tools to Secure Your SaaS Stack in 2024 The explosion of cloud-based applications, or SaaS (Software-as-a-Service), has transformed the way businesses operate. [...]
The Evolution of Firewall Technology in the Digital Age The evolution of firewall technology in the digital age has been marked by continuous adaptation and [...]
What is a Security Operations Center (SOC)? In this article, we will explore the concept of a Security Operations Center (SOC) in greater detail, including [...]
The Future of Wireless Security: Quantum Cryptography Quantum cryptography is a cutting-edge field that holds promise for revolutionizing wireless security. Unlike traditional cryptographic methods, which [...]
The Evolution of Firewall Technology: Past, Present and Future Past: Early Firewall Technology (1980s-1990s) Packet Filtering: The earliest form of firewalls involved packet filtering, where [...]